
Rapid Growth of SafePay Ransomware Group Highlights Cyber Threats as of May 2025
Cybersecurity Alert: The Latest on Ransomware Threats in May 2025
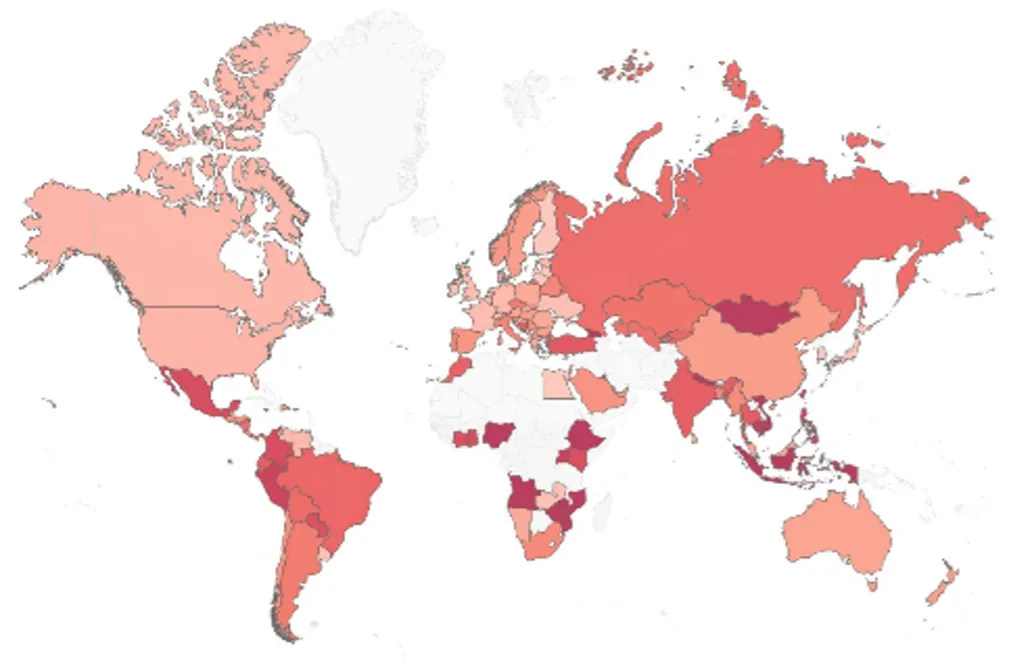
In the latest report from Check Point Research, a leader in cyber threat intelligence, the month of May 2025 has unveiled pressing concerns in the realm of cybersecurity. The Global Threat Index highlights the unprecedented rise of a relatively new ransomware group named SafePay, marking it as the most active in this period. This group's alarming capability to leverage double extortion tactics is forcing organizations worldwide to reassess their security protocols to combat this evolving threat.
Emergence of SafePay
Since its observation in late 2024, SafePay has rapidly developed into a significant player in the ransomware landscape, causing distress across enterprises of all sizes. The group not only encrypts victims' files but also threatens to leak confidential data to pressure them into paying the ransom. This dual-threat approach has raised their profile significantly, as it forces victims into a damaging position, both economically and reputationally.
Interestingly, while SafePay's activities dominate headlines, the familiar name of FakeUpdates continues to pose a pervasive threat. This malware variant has consistently ranked as the most widespread, affecting numerous organizations globally with a 3.26% impact rate in May 2025.
Law Enforcement and Cyber Operations
In a noteworthy development, May saw extensive collaboration among law enforcement agencies such as Europol and the FBI, alongside tech giants like Microsoft, to dismantle a malware-as-a-service platform known as Lumma. This large-scale operation resulted in the seizure of thousands of domains, significantly disrupting Lumma's operations. However, despite the crackdown, it appears that the core servers based in Russia remain operational, with the developers reportedly rebuilding their infrastructure quickly.
The persistence of Lumma signifies the ongoing challenges in combating phishing tactics that erode user trust in these services, hence indicating a complicated battle against such cyber threats.
Activating Security Measures
Lotem Finkelstein, Check Point’s Director of Threat Intelligence, emphasizes the need for organizations to adopt proactive and multilayered security measures. According to Finkelstein, the data from May illustrates how rapidly the tactics employed by cybercriminals are evolving. As such, organizations must be equipped with real-time threat intelligence and robust defenses to stay ahead of ongoing cyber threats.
Malware Landscape in May 2025
In May, the top malware families in the domestic landscape included:
- - FakeUpdates (3.26%): This downloader type malware has been notorious since its discovery in 2018. It spreads through malicious websites and prompts users to install fake browser updates. The malware is believed to be affiliated with the Russian hacking group Evil Corp and is often used to deliver payloads after infection.
- - Androxgh0st (2.51%): This Python-based malware targets applications using the Laravel PHP framework, scanning exposed .env files for login credentials to various services.
- - Remcos (2.01%): Known as a remote access trojan (RAT), Remcos bypasses security mechanisms of Windows to execute its malware, typically spread via phishing campaigns.
Globally, FakeUpdates was similarly the most widespread malware, affecting around 5% of organizations, followed by Remcos and Androxgh0st, both at 3% impact.
Conclusion and the Road Ahead
The Threat Index for May 2025 clearly illustrates the increasing complexity of cyber threats, with new ransomware actors like SafePay complicating the existing landscape dominated by malware like FakeUpdates. The particularly high frequency of attacks targeting educational institutions indicates a pressing need for organizations across all sectors to enhance their security frameworks proactively. Organizations are urged to stay vigilant and adopt advanced defensive measures against the backdrop of a continuously evolving cyber threat environment.
For more comprehensive insights on the Global Threat Index and detailed analysis, visit Check Point’s blog.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.