
Check Point Research Raises Alarm on Cyber Attacks Using PDF Weaponization Techniques
Check Point Research Issues Alerts on PDF-based Cyber Attacks
In the ever-evolving landscape of cyber threats, Check Point Research (CPR), the threat intelligence arm of Check Point Software Technologies, has issued a critical alert regarding the increasing use of PDF files in cyberattacks. This form of attack is growing more sophisticated, blending tactics that exploit the vulnerabilities in PDF readers with social engineering and evasion techniques to ensure malicious activities go undetected.
The Prevalence of PDF Files
According to CPR, over 400 billion PDFs were opened globally last year, with a staggering 87% of businesses utilizing PDF as their standard communication format. This widespread adoption makes PDF an attractive vector for cybercriminals, who take advantage of its ubiquity and perceived safety.
The research shows that 68% of cyberattacks are delivered via email, with 22% of those containing malicious PDF attachments. For businesses that consistently handle PDFs, this statistic signals a rising tide of hidden threats that could compromise sensitive information and systems.
Evolving Tactics and Techniques
Threat actors today are well-versed in existing security measures and are adept at employing advanced evasion tactics that outsmart traditional security vendors. Notably, some attacks remain undetected even in antivirus scans, with tools like VirusTotal reporting zero detections over the past year.
Check Point’s Threat Emulation provides real-time zero-day protection against these challenging threats, effectively blocking attack chains before they cause damage.
Why PDFs Are Targeted
The structure of the PDF specification (ISO 32000) extends nearly 1,000 pages, filled with complexities that allow cybercriminals to slip through security detection mechanisms. While PDFs appear user-friendly and straightforward, they pose significant challenges for security systems due to their complexity, facilitating evasion of automated detection systems.
Recently, attackers have shifted from exploiting known vulnerabilities in PDF readers or embedding malicious JavaScript to using straightforward yet effective social engineering tactics. Since PDFs are generally deemed safe and trusted, they are cleverly used to disguise harmful links or content. Additionally, many email security systems focus on other formats, allowing PDFs to evade detection more easily.
Anatomy of a PDF Attack Campaign
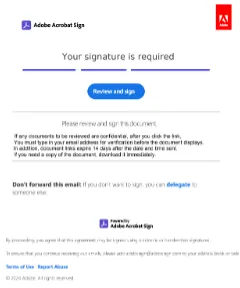
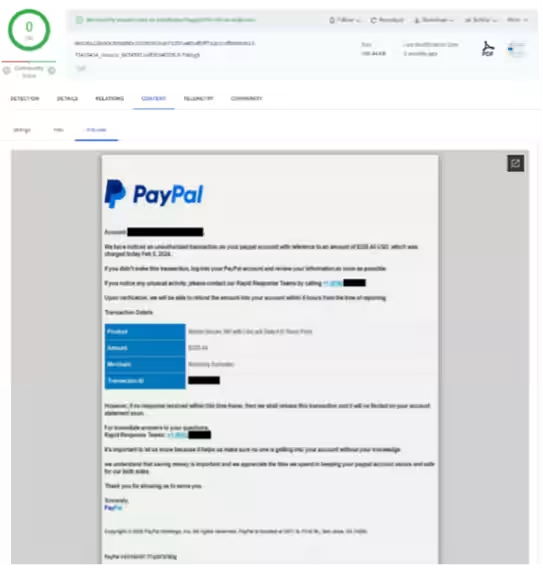
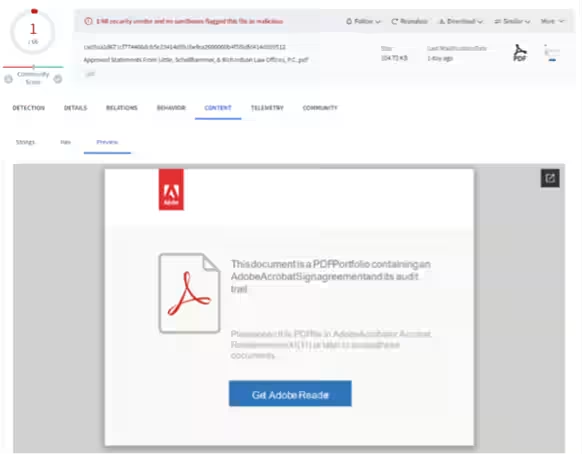
One of the most commonly observed techniques by CPR involves using embedded links within PDFs to direct users to phishing sites or malicious file downloads. Often, these links are designed to mimic trusted brands such as Amazon, DocuSign, or Adobe Acrobat, enhancing their credibility and making them seem innocuous.
Attackers have full control over the links, text, and images, complicating detection based on reputation or static signatures. The requirement for human judgment—clicking on links—also poses difficulties for sandboxing and automated detection systems, further tilting the scale in favor of attackers.
