
Check Point Research Warns About Malware Targeting Minecraft Players
Rising Cyber Threats in the Minecraft Community
Check Point Research (CPR), a division of Check Point Software Technologies, has recently uncovered a sophisticated malware campaign targeting the vibrant community of Minecraft players. The campaign employs malicious mods disguised as legitimate Minecraft modifications, raising serious concerns about cybersecurity in one of the world’s most popular video games.
Key Discoveries
The CPR team detected a multi-layered malware campaign that utilizes fake Minecraft mods, which are distributed across various platforms, primarily GitHub. These insidiously crafted mods are designed to lure unsuspecting players into downloading malicious software, leading to potential data breaches and unauthorized access to personal information.
Three-Peak Infection Chain
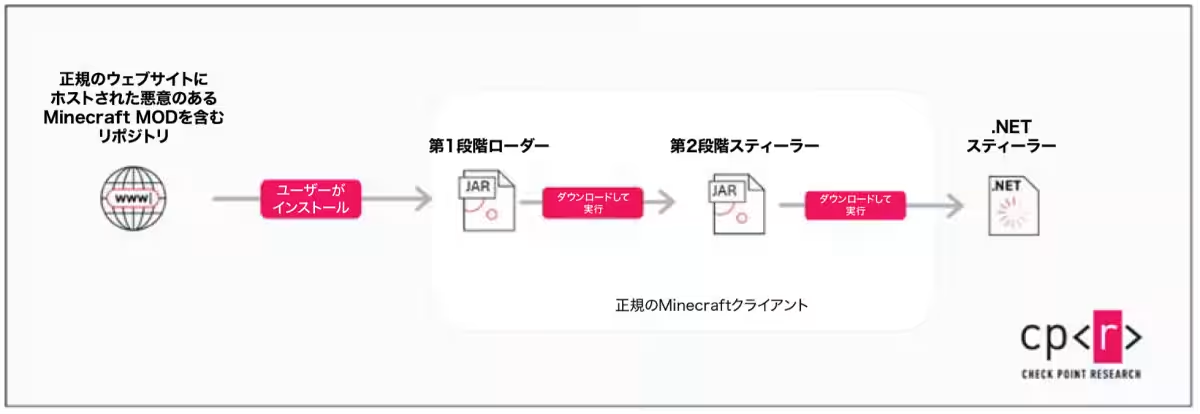
The attack consists of a three-step infection process:
1. Java Downloader: Initially, a seemingly harmless Java downloader is presented to the player. Once downloaded, it bypasses traditional security measures.
2. Information Stealer: Following the downloader, a two-stage information-stealing malware kicks in, aimed at harvesting sensitive user data.
3. Advanced Stealer: In the final stage, a sophisticated stealer is deployed, capable of collecting passwords, cryptocurrency wallet information, and other crucial data.
Possible Involvement of Russian Threat Actors
Analysis of the malware's behavior and comments in the code suggest possible involvement from Russian-speaking threat actors, as observed through UTC+3 timezone activity patterns and Russian language scripts included in certain files.
The Popularity and Risk of Minecraft Mods
Minecraft stands as a titan in the gaming industry, with sales surpassing 300 million copies and an active player base exceeding 200 million monthly. One of the game’s major attractions is its modding community, which allows users to create custom mods. These modifications can enhance gameplay, resolve bugs, and introduce new content, nurturing an innovative ecosystem.
Despite its diverse and creative community, the game's demographic poses unique security challenges. Approximately 65% of Minecraft players are under 21, a group often less aware of cybersecurity risks and more susceptible to malicious attacks, making them prime targets for cybercriminals.
The ‘Stargazers Ghost Network’ Campaign
In May 2025, CPR commenced tracking a network dubbed the ‘Stargazers Ghost Network’. This operation, first identified in July 2024, is run by employing a Distribution-as-a-Service (DaaS) model, utilizing multiple GitHub accounts to disseminate harmful links and malware extensively.
Within this framework, malware infiltrates users’ machines unnoticed, masquerading as popular mods known for facilitation of cheats and automation tools. In order for the attack to be effective, Minecraft must already be pre-installed on the victim's device, allowing attackers to pinpoint vulnerable players.
Tracking Malicious GitHub Repositories
Since March 2025, Check Point has been tracking harmful GitHub repositories purporting to offer legitimate Minecraft mods. While these repositories appear to be genuine and are aimed at curious players, they harbor small-scale Java-based malware that secretly installs additional malicious software into the victim's device.
These files often mimic popular cheating tools popularized within the Minecraft community, increasing their likelihood of evading user and security solution detection.
Understanding the Attack Mechanism
The infection begins when a player unwittingly downloads what seems to be an innocuous mod from GitHub. Upon launch, the mod checks whether it is functioning in a virtual environment. Security professionals typically use such environments to analyze malware safely. Upon confirming its operation outside of the virtual space, the next stages of the attack ensue.
Once the malicious mod runs, it downloads a secondary payload designed to extract sensitive information. Following this, more advanced spyware tools are deployed capable of collecting login credentials from browsers, cryptocurrency wallets, as well as apps like Discord, Steam, and Telegram. Furthermore, the spyware can take screenshots and gather intricate details about the affected system.
Stolen data is systematically compiled and stealthily transmitted through platforms like Discord, cleverly disguising malicious traffic within legitimate communications. Based on insights gathered, CPR estimates that over 1,500 devices might have fallen victim to this campaign.
Emerging Threats in the Gaming Community
This unsettling campaign underscores how even seemingly secure digital platforms can fall prey to cybercriminal activities. By disguising malware within Minecraft mods, attackers have successfully targeted an eager yet unprotected user base through Java-based multi-stage infections. These files frequently appear harmless, thus eluding conventional protective measures, placing all Minecraft players at risk.
As the gaming community expands, malicious attackers are drawn in by the potential for profit amid these vulnerabilities. The findings emphasize the critical need for cautious deliberation before downloading third-party content, regardless of its source’s appearance.
Recommendations for Users and Gamers
- - Download mods only from verified and trusted sources.
- - Be cautious with tools claiming to offer cheats or hacks.
- - Keep antivirus software and system software updated at all times.
- - Be wary of tools that promise unusually favorable conditions, as they may harbor risks.
Check Point’s Threat Emulation and Harmony Endpoint solutions provide comprehensive protection against the methods and malware employed in this campaign, ensuring safety for both users and organizations.
For technical details, the full investigative report is available here.
About Check Point Research
Check Point Research provides the latest cyber threat intelligence for customers and the broader cyber threat community. The team of over 100 analysts and researchers works diligently to deter hackers and enhance protective measures within Check Point’s products, utilizing global data on cyber attacks stored within ThreatCloud AI.
For more information, visit the Check Point website and explore our resources through various platforms.
About Check Point Software Technologies
Check Point Software Technologies is a leading provider of cyber security solutions dedicated to safeguarding organizations globally through AI-driven security measures. The company’s Infinity Architecture integrates management for on-premises, cloud, and workspace environments, offering flexibility and simplicity while reducing risk. Its Japanese subsidiary was established in October 1997, with headquarters in Tokyo.
For inquiries, please reach out to the Check Point PR office.
Topics Entertainment & Media)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.