
Expansion of Cyberattacks on European Companies by Nimbus Manticore Threat Actors
The Rise of Nimbus Manticore's Cyberattacks on European Companies
In an alarming development, Check Point Research (CPR) has confirmed the expanding activities of the Iranian-backed cyber threat group known as Nimbus Manticore, which has been increasingly targeting companies across Europe. This group has been under close watch by CPR, which has been actively tracking their operations and methodologies.
Key Highlights
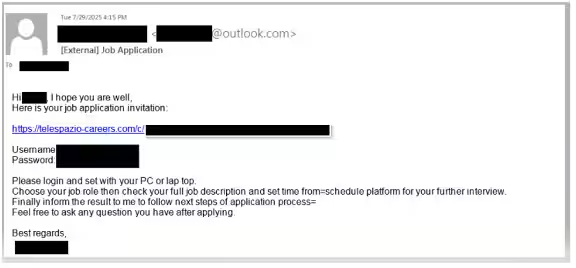
CPR's latest findings indicate that Nimbus Manticore has shifted its focus towards European defense, communications, and aerospace sectors, primarily for intelligence-gathering purposes. Using fake job portals and spear-phishing tactics, the group lures victims under the guise of legitimate recruitment processes, sending malicious files that appear to be from reputable aerospace companies.
Advanced malware such as MiniJunk and MiniBrowse allows these attackers to maintain stealth, steal data, and ensure long-term access to their victims' systems. These operations align with the strategic priorities of the Iranian Revolutionary Guard Corps (IRGC), particularly during times of heightened geopolitical tension, emphasizing the collection of sensitive information from critical defense vendors.
Since early 2025, CPR has observed a series of activities associated with Nimbus Manticore, also referred to as UNC1549 or Smoke Sandstorm. The group, previously linked to the Iranian Dream Job campaign, has predominantly targeted the aerospace and defense sectors both in the Middle East and Europe.
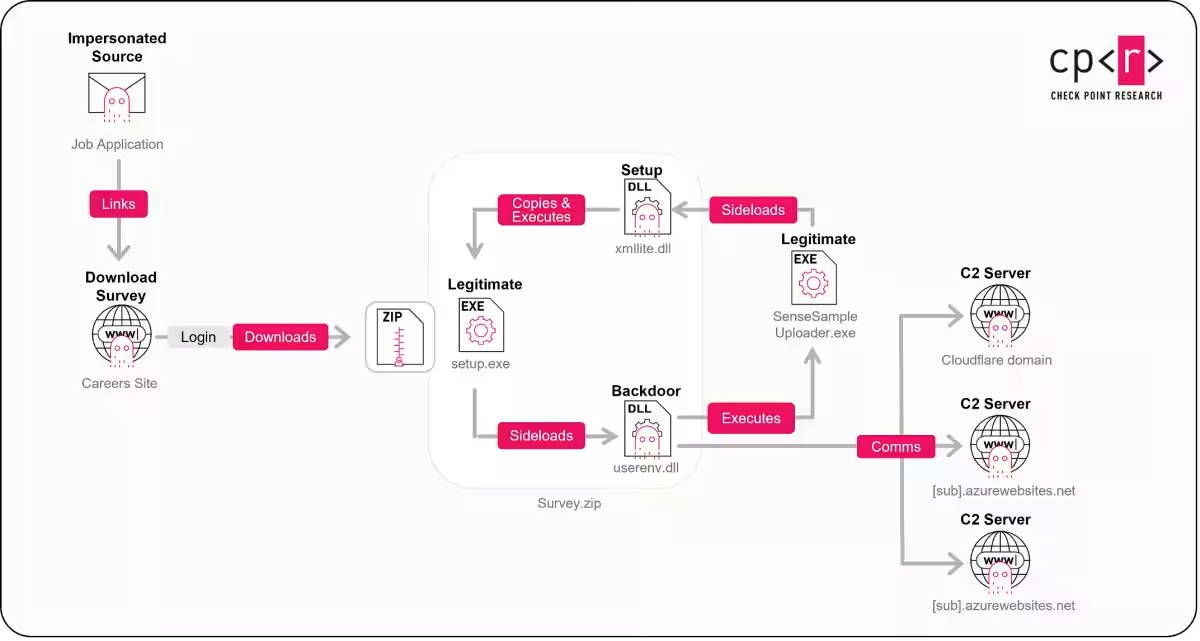
The group's prowess in delivering customized implants such as Minibike (also called SlugResin) is notable. Since its initial report in 2022, Minibike has evolved steadily, adopting obfuscation techniques, modular architecture, and redundant command-and-control (C2) infrastructures. Recent activities show significant advancements, including the use of new methods that allow them to load DLL files from alternative paths by modifying execution parameters. This evolution reflects Nimbus Manticore's ongoing efforts to evade detection.
