
Check Point Research Reports Surge in Ransomware Attacks in Q1 2025
Overview of Ransomware Attacks in Q1 2025
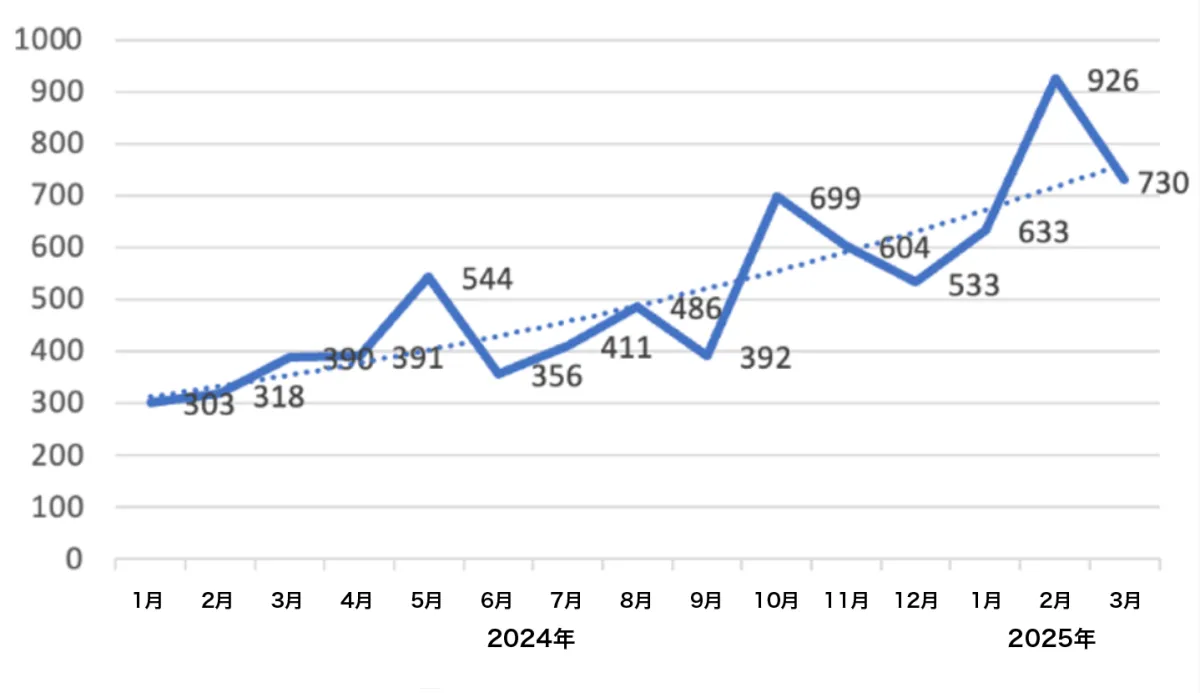
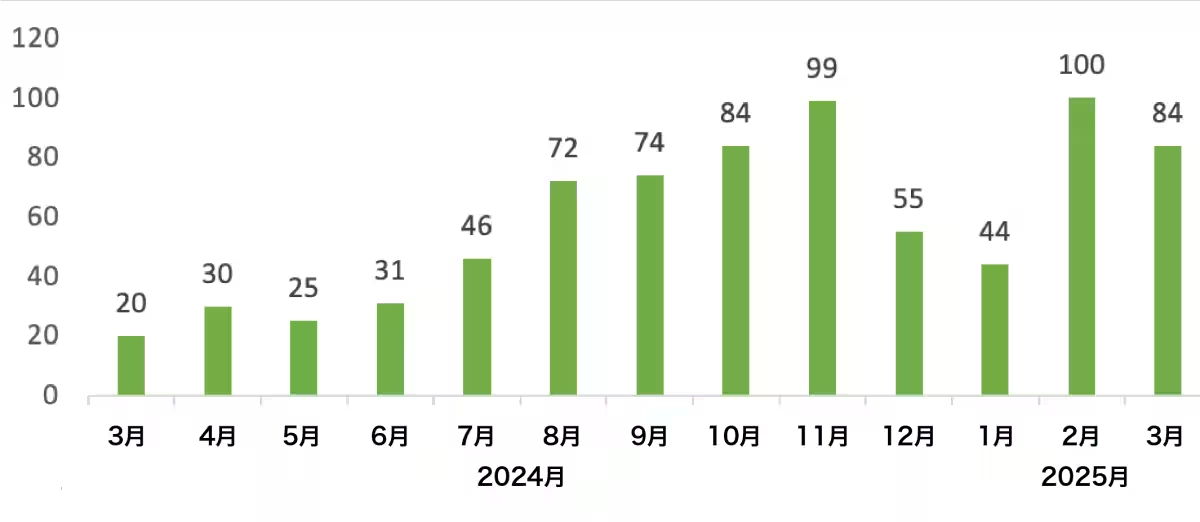
Check Point Research (CPR), a leader in cybersecurity solutions, announced its ransomware report for the first quarter of 2025. The report highlights a staggering 126% increase in ransomware attacks compared to the same period last year, with a total of 2,289 victims publicly reported on leak sites. The number of ransomware groups has also risen to 74, marking a record high for a single quarter.
