

Check Point Research Uncovers Advanced Phishing Campaign Targeting European Diplomatic Institutions
Recent Cyber Threat: APT29's Phishing Campaign
Check Point Research (CPR), a pioneering force in cybersecurity solutions, reveals that the threat group known as APT29, which is believed to have ties to Russia, has launched a new and sophisticated phishing campaign targeting various diplomatic institutions across Europe. Known for its involvement in large-scale attacks such as the 2019 SolarWinds supply chain incident, APT29's latest tactics are causing significant concern among security experts.
Overview of the Campaign
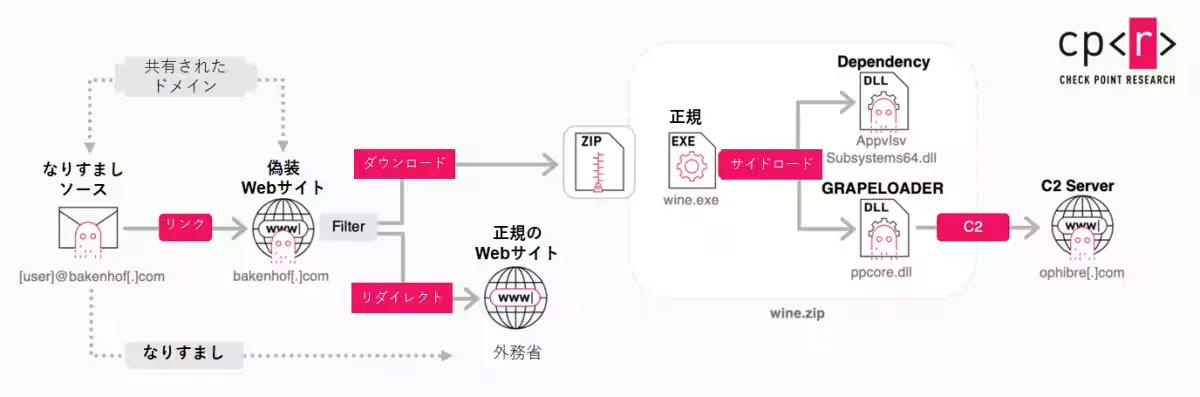
The CPR report highlights that APT29 is employing advanced phishing techniques that primarily aim at European governmental and diplomatic entities. This latest wave of attacks appears to be a continuation of earlier campaigns that utilized backdoor malware known as Wineloader. The attackers are impersonating a prominent European nation's foreign ministry, disseminating fake invitations to diplomatic events, including wine tastings, as a guise.
During this campaign, the phishing emails contain links that prompt recipients to download two types of malicious backdoor malware: Grapeloader and a new variant of Wineloader. The detailed analysis suggests that these malware types represent a significant evolution in the operational tactics of APT29.
APT29: The Adaptable Threat Actor
Also referred to as Midnight Blizzard or Cozy Bear, APT29 has once again demonstrated its capabilities through a series of targeted phishing attacks that commenced in January 2025. These attacks are reminiscent of previous efforts where advanced strategies and methodologies, or TTPs (Tactics, Techniques, and Procedures), were employed against European governmental agencies.
The threat group is infamous for targeting well-known organizations, including government agencies and think tanks. Their operations span various attack vectors, from targeted phishing techniques to extensive supply chain intrusions, frequently leveraging custom-made malware tailored to the needs of their campaigns.
Impersonating Diplomatic Institutions
APT29's recent phishing endeavors have involved impersonating a foreign ministry of a key European country. Emails that appear legitimate are sent under the pretense of inviting recipients to wine-tasting events. This phishing campaign is concentrated on European diplomatic agencies, including embassies outside the EU. Each email contains malicious links designed to either download Grapeloader malware or redirect users to fraudulent websites masquerading as official foreign ministry pages.
Through investigations, several variants of Grapeloader and a new subform of Wineloader were uncovered, suggesting a notable connection between the compile time of this Wineloader variant and the new Grapeloader. This correlation implies that the Wineloader variant was introduced in the later phases of the attack sequence. Such developments underscore the evolving tactics being employed by APT29, showcasing how the group manipulates trusted institutions to deploy sophisticated malware against unsuspecting targets.
The Mechanics of the Phishing Emails
Numerous emails impersonating officials within a foreign ministry were discovered, all containing malicious links. These links, when clicked, would lead to the download of a file named `wine.zip`, representing the next phase of the attack. The domains hosting these links were designed to mimic the sender's official domain closely.
Additionally, the servers hosing these malicious links seem to implement sufficient defenses against scanning and automated analysis tools. Notably, the harmful downloads are executed only under specific conditions, including particular timeframes or geographical locales, adding an additional layer of sophistication to the campaign.
Conclusion
The latest targeted phishing attacks associated with APT29 shine a light on the evolving and adaptive nature of cyber threats faced by governments and diplomatic entities. The emergence of Grapeloader, alongside a new variant of Wineloader, points to the ongoing progression of malware capabilities. These developments present critical challenges for the detection and prevention of cyberattacks, as they demonstrate advanced stealth and evasion techniques.
Check Point's Threat Emulation and Harmony Endpoint technologies are designed to identify malicious behaviors proactively before they impact networks, protecting organizations from threats like those discussed here. By detecting unknown threats and zero-day vulnerabilities while enabling quick access to secure versions of files, this proactive approach facilitates rapid access to safe content and effective identification and management of potential risks, ultimately strengthening security and maintaining network integrity.
For further details on APT29's recent campaigns, refer to Check Point Research's comprehensive report.
About Check Point Research
Check Point Research provides the latest cyber threat intelligence to Check Point customers and the global threat information community. With over a hundred analysts and researchers, to ward off hackers and contribute to the effectiveness of security features integrated into their products, they remain vigilant in the ongoing fight against cyber insecurity.
To further explore Check Point’s innovative cybersecurity solutions and understand their impact, visit Check Point’s official website.

Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.