

Netskope Uncovers New Ransomware Variant Named 'DOGE Big Balls'
New Ransomware Discovery: 'DOGE Big Balls'
Netskope Threat Labs, the research division of the leading security and networking company Netskope, has recently identified a complex ransomware variant named 'DOGE Big Balls.' This particular malware is derived from the existing Fog ransomware and employs a range of custom tools and specialized techniques to strategically breach enterprise networks. What’s particularly intriguing about this ransomware is its name, which serves as a provocative jab at the U.S. Department of Government Efficiency (DOGE) and features politically charged statements, including quotes from prominent public figures and YouTube videos designed to taunt victims.
Over the past few months, various reports from cybersecurity firms like Trend Micro, Cyble, and DFIR Report have elucidated the activities of this ransomware variant. In this article, we will delve into the newly discovered malware payloads and examine the entire infection chain associated with 'DOGE Big Balls.'
Key Findings from Netskope Threat Labs
Netskope Threat Labs has discovered multiple new scripts and binary files believed to be employed by the attackers affiliated with the 'DOGE Big Balls' ransomware. They have pinpointed a wide array of diverse tools utilized at each phase of the attack, including custom scripts for lateral movement, privilege escalation, and credential theft. Moreover, the analysis identified the features used to exploit vulnerable drivers and deploy the ransomware payloads along with another payload known as Havoc Demon.
Importantly, the attackers have been progressively updating their methodology and tools, frequently refreshing the contents of their payloads hosted on the Netlify platform. This continuous evolution ensures the infection process remains effective at every step.
Mechanics of the Multi-Stage Infection Chain
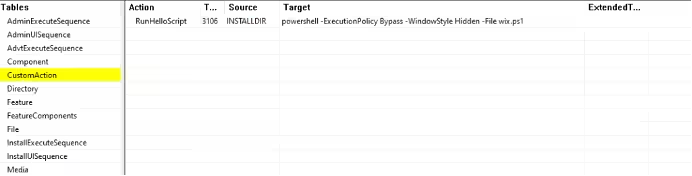
The ransomware attack initiates with an MSI file which executes an encoded PowerShell script. This script establishes persistence by utilizing the Windows startup folder and scheduled tasks. The main infection script downloads multiple tools, disabling security measures while broadly infiltrating the network.
Techniques Used in the Attack:
Advanced AMSI bypass techniques to evade security detection.
Credential theft utilizing tools such as Mimikatz.
Lateral movement across hosts through multiple methods, including SMB and PsExec and using stolen Kerberos tickets.
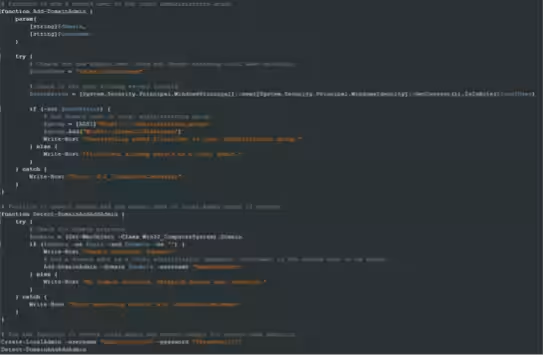
Targeting domain controllers to create administrator accounts for privilege escalation.
Establishing remote connections through ZeroTier network software.
Implementing cryptocurrency mining as an additional revenue stream.
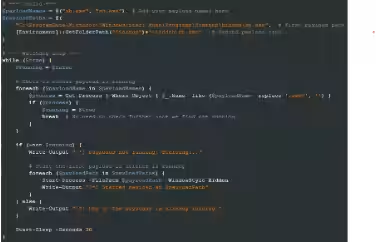
The attacking parties are consistently refining their toolkit, with recent updates including scripts designed to target domain administrators and secure ongoing access to breached systems. During investigation efforts, it became clear that both the payloads and the URLs used for downloads exhibited frequent updates.
Upon attempting to download a new version, researchers discovered that the stage1.ps1 script had evolved to incorporate two new scripts: addadmins.ps1 and shwatchdog.ps1. The first script is responsible for creating administrator accounts on infected machines and adding domain users to the admin group. The second script ensures the constant execution of specific payloads (notably sh.exe).
Detection by Netskope
The threats associated with this ransomware include:
Generic.ShellCode.Marte.2.F02D5747
Script-PowerShell.Trojan.Powdow
Win64.Backdoor.Swrort
Win32.Infostealer.Tinba
Win32.Trojan.ShellcodeRunner
Gen.Malware.Detected.By.IT
Importance of Continuous Monitoring and Mitigation
The plethora of payloads related to this ransomware and their frequent updates exemplify the complexity and dangers inherent in the ransomware attack that encompasses multiple phases such as lateral movement, privilege escalation, and credential theft. Regardless of whether the motivation stems from malice or mischief, the repercussions can severely impact environments and businesses alike. The Netskope Threat Labs team will persist in monitoring these malicious campaigns, related activities, and the malign payloads employed in these attacks. All IOC (Indicators of Compromise) associated with this malware is publicly available in our GitHub repository.
For an in-depth exploration of the 'DOGE Big Balls' ransomware, please refer to our blog (in English).
About Netskope Threat Labs
Netskope Threat Labs employs some of the industry’s leading cloud threat and malware researchers, focusing on the detection, analysis, and design of defenses against emerging cloud threats that may adversely affect enterprises. Through unique research and detailed analysis on threats related to cloud phishing, fraud, malware distribution, command and control, and data extraction or exposure, the lab protects Netskope customers from malicious adversaries and contributes to the global security community through research, advice, and best practices. The lab is led by researchers and engineers with extensive experience in establishing and managing companies worldwide, including Silicon Valley. Regularly participating as speakers and volunteers at the most prestigious security conferences, including DefCon, BlackHat, and RSA, the researchers continue to advance the field of cybersecurity.
About Netskope
Netskope leads the industry with cutting-edge security and networking technology. Providing optimized access and real-time context-based security, we meet the needs of both security and networking teams, regardless of where individuals, devices, or data are located. Thousands of customers, including over 30 Fortune 100 companies, trust and leverage the Netskope One platform, zero-trust engine, and powerful NewEdge network. These solutions enable visibility into usage across cloud, AI, SaaS, web, and private applications, facilitating security risk reduction and enhanced network performance. For more information, please visit netskope.com/jp.
Media Inquiries
For media-related inquiries, please contact:
Netskope Public Relations Office (next PR LLC)
TEL: 03-4405-9537
FAX: 03-6739-3934
E-mail: [email protected]

Topics Consumer Technology)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.