Key Trends Observed
The report's data reveals several concerning trends:
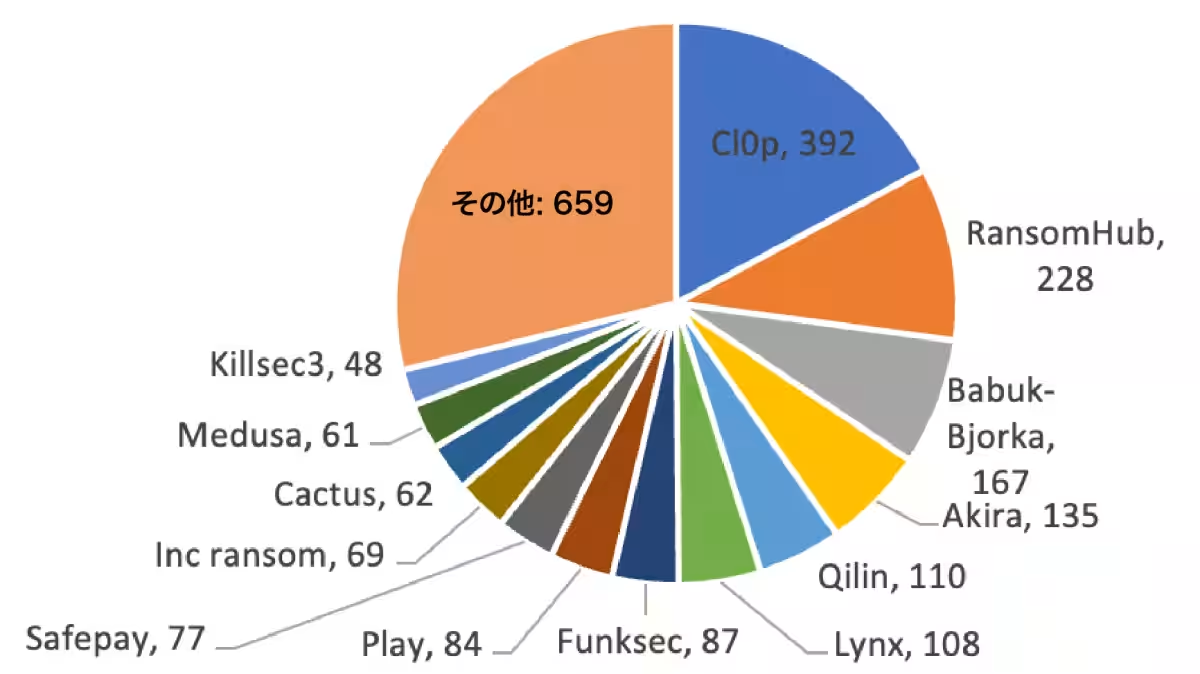
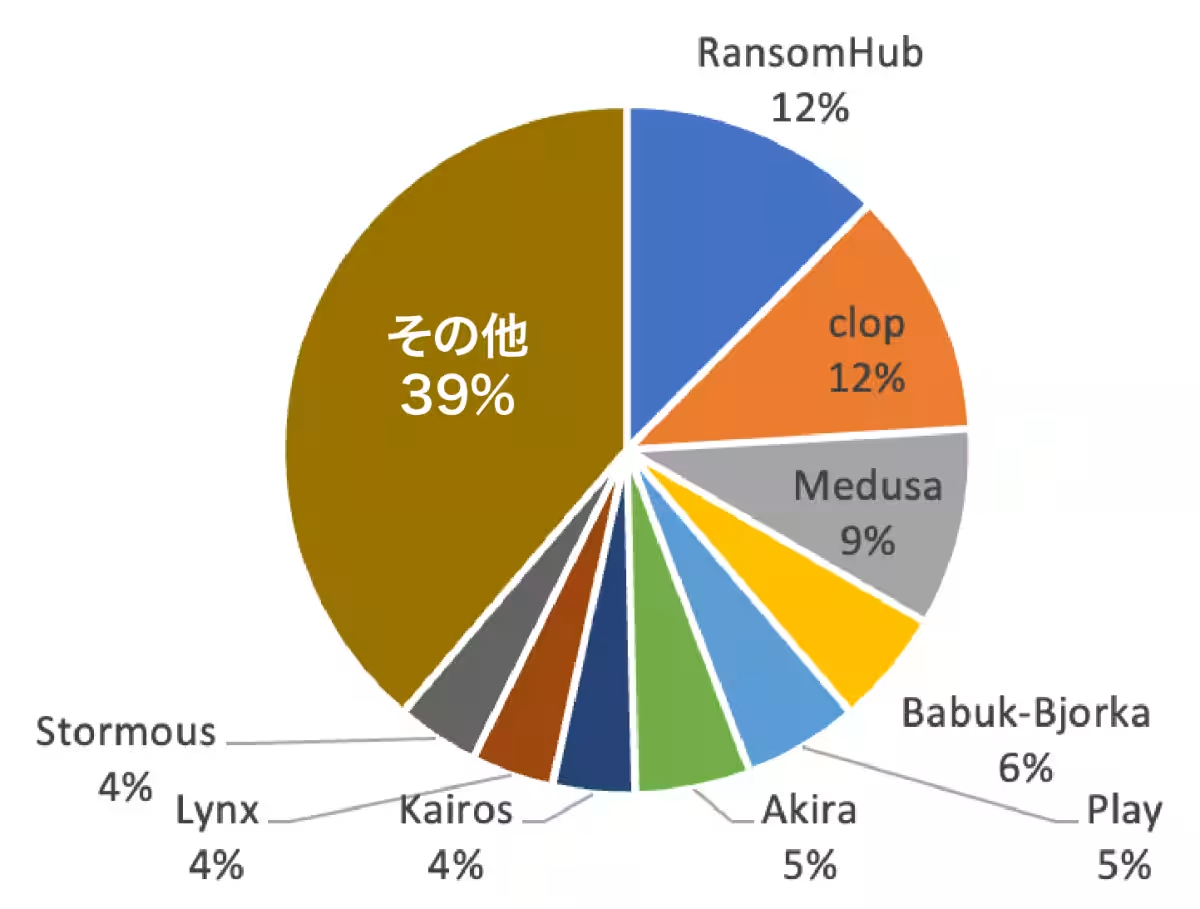
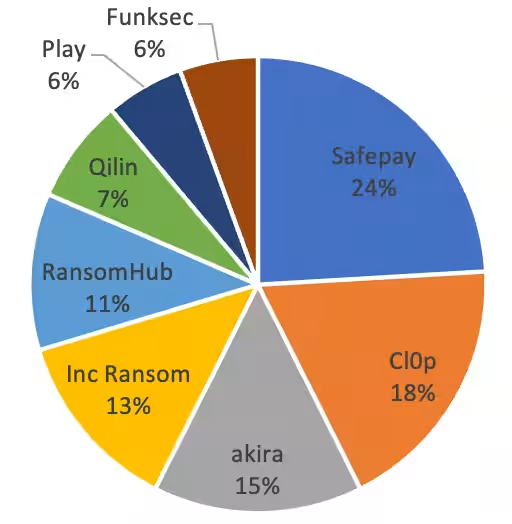
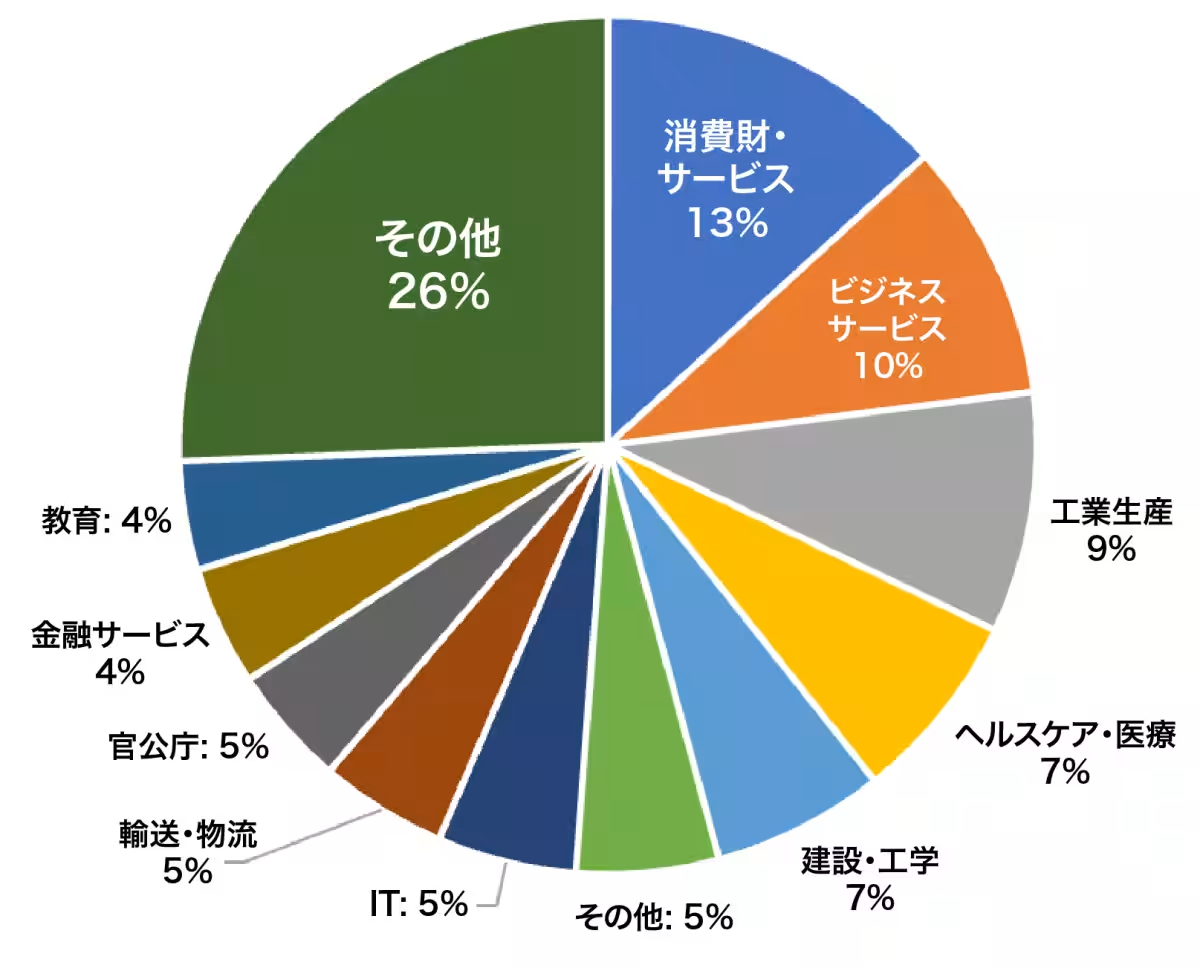
1. Cl0p's Surge: Cl0p emerged as the most active group during this quarter, utilizing a zero-day vulnerability in the Cleo file transfer tool. Instead of encrypting data, 392 incidents were reported where Cl0p stole data and demanded ransom. A significant 83% of these victims were located in North America, with 33% from the consumer goods and services sector, highlighting a strategic targeting of the supply chain.
2. RansomHub's Rise: Inheriting the operations of LockBit, RansomHub reported 228 victims this quarter. Its strategy focused on aggressive affiliate recruitment and high reward distribution, allowing it to capture market share from LockBit.
3. Deceptive Tactics: Groups such as Babuk-Bjorka and FunkSec have been reported to misuse previously published victim lists, falsely claiming attacks against organizations they haven’t targeted (Babuk-Bjorka claimed 167 incidents, and FunkSec over 170). Such practices inflating their records to attract affiliates and enhance their reputation are problematic. FunkSec is suspected to be leveraging AI-driven malware, complicating the identification and response to these attacks.

