
Check Point Research Confirms Lumma Malware Developers Resuming Operations
Increase in Cyber Crime Activity: Lumma's Revival
In May, Check Point Research reported that the information-stealing malware Lumma had its infrastructure significantly compromised due to a law enforcement crackdown. Despite these setbacks, the developers behind Lumma are reportedly making efforts to revive their operations.
Overview of the Situation
The shutdown of Lumma's infrastructure has certainly dealt a heavy blow to its operations. However, it appears that many of the critical components operating within Russia remain unaffected. As such, the Lumma developers are taking quick steps to rectify the situation and continue their activities, suggesting a likely return to normal operations is on the horizon.
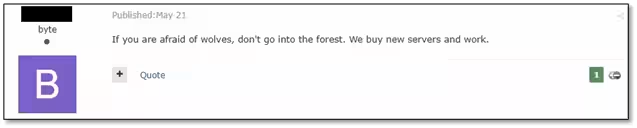
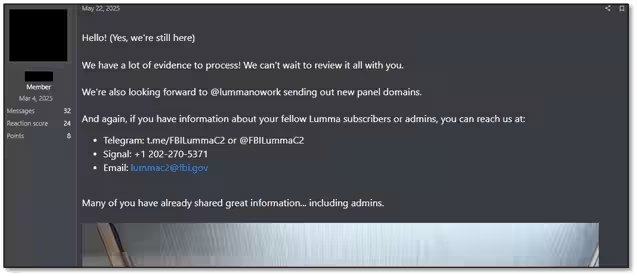
In light of the crackdown, the reputation of the Lumma infostealer has been hurt considerably, suggesting that the recovery of trust among its users and affiliates may pose a more significant challenge than addressing technical issues. On May 21, a joint operation was announced involving Europol, the FBI, and Microsoft to dismantle the operations of Lumma, marking it as one of the most pervasive information-stealing malware currently being distributed as a service.
The Arrest Operation
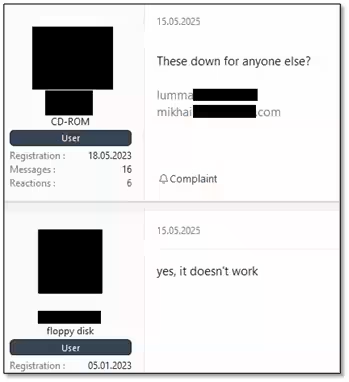
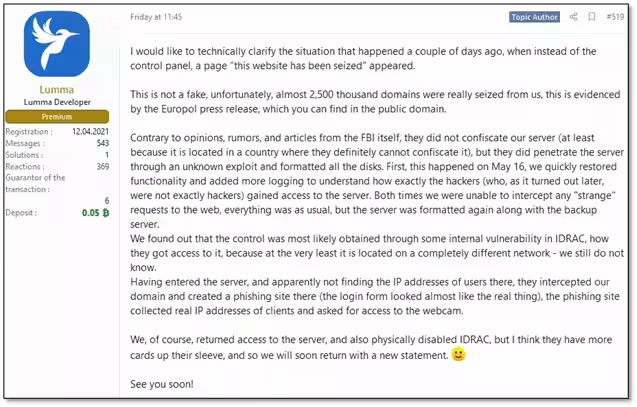
According to sources involved in the takedown operations on the dark web, the campaign began on May 15, with Lumma’s clients reporting inaccessibility to the malware's control servers and admin dashboards. The developers officially acknowledged this issue on May 23, admitting that around approximately 2,500 of their domains had been seized or deleted by law enforcement.
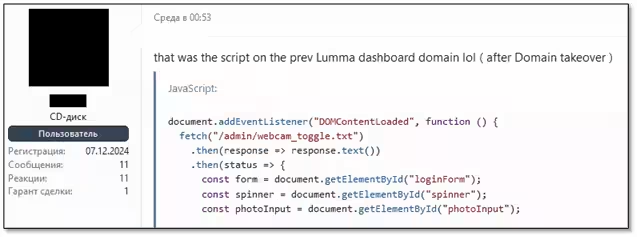
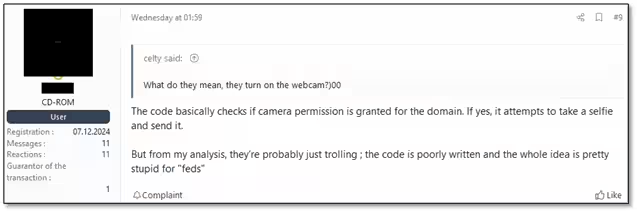
Interestingly, while the authorities were unable to seize Lumma's main servers due to geographical constraints, they managed to exploit vulnerabilities in the Integrated Dell Remote Access Controller (iDRAC) to infiltrate the server, leading to the deletion of server contents including backups. Though the Lumma developers claimed they did not record the clients' IP addresses, authorities were reportedly employing fake login pages to collect user credentials and digital footprints. They even introduced JavaScript code aimed at accessing users' webcams under the pretense of taking pictures.
