
Understanding Ransomware Trends for Q2 2025: AI Integration and the Rise of Cartels
Ransomware Trends for Q2 2025: A Deep Dive into the Evolving Landscape
In its latest report, Check Point Research has provided insights into the rapidly changing world of ransomware threats as observed in the second quarter of 2025 (April - June). Notably, the ransomware ecosystem is undergoing profound transformations, influenced by AI advancements, the emergence of cartels, plummeting payment rates, and increasingly sophisticated tactics from cybercriminals.
Key Highlights from the Q2 2025 Ransomware Report
Fragmentation of RaaS Groups
A significant trend observed in Q2 2025 is the fragmentation of Ransomware-as-a-Service (RaaS) groups. A number of prominent ransomware organizations have vanished, leaving behind a more decentralized ecosystem. This fragmentation complicates tracking and combating ransomware efforts, as new actors with agile methodologies emerge.
Decrease in Public Threats
This quarter saw a notable reduction in the number of publicly named targets on data leak sites. This change is attributed to increased pressure from authorities and shifting tactics among attackers, indicating an adaptation to the evolving landscape of cybersecurity.
Focus on Data Theft and Extortion
Cybercriminals appear to be shifting strategies away from encryption, opting instead for data theft and extortion tactics. By stealing and threatening to leak sensitive data, attackers are effectively pressuring organizations to comply with ransom demands, showcasing a troubling trend where the nature of threats is diversifying.
Dominance of Qilin Ransomware Group
In Q2, the Qilin ransomware group has emerged as a notable player, leveraging innovative techniques to pressure targets and maximize ransom sums. The group has developed new tools that enhance their extortion capabilities, indicating a concerning pivot towards more aggressive tactics.
The Rise of AI in Ransomware Operations
The integration of AI into ransomware strategies is no longer theoretical. In 2025, many ransomware groups have begun incorporating AI into their operations. Check Point Research has documented instances where generative AI is used for crafting phishing content, obfuscating code, and impersonation efforts. AI democratizes access to sophisticated attack tools, lowering barriers for cybercriminals and reducing reliance on skilled developers.
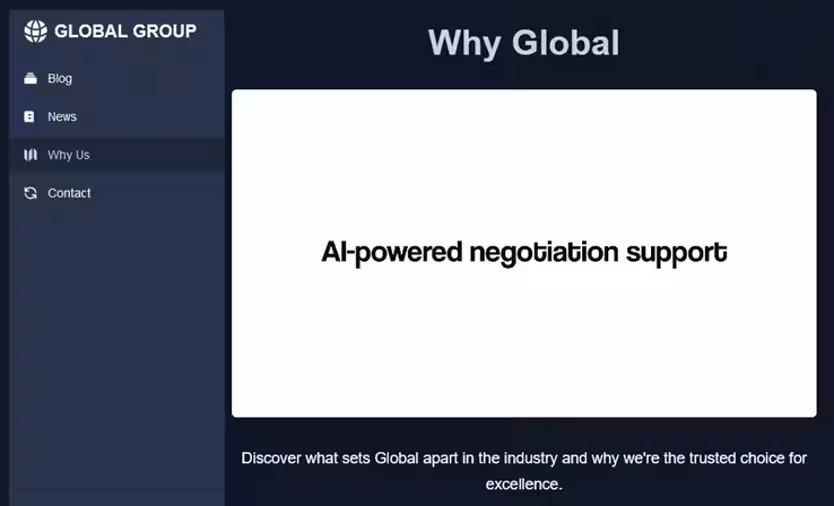
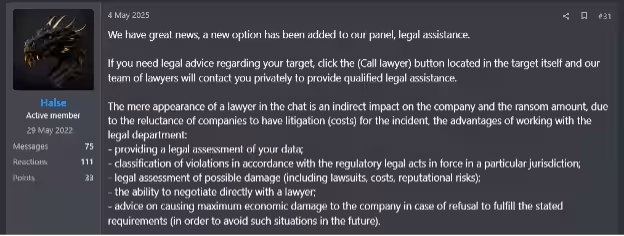
AI-Driven Negotiation Services
The Global Group, also known as El Dorado or Blacklock, has begun marketing AI-assisted negotiation services as part of their RaaS offerings. This service aims to optimize the attackers' negotiation tactics for securing higher ransom amounts, underscoring the evolving sophistication of ransomware operations. Suggestions from experts about these AI tools include tailored communication bots that can personalize ransom messages in response to target behavior, generation of more persuasive or intimidating messages, and psychological profiling to exert strategic pressure on decision-makers.
From Gangs to Cartels: Brands in Ransomware
The ransomware business model has shifted toward specialization and decentralization. The DragonForce group has pioneered a cartel model, allowing affiliated organizations to operate semi-independently while adhering to a central playbook. This model presents challenges for law enforcement and cyber defense measures.
Key Features of the Cartel Model
- - White-Label Tools: Affiliated organizations can access advanced ransomware builders and infrastructure provided by DragonForce, enhancing their operational capabilities.
- - Brand Licensing: Attacks carried out under the DragonForce name increase the visibility and perceived threat of these operations, even if core operators aren't directly involved.
- - Operational Independence: This structure allows groups to carry out unique attacks without drawing direct attention, complicating enforcement efforts.
The partnership with Ramp, the largest underground forum for ransomware, highlights DragonForce's strategic emphasis on branding and recognition.
Falling Payment Rates
Despite the increasing sophistication of ransomware, payment rates are reportedly declining. According to Coveware, global payment rates are dropping to 25-27% for the first time. Factors contributing to this decline include:
- - Increased Resilience: Organizations are investing more in backup solutions, segmentation, and incident response, enabling them to refuse ransom payments.
- - Distrust Towards Attackers: There's growing skepticism about the likelihood of receiving decrypt keys or data deletion post-payment.
- - Regulatory Pressure: Legislation prohibiting ransom payments is being proposed or enacted in nations like the U.S. and Australia, fundamentally altering risk assessments for organizations.
However, ransomware remains a lucrative avenue for cybercriminals, with tactics evolving continually.
Evolving Threats and New Normal Post-Collapse
No longer is ransomware dominated by a few notable names; the ecosystem has grown increasingly fragmented. Recent movements in Q2 suggest:
- - Major players like LockBit faced operational failures, losing affiliates.
- - The RansomHub group has reportedly gone inactive.
- - Mid-tier groups like Cactus are disappearing or splitting into smaller factions.
Despite a decrease in activity from some known groups, new actors are emerging, often reusing leaked code bases and tools while adopting stealthier methods to evade detection.
This fragmentation highlights that identifier delineations are increasingly ambiguous, complicating detection efforts for defenders. Smaller groups frequently operate unnoticed, revealing their presence only after initial breaches. Security responses must now address not only significant attacks but also a multitude of minor threats.
What Security Leaders Can Do
To maintain an edge against ransomware in 2025, organizations need more than just patch updates and perimeter defenses. Recommendations include:
- - Implement a comprehensive security architecture that encompasses endpoint, network, and identity protection across hybrid and multi-cloud environments.
- - Conduct widespread user awareness training and deploy phishing defenses capable of detecting AI-generated bait messages.
- - Segment backups and conduct regular recovery tests to ensure resilience.
For further details on the state of ransomware, including tactics utilizing AI, geopolitical insights, and practical defense strategies, check the full Ransomware Intelligence Report by Check Point Research.
Conclusion
The ransomware landscape continues to evolve rapidly, with AI integration and cartels reshaping threat dynamics for organizations worldwide. To stay ahead, security leaders must adapt their strategies and invest in comprehensive solutions that address the complexities of this new era in cybercrime.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.