
Check Point Analysis: Instagram Map Feature Raises Cybersecurity Risks
Check Point Analysis of Instagram's New Map Feature
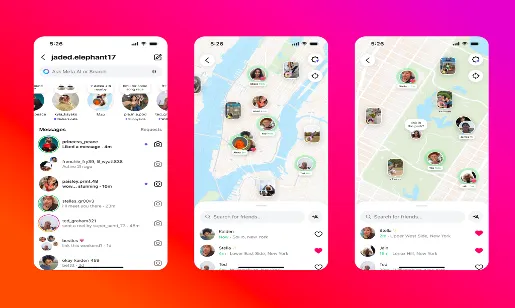
In August 2023, Meta released a new feature on Instagram called the "Instagram Map," touted as a fun way to check friends' locations and discover common spots. However, this introduction has raised significant concerns about the security implications associated with location sharing. Check Point Software Technologies, a pioneer in cybersecurity solutions, has conducted a thorough analysis to shed light on potential digital and physical risks tied to activating this new map function.
How Instagram's Map Function Collects Location Data
When users enable the Instagram Map function, it collects and saves two primary types of location data:
1. Launch-Based Location Logging: Each time a user opens or restarts the Instagram app, their latest location is logged.
2. Content-Based Location Data: Posts, stories, and reels that are tagged with locations are indexed and linked to the user's account profile.
Through this mechanism, even if a user does not utilize continuous GPS tracking, a history of their movements with timestamps can be established. By repeatedly checking in at the same coordinates over time, the app can accurately infer a user's home or workplace locations, travel patterns, and frequently visited places.
This data is stored centrally on Meta's servers, which supports not only Instagram but also Facebook, Messenger, and other Meta services. Notably, Meta does not specify how long it retains this data. Instead, it uses vague phrasing indicating it is retained as long as necessary for purposes like service enhancement, compliance, and commercial use. Unlike security-focused location services, this data is not end-to-end encrypted. Such centralized data management makes it an attractive target for cybercriminals.
The Double Threat: Physical and Digital Risks
The risks associated with location sharing can largely be categorized into physical and digital threats. However, a critical concern lies in their potential overlap. Physically, revealing one’s location can lead to stalking, harassment, or unwanted encounters. It can enable criminals to exploit tagged locations to target empty homes for burglary. Vulnerabilities increase significantly for minors, as public location sharing can allow predators to identify, track, or approach them.
On the digital side, location data serves as a powerful profiling tool. Within Meta’s advertising platform, this information can be integrated with browsing history, purchase records, and demographic details, creating highly specific target groups. While this can improve advertisement relevance, it also opens opportunities for malicious targeting through disinformation or phishing attacks. Attackers can deduce political beliefs, faith, or health conditions based on location patterns, leveraging this data to create compelling and manipulative content tailored to individuals. In this way, what is beneficial for marketing can simultaneously help attackers identify optimal times and methods for targeting users.
Comparing Instagram Map with Other Location Sharing Tools
At first glance, Instagram Map shares similarities with renowned services like Apple’s ‘Find My’ and Snapchat’s Snap Map. However, their design goals, privacy models, and associated risk profiles markedly diverge.
Apple's 'Find My' feature is widely acknowledged as the most secure consumer-oriented location sharing tool. It uses end-to-end encryption, ensuring location data is encrypted on the sender's device, only being decryptable on the intended recipient's device. Even on Apple servers, this data remains unreadable during transmission or storage. Access is restricted through exchange of encrypted keys linked to authorized contacts. This feature aims to secure individuals and recover lost devices, not for social engagement or advertising. Thus, it lacks commercial motivation to store or process location data beyond necessary parameters.
Snap Map, while also opt-in, has seen incidents of misuse, including stalking and harassment cases. Even with privacy settings like Ghost Mode, malicious actors have exploited Snap Map to identify users and initiate direct confrontations.
Instagram Map, however, differs fundamentally in three significant manners:
1. Integration within Meta's Ecosystem: This feature integrates location information into Meta's broader ecosystem, allowing for historical data association with a vast array of personal information.
2. Commercial Motivation: Being an advertising-driven platform, the collection, analysis, and retention of location data are fueled by commercial interests.
