
Check Point Research Unveils New Cloud-Native Linux Malware Framework VoidLink
Introduction
Check Point Research has recently identified a groundbreaking malware framework named VoidLink, specifically designed for cloud-native Linux environments. Unlike traditional malware that focuses on individual endpoints, VoidLink is engineered to establish long-term and stealthy access to cloud infrastructures, posing significant risks to businesses and governments alike.
Shift in Target Focus
The emergence of VoidLink highlights a worrying trend among cyber attackers, who are increasingly shifting their focus from Windows systems to the Linux environments that support critical cloud services and business operations. This shift indicates a new landscape in cyber threats where the potential for stealthy, long-term attacks on vital infrastructures is amplified.
Modular Design for Flexibility
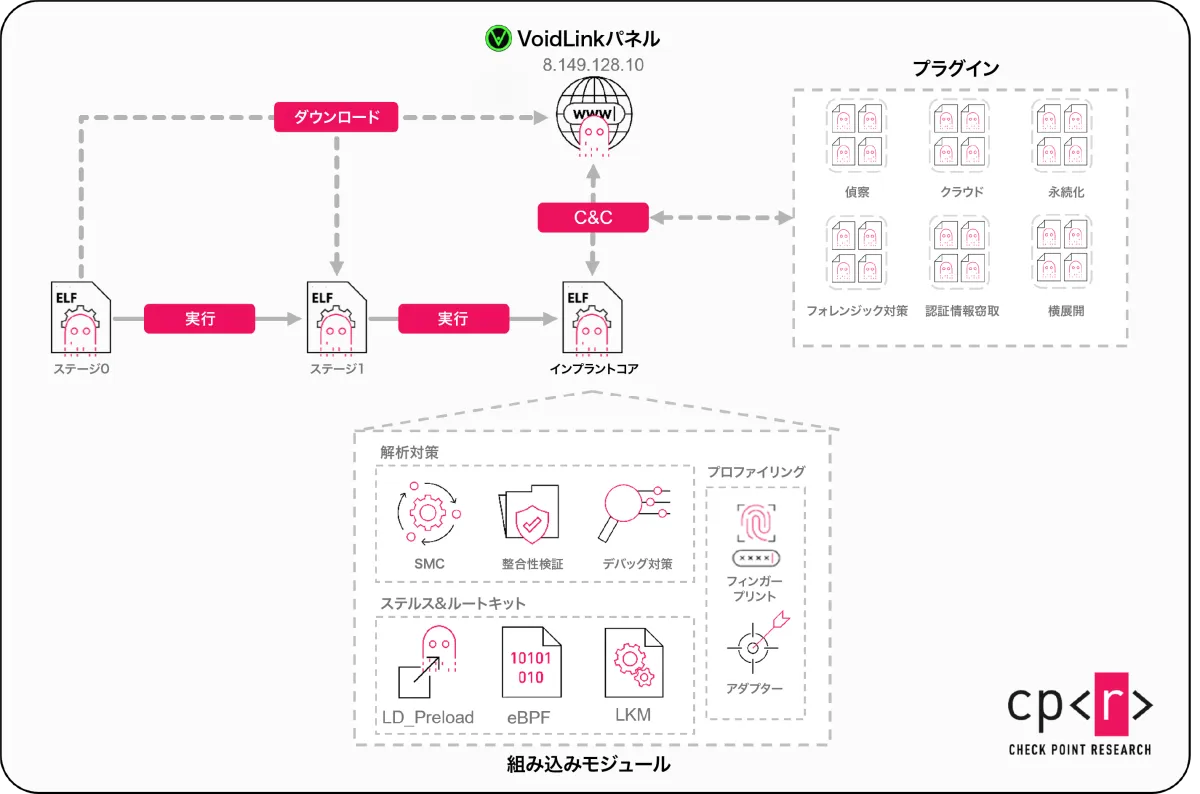
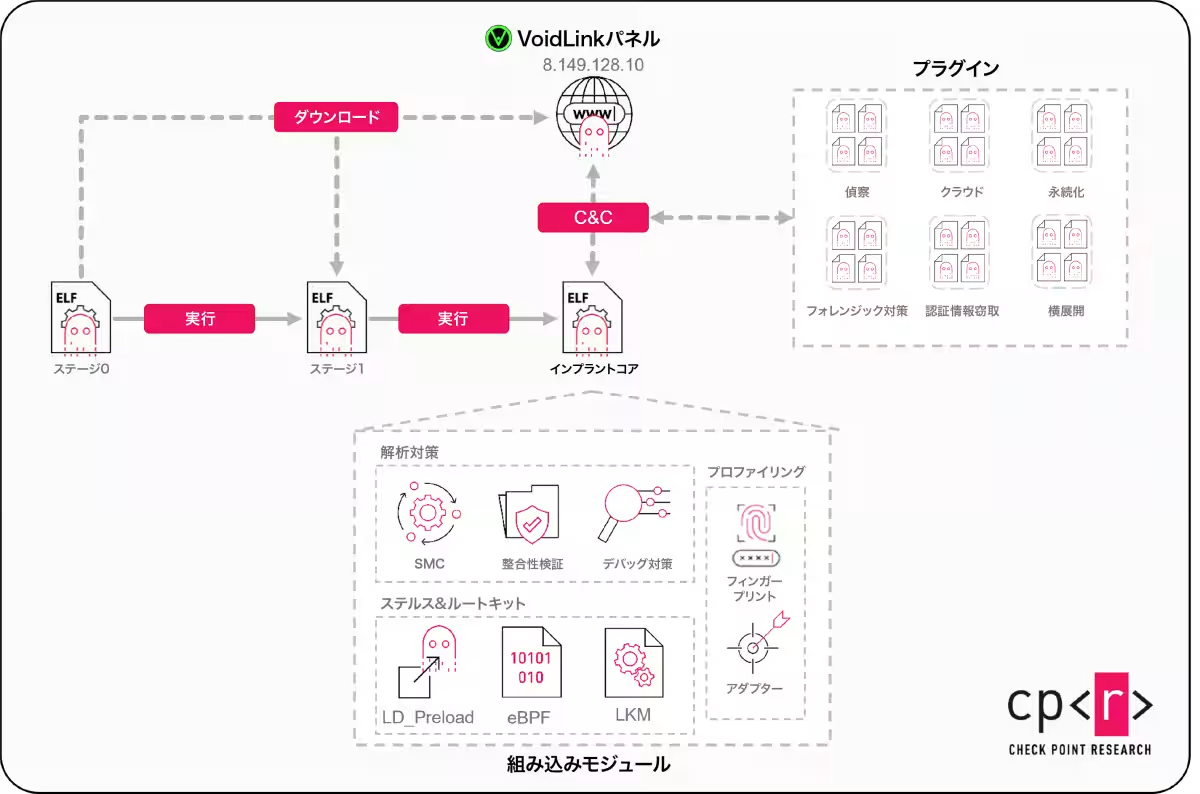
VoidLink is notable for its modular and plugin-based architecture, allowing threat actors to customize and expand their attack capabilities over time according to their objectives. This design not only provides flexibility but also enables attackers to adapt their strategies to the defensive postures of their targets. For instance, in closely monitored environments, the malware prioritizes evading detection, while in less scrutinized settings, it may operate at higher speeds.
The Role of Artificial Intelligence
One of the most striking features of VoidLink is its apparent development using artificial intelligence (AI). This is among the first instances where AI-generated malware displays advanced sophistication and rapid evolution. Traditional AI-assisted malware has often resulted in low-quality outputs; however, VoidLink represents a significant leap in how AI can facilitate the creation of complex cyber weapons quickly, reducing development time from months to just a few days.
The Nature of VoidLink
According to Check Point Research, VoidLink has not been actively deployed against victims yet, but its capabilities indicate that, once in the hands of experienced threat actors, it could be utilized to target cloud infrastructures directly. The framework is designed for long-term stealthy access, particularly focusing on compromised Linux systems, especially those operating in public cloud platforms and container environments.
Deceptive Operations: A Cloud-Centric Design
Unlike traditional malware that retrofits cloud capabilities, VoidLink is built from the ground up with cloud environments in mind. Upon deployment, the malware identifies which cloud provider it’s operating under and whether it runs in a virtual or containerized environment, adjusting its behavior accordingly. Such cloud-awareness allows attackers to blend into legitimate infrastructure quietly, making it exceedingly difficult to detect malicious activity among standard operational functions.
Features of VoidLink