Global Targeting of Ransomware
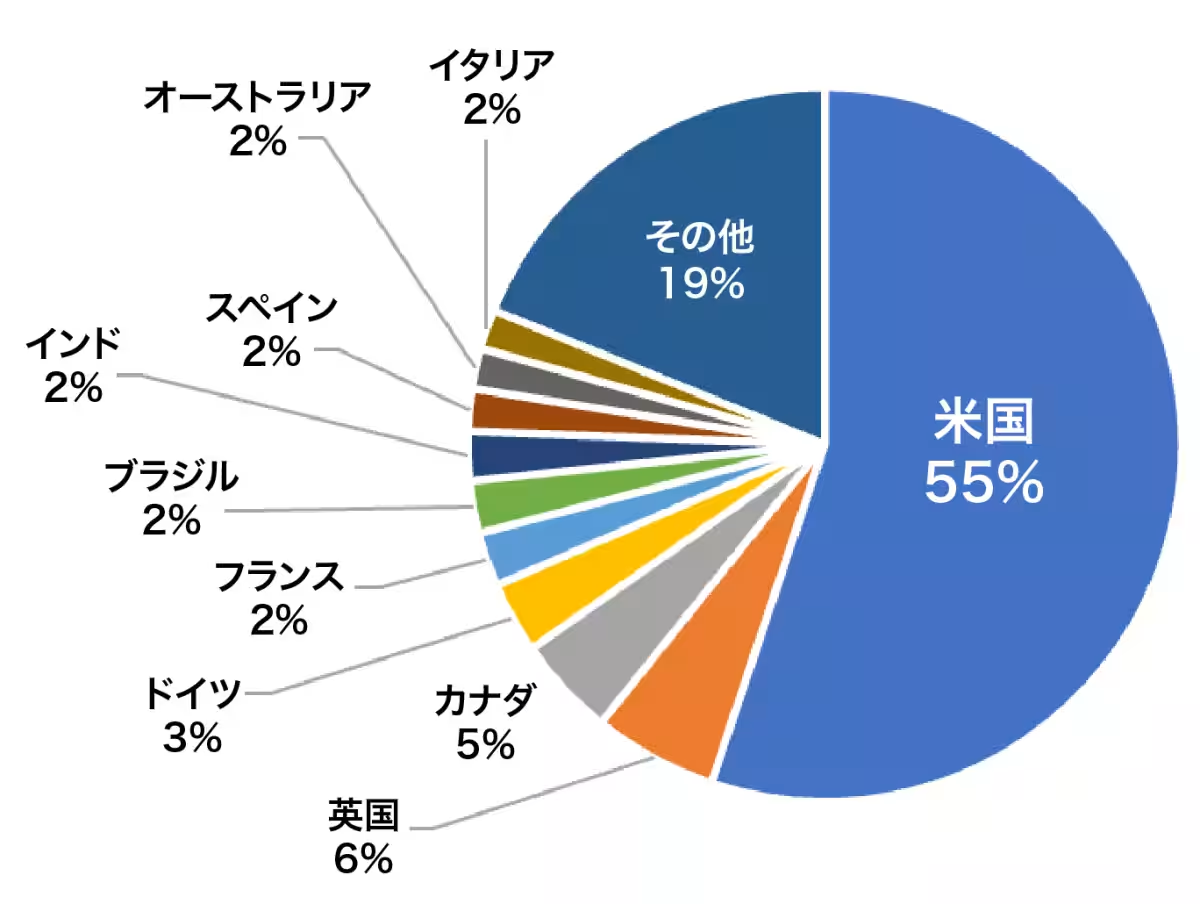
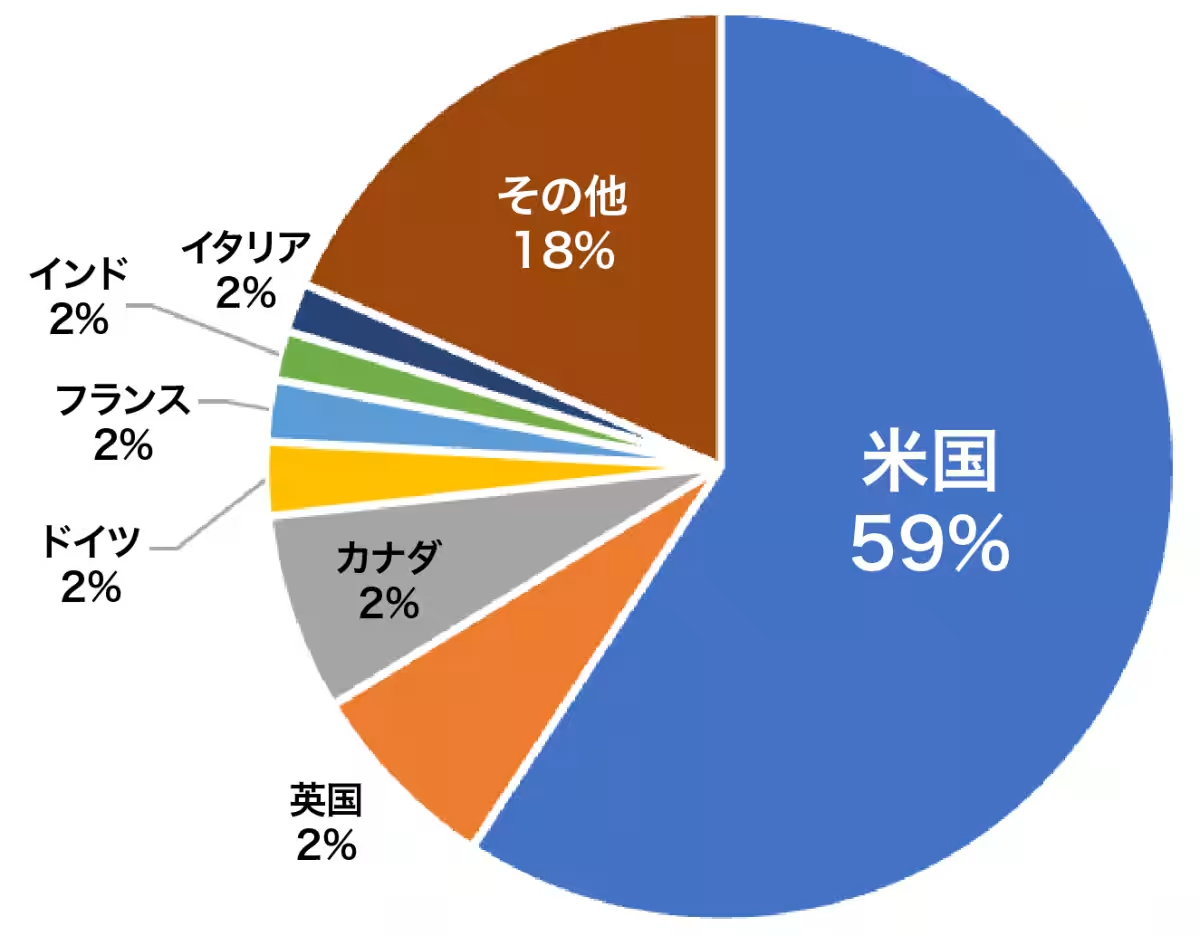
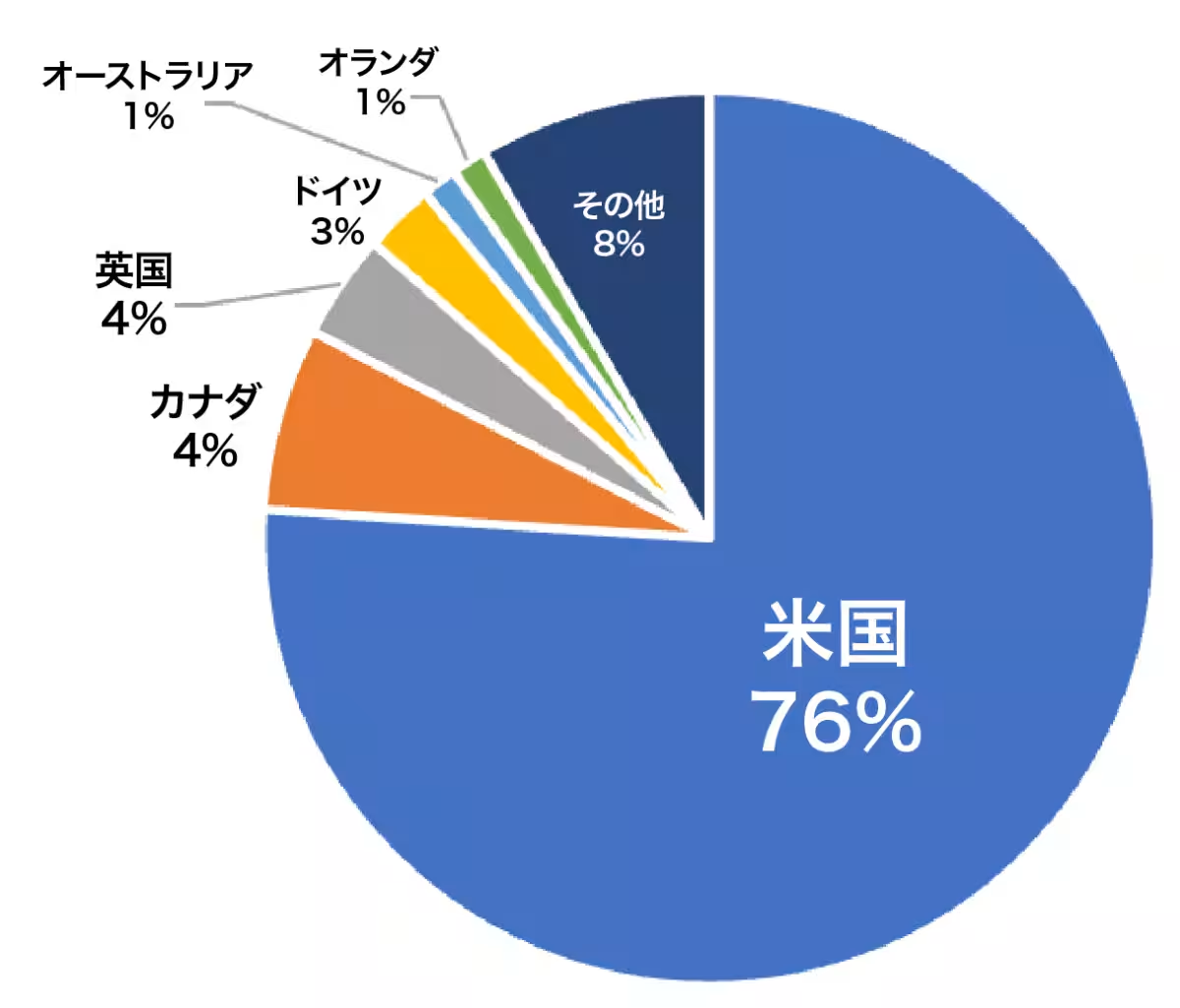
- - The United States continues to be the main target, accounting for nearly 50% of all reported victims. The high likelihood of U.S. companies paying ransoms influences this.
- - In the UK, Medusa ransomware has claimed 9% of domestic incidents, exhibiting a fivefold increase compared to global shares.
- - In Germany, Safepay represented 24% of reported attacks, indicating a targeted approach by attackers. Each ransomware group appears to strategically select targets based on local infrastructure, legal contexts, and ransom payment capabilities.

According to Chainalysis, while the number of publicly reported ransomware incidents has surged, actual ransom payments have decreased by 35%. This divergence suggests a growing trend where victims are either refusing to pay or where some identified victims may not exist at all.