Evasion Techniques Employed by Threat Actors
Malicious actors are continuously refining their strategies to evade detection by security systems. Here's an overview of their evasion techniques:
- - Using Harmless Redirect Services: Attackers often use well-known redirect services like Bing or Google AMP URLs to obscure the true destination. These sites are frequently whitelisted by security vendors, complicating threat identification.
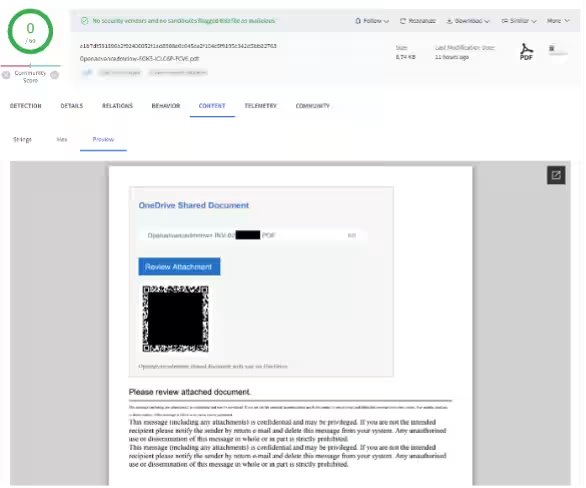
- - Embedding QR Codes: By embedding QR codes in PDFs and prompting users to scan them with smartphones, attackers can bypass traditional URL scanners entirely.
- - Phone Scams: Social engineering tactics may lead users to call a specific phone number, rendering suspicious URLs unnecessary, yet still requiring human interaction.
Static Analysis Evasion Strategies
Exploiters leveraging the intricate design of PDFs have devised methods to outsmart security tools during static analyses. For instance, they manipulate PDF annotation capabilities and exploit variances in how PDF readers interpret data, thereby deceiving automated detection mechanisms.
They can also obscure files using techniques like encryption or indirect objects, which may make a PDF appear broken, yet remain accessible to conventional PDF readers. This creates added difficulties for automated security solutions.
The Advent of Machine Learning Evasion Techniques
As security systems integrate machine learning capabilities, corresponding evasion tactics have become more advanced. For example, embedding text within images poses challenges for OCR (Optical Character Recognition), affecting speed and accuracy during detection. Attacks may also involve manipulating images or using ultra-low resolution to confuse security measures.
Defensive Measures Against PDF-based Threats
To mitigate risks associated with PDF-based attacks, Check Point recommends the use of their Threat Emulation and Harmony Endpoint solutions, which defend against a wide array of attack tactics, including file types and operating systems. Users can also implement the following strategies to reduce exposure:
- - Verify Sender Authenticity: Always double-check the email address of the sender, even if the PDF appears legitimate, as cybercriminals often impersonate trusted brands or colleagues.
- - Be Cautious with Attachments: Remain vigilant when receiving unexpected PDFs, especially those urging link clicks or QR code scans.
- - Hover Over Links Before Clicking: Verify the actual URL of any link in the PDF before clicking. Be wary of shortened links or redirects.
- - Use Secure PDF Viewers: Ensure that you utilize updated browsers and PDF readers with built-in security features, while avoiding outdated or unreliable software.
- - Disable JavaScript in PDF Readers: Unless necessary, disabling JavaScript can mitigate the risk of script-based exploits.
- - Keep Systems and Security Tools Updated: Regular updates help close vulnerabilities exploited by malicious PDFs, amplifying defenses against potential attacks.
- - Stay Alert for Suspicious Signs: Be aware of unusual content, display abnormalities, or requests for sensitive credentials.
The insights herein are based on a blog released on April 2, 2025, detailing the evolving risks posed by PDF weaponization in cyberattacks.
About Check Point Research
Check Point Research delivers the latest cyber threat intelligence to Check Point's customers and the broader threat intelligence community. They gather and analyze global cyberattack data housed in Check Point’s ThreatCloud AI to deter hackers while contributing to the efficacy of protective features integrated into Check Point products. With a team of over 100 analysts and researchers, CPR collaborates with security vendors, law enforcement, and CERT organizations to bolster cybersecurity defenses.
About Check Point Software Technologies
As a leading provider of AI-driven cloud-based cybersecurity platforms, Check Point Software Technologies safeguards more than 100,000 organizations worldwide. Through the Infinity Platform, they harness AI to enhance the efficiency and accuracy of cybersecurity measures, ensuring proactive defense and responsive actions. The platform comprises solutions for employee protection (Check Point Harmony), cloud security (Check Point CloudGuard), network security (Check Point Quantum), and collaborative security operations (Check Point Infinity Core Services). Established in 1997, Check Point maintains its Japan branch in the Minato district of Tokyo.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.