
Check Point Research Leverages AI to Analyze the Advanced Xloader Malware Threat
Check Point Research Unveils AI-Enhanced Analysis of XLoader Malware
Check Point Software Technologies, a global leader in cybersecurity solutions, has released a comprehensive analysis report on the information-stealing malware known as XLoader 8.0. Conducted by its Threat Intelligence division, Check Point Research (CPR), this report highlights the integration of generative AI into traditional malware analysis workflows, resulting in unprecedented speed and depth in understanding malware behavior.
Key Highlights from the Analysis
XLoader 8.0 is recognized as one of the most sophisticated information-stealing malware pieces currently in existence. It employs multiple layers of encryption, uses fake domains, and receives periodic updates to evade detection effectively. The CPR team utilized AI-driven malware analysis to transition from manual reverse engineering processes that typically took several days to completing the same tasks within mere hours.
AI has demonstrated capabilities in automatically identifying encryption layers and decrypting functions, uncovering hidden command-and-control (C2) domains, and enabling faster extraction of indicators of compromise (IoCs). This innovation leads to improved threat intelligence and a strengthened protective framework for users worldwide.
The Nightmare for Analysts
Since 2020, XLoader has evolved from the FormBook malware family, specializing in information theft through complex obfuscation methods that impede detection by antivirus tools and sandbox environments. Traditional malware analysis, which relied heavily on time-consuming manual processes, required experts to deconstruct binaries, trace functions, and generate decryption scripts. Even employing sandbox environments was often ineffective as XLoader reveals its true code only during execution and can detect when it is under scrutiny.
This makes XLoader a prime example of modern malware that weaponizes time, complexity, and obfuscation.
AI-Driven Reverse Engineering
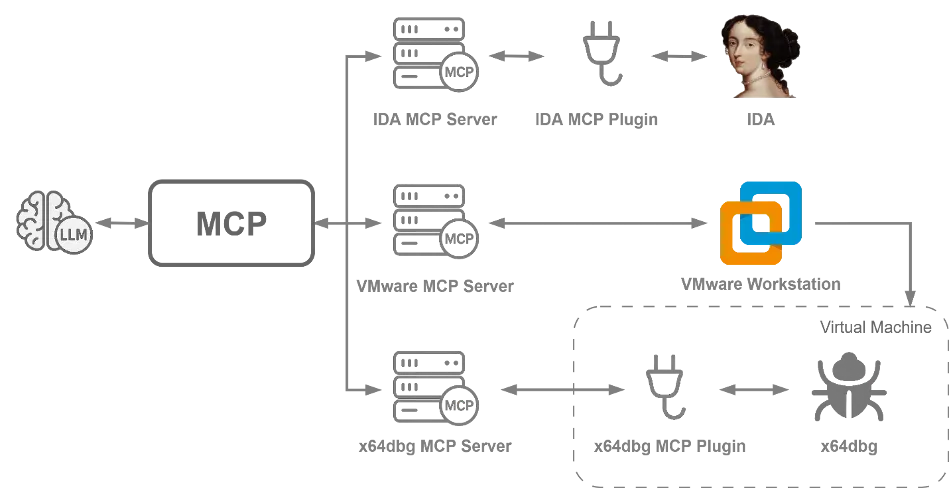
To streamline and automate the analysis process, CPR implemented AI-driven malware analysis techniques. By integrating ChatGPT (GPT-5), they developed two complementary workflows:
1. Cloud-Based Static Analysis: Data exported from IDA Pro (disassembled data, decompiled functions, and strings) is analyzed in the cloud. The AI model identifies encryption algorithms, recognizes data structures, and generates Python scripts to decode specific code sections.
2. MCP-Powered Runtime Analysis: The AI connects to a live debugger to extract runtime values from the malware, such as encryption keys, decrypted buffers, and C2 data in memory.
This hybrid AI workflow transforms cumbersome manual reverse engineering into a quicker, repeatable, and more sharable semi-automated process.
What AI Has Revealed
Leveraging the new workflow, CPR achieved significant breakthroughs:
- - Core Code Decryption: AI-generated scripts successfully decrypted over 100 previously encrypted functions.
- - Deciphered Encryption Layers: The analysis identified three complex decryption schemes utilizing modified RC4 algorithms and XOR markers.
- - Unveiling Hidden APIs: Previously obscured Windows API calls were automatically deobfuscated through custom hash processing.
- - Restored 64 Hidden C2 Domains: By decrypting multi-layered encodings like Base64 and RC4, the analysis revealed the attacker’s actual infrastructure.
- - Discovered New Sandbox Evasion Techniques: The research identified a “Secure Call Trampoline” that temporarily encrypts parts of the malware during execution to evade monitoring.
These discoveries underscore how AI contributes to understanding XLoader’s obfuscation, communication, and self-defense mechanisms, which are crucial for strengthening detection and defensive capabilities. As a result, Check Point's threat intelligence can deliver faster, more accurate protective updates.
Innovations Brought by AI in Cybersecurity
AI is not a replacement for malware analysts but rather a significant enhancement of their capabilities:
- - Speed: Tasks that once took days can now be completed in under an hour.
- - Reproducibility: With exported datasets, anyone can rerun the AI workflow and verify results.
- - Insights: Automation allows analysts to focus on in-depth behavioral analysis of malware propagation, information theft, and evolution.
- - Defense: Rapid extraction of IoCs accelerates the response from threat detection to defense deployment.
Generative AI is becoming a powerful tool for incident response, reverse engineering, and threat hunting.
Conclusion
While malware creators may eventually develop methods to counter AI-driven analysis, the advantage remains clear for defenders. Utilizing AI enables near real-time response capabilities against complex and highly encrypted threats like XLoader. CPR will continue refining workflows that combine AI automation, scripting, and runtime validation to expand malware analysis and threat detection efforts.
For the full report by CPR, click here.
About Check Point Research
Check Point Research provides the latest cyber threat intelligence information targeting Check Point's clients and the threat intelligence community. By collecting and analyzing data on cyberattacks stored within Check Point's ThreatCloud AI, they develop protective features while deterring hackers. This dedicated team consists of over 100 researchers and analysts working collaboratively with security vendors, law enforcement, and various CERT organizations.
About Check Point Software Technologies
Check Point Software Technologies is a leading provider of digital trust, protecting over 100,000 organizations worldwide through AI-powered cybersecurity solutions. Its Infinity Platform and open-garden ecosystem ensure reduction of risks while achieving the highest level of security effectiveness. By adopting a hybrid mesh network architecture centering around SASE, the Infinity Platform integrates management across on-premises, cloud, and workspace environments, delivering flexibility, simplicity, and scalability to enterprises and service providers.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.