VoidLink exhibits a high degree of modularity, allowing it to function not merely as a static tool but as a customizable attack platform. Operators can load, swap, or remove plugins as needed, tailoring the framework to suit specific targets. Currently, over 30 plugins have been identified, enabling a wide range of malicious activities, from stealth reconnaissance and credential harvesting to lateral movement and erasing forensic traces post-attack.
Adaptable Stealth Techniques
Another standout feature of VoidLink is its stealth design aimed at adapting to the target’s defensive environment. It evaluates security postures, recognizing deployed monitoring tools and endpoint protection technologies. If faced with robust defenses, it will engage in stealthier, slower operations; in less monitored scenarios, it will broaden its operational bandwidth. This dynamic adaptability sets VoidLink apart from conventional Linux malware.
The Rising Threat Landscape
VoidLink signifies a significant evolution in the cyber threat landscape, highlighting the shift in attackers' focus towards Linux systems, cloud infrastructures, and application deployment environments. Organizations moving critical workloads to the cloud must recognize these environments as high-value targets.
The Importance of Understanding AO AI-Driven Malware
It is suggested that VoidLink may have ties to threat actors associated with China, though precise affiliations remain unclear. The framework demonstrates a high level of technical expertise, with a synthesis of various programming languages and knowledge of Linux OS internals. What emerges from deeper analysis is that VoidLink likely stemmed from a single threat actor who leveraged AI at every stage of development—from outlining a detailed project plan and definitions of outcomes, to testing the malware and refining it efficiently.
Protecting Against VoidLink
To combat the vulnerabilities exposed by VoidLink, security teams must treat cloud-hosted Linux systems as high-value targets. Enhanced visibility into cloud workloads, application environment monitoring, and broader threat detection beyond traditional endpoints are essential steps. Organizations are urged to develop strong, prevention-first security strategies supported by real-time threat intelligence and rapid detection capabilities.
Conclusion
The identification of VoidLink not only points to the discovery of a new malware variant but underscores a broader shift in the cyber threat landscape where AI is being harnessed to speed up the development of advanced malware. A renewed focus on AI-driven threats necessitates that organizations adapt quickly, creating robust security measures to anticipate and counteract these evolving tactics. Check Point's Threat Emulation and Harmony Endpoint solutions offer comprehensive protection against such sophisticated threats. For further insights, please refer to Check Point Research's blog.
Topics Entertainment & Media)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.