3. Recent Data Breaches: Over the past six months, Meta has experienced multiple significant data breaches, making this map feature a particularly attractive target for attackers seeking detailed geographic user profiles.
Is Instagram Map a "Threat Map"?
From a threat intelligence standpoint, Instagram Map has already caught the attention of malicious actors. Within days of its release, discussions on underground forums about reverse-engineering the application programming interfaces (APIs) to understand the location data handling mechanism emerged. Furthermore, techniques for collecting mass user coordinates and correlating them with open-source information came into focus, alongside strategies for de-anonymizing individuals.
These methods are not unprecedented; they reflect techniques seen in past exploitations, such as Snapchat exploit cases, intrusions utilizing Instagram and Facebook geotagging, and the Strava heatmap leak revealing military site locations.
The rapid escalation of such activities signals that attackers recognize the high value of location data. Here, the risk extends beyond simply pinpointing someone's current location. The intertwining of location information with other accessible data poses a danger of creating detailed and exploitative personal profiles.
User Mitigation Strategies
Awareness of these risks forms the first line of defense. Yet, it is also a significantly overlooked aspect by many users. Many Instagram users might not fully grasp that enabling location sharing could make their movement patterns accessible to unknown individuals. Often, follower lists remain unchecked, and settings frequently remain at default. Additionally, social pressures could lead users to opt-in without considering the risks involved, creating a vulnerability that turns social functionalities into potential security threats.
To mitigate these risks, the following steps are recommended:
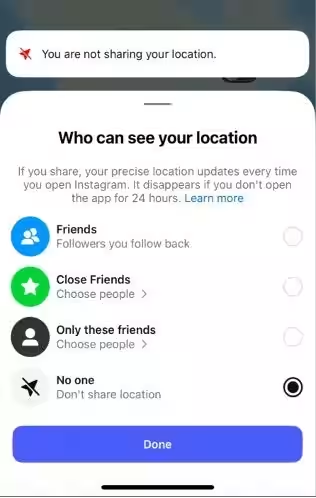
1. Disable Location Sharing: Navigate to messages → Map → Settings and switch location sharing to "private."
2. Limit Device Permissions: Adjust the privacy settings on smartphones to allow Instagram access to location only while using the app or disable entirely.
3. Regularly Review Followers: Remove followers who are unknown or untrusted.
4. Parental Monitoring: For minors, guardians should utilize Instagram’s Family Center to oversee location settings and restrict sharing to trusted contacts.
5. Contextual Sharing: If sharing location for a specific reason, immediately disable it afterward to prevent the accumulation of long-term location histories.
This analysis has been derived from a blog released on August 13, 2025, (U.S. time) to provide insights into the privacy risks associated with Instagram Map.
About Check Point
Check Point Software Technologies (https://www.checkpoint.com/) is a leading provider of digital trust, protecting over 100,000 organizations worldwide through AI-driven cybersecurity solutions. Its Infinity Platform and open-garden ecosystem offer industry-leading security effectiveness while reducing risk in a prevention-first approach. The architecture centers around SASE-powered hybrid mesh networks, integrating management across on-premises, cloud, and workspace environments, providing flexibility, simplicity, and scalability to enterprises and service providers. Check Point Software Technologies Japan, wholly owned subsidiary, was established on October 1, 1997, with its headquarters in Minato-ku, Tokyo.
Legal Disclaimer Regarding Forward-Looking Statements
This press release contains forward-looking statements regarding future events or our future financial or operational performance. These statements reflect our expectations of future growth, expansion of industry leadership, increasing shareholder value, and delivering industry-leading cybersecurity platforms to global clients. However, our predictions and beliefs in these areas may not materialize, and actual outcomes may vary significantly due to risks or uncertainties. Such risks include our ability to continue developing platform functionalities and solutions, customer acceptance and purchase of our existing and new solutions, ongoing development of the IT security market, competition from other products and services, general market conditions, political, economic, and management circumstances, and impacts from acts of terror or war. Detailed discussions of these risks can be found in our filings with the U.S. Securities and Exchange Commission, including our annual report (Form 20-F) submitted on April 2, 2024. Check Point is not obligated to update any forward-looking statements unless legally required to do so.
Topics Entertainment & Media)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.