Future Outlook
Despite the significant damages inflicted by this operation, opinions are split regarding Lumma's future within cybercrime forums. Some speculate that they may shut down completely or at least withdraw from public view, moving towards a more covert marketing strategy. Conversely, others hold the view that this takedown will have no long-term repercussions.
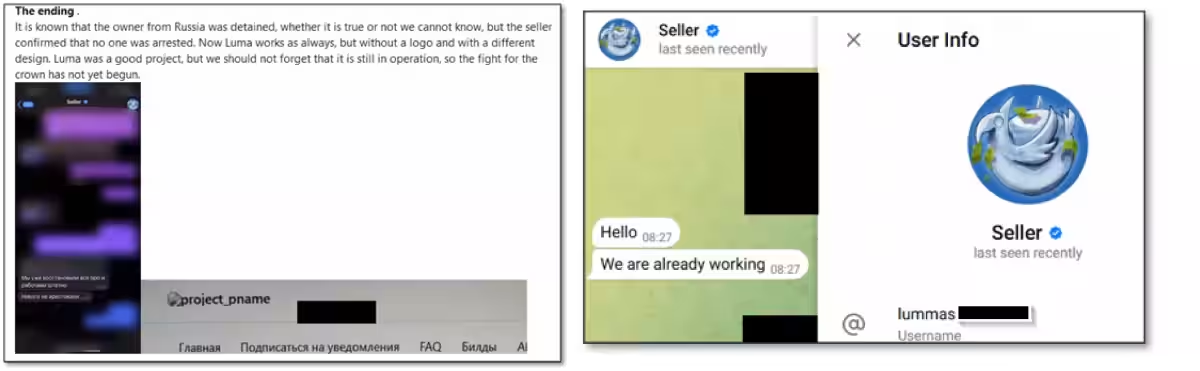
Reportedly, developers claim to have resumed their operations, as some cybercriminals have begun sharing communications in Telegram groups where they assert that Lumma’s operations are fully functional again without any arrests among the team. When investigated further, it appears that servers still linked to Lumma in Russia remain unaffected.
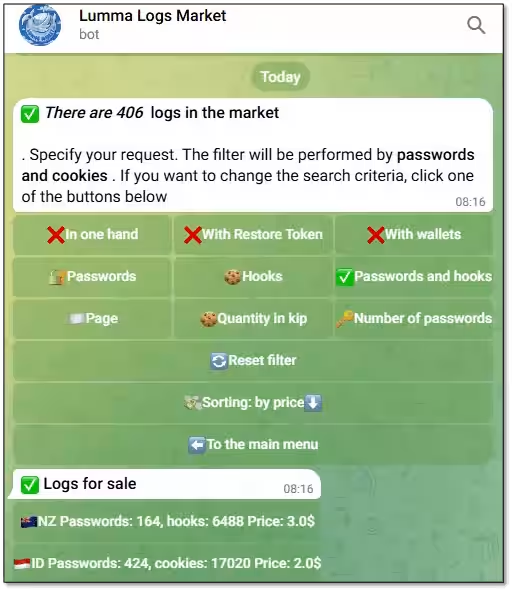
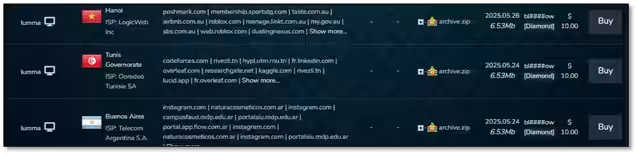
In fact, data stolen from compromised computers continues to circulate in online markets. Just two days after the crackdown, a Telegram bot was found offering logs of stolen credentials from 41 countries, with the total number of logs reaching 406 by May 29, indicating a steady increase. Furthermore, a centralized shop focusing on the Russian market still had listings containing data from Lumma-infected computers even post-operation.
Conclusion
While the crackdown against Lumma has been noteworthy, Check Point Research is observing the developers' concerted efforts to reinstate their operations. The real concern lies not only in the technical aspects but also in the reputational damage inflicted upon the Lumma brand. The psychological warfare employed by law enforcement may have sowed seeds of distrust among affiliates and potential users, insurmountable as has been seen in previous similar scenarios.
This article is based on a blog post released on May 29, 2025, in U.S. time, by Check Point Research.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.