Evolving Ransomware Strategies
Ransomware is evolving to prioritize ransom requests without encryption, with tactics focusing on tarnishing corporate reputations rather than technical data recovery. This indicates a significant shift in the threat landscape, where attackers exploit reputational risks instead of just encryption. The statistics based on conventional leak sites do not accurately reflect real-world situations, making it increasingly challenging for security teams, regulators, and law enforcement to monitor attackers effectively.

As Sergey Shykevich, head of the threat intelligence team at Check Point, states, “Ransomware attacks are not just statistics; they are a crucial indicator that shows attackers are using more sophisticated methods to manipulate our psyche, making it harder to track them down.” Shykevich emphasizes the importance for organizations to shift from reactionary defenses to preventive, intelligence-based security measures, especially with the misuse of AI and deceptive reporting emerging as new challenges.
About Check Point Research
Check Point Research offers cyber threat intelligence to its customers and the wider security community, collecting and analyzing data on cyberattacks globally. With over 100 analysts, they work in collaboration with security vendors and law enforcement to improve cybersecurity measures.
To learn more about cybersecurity, visit our blog at Check Point Research.
About Check Point Software Technologies
Check Point Software Technologies provides cybersecurity protection to more than 100,000 organizations worldwide as a leading provider of AI-driven cloud cybersecurity platforms. Learn more at Check Point's Website.
For media inquiries, please contact the Check Point PR team.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.