Malware Distribution and Victim Targeting
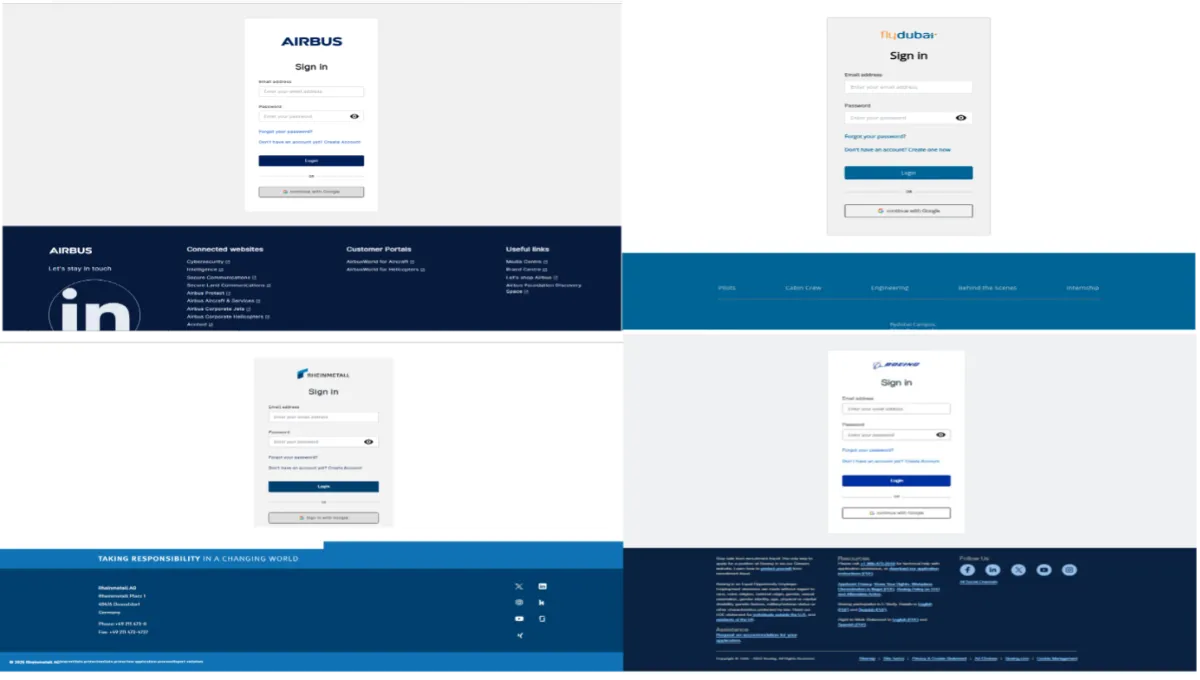
The infection chain begins with phishing links redirecting victims to fake job-related login pages. These sites share several common characteristics:
- - Brand Spoofing: Websites impersonating reputable aerospace brands like Boeing, Airbus, and Rheinmetall, tailored with appropriate React templates.
- - Domain Strategy: Domains often have career-themed names, registered under Cloudflare for obfuscation, hiding the actual hosting infrastructure.
- - Controlled Access: Each victim is provided unique login credentials. Malware-laden archive files are delivered only upon successful credential input, allowing attackers to track individuals and block unwanted visitors.
This controlled access approach highlights the group's operational security and persuasive camouflage typical in state-sponsored attacks.
Evolving Tools: MiniJunk and MiniBrowse
Nimbus Manticore's latest toolset comprises two primary focuses. MiniJunk enables attackers to maintain prolonged covert access to victims' systems, while MiniBrowse is designed to covertly steal sensitive information. These tools are continuously updated to evade security scans, ensuring sustained functionality and guaranteed espionage capabilities over the targeted organizations.
Concurrent Activity Clusters
In addition to MiniJunk, CPR has identified another parallel activity cluster previously reported by PRODAFT, characterized by less sophisticated techniques and payloads without the advanced obfuscation found in MiniJunk. This group also employs similar spear-phishing tactics and fake recruitment site strategies. They often pose as HR representatives, initially contacting victims through LinkedIn or other professional platforms before shifting to email communications, luring them to customized job portals.
Check Point Harmony Email & Collaboration has successfully thwarted one such attack against an Israeli telecom company, confirming that both activity clusters share fraudulent tactics and a broad range of targets.
Impact and Targeted Industries
Expansion into Europe
While Nimbus Manticore consistently targets the Middle East, especially Israel and the United Arab Emirates, recent activities indicate an increased focus on Western European countries like Denmark, Sweden, and Portugal.
Concentrated Targeting in Specific Industries
- - CPR identified a correlation between the content of malware-distributing websites and targeted sectors. For example, a fake job portal impersonating a telecommunications company was aimed at employees within that industry.
- - Analysis reveals prevalent targeting in key areas such as the telecommunications sector (notably satellite communications), defense contractors, aerospace industry, and airlines, aligning with the IRGC’s intelligence collection priorities.
Defensive Measures Against Nimbus Manticore
Amidst their evolving attack strategies over the past year, Nimbus Manticore has continually adapted its malware delivery methods, evolving from Minibike to MiniJunk and expanding MiniBrowse while refining its spear-phishing techniques. This indicates a remarkable resilience and stealth, particularly as geopolitical conflicts intensify.
To counteract these threats, organizations must deploy protective measures before attacks reach employees. Check Point Harmony Email & Collaboration provides the necessary safeguards by detecting and preventing spear-phishing attempts, fake job portals, and malicious attachments linked to Nimbus Manticore campaigns. This multi-layered security approach includes:
- - Check Point Harmony Email & Collaboration: Detecting and preventing spear-phishing, fake job sites, and malicious attachments at the email and collaboration tool level, obstructing initial attack vectors.
- - Harmony Endpoint: Protecting devices when advanced malware infiltrates, offering defense even if initial email defenses are bypassed.
- - Quantum Network Security: Constructing barriers to block malicious traffic at the network perimeter, preventing the download of malicious files, C2 communications, and data exfiltration.
As CPR continues to monitor Nimbus Manticore's activities, they will provide insights to bolster resilience against state-sponsored attack campaigns. For more detailed analysis, refer to CPR's comprehensive technical reports on this pressing issue.
For further information on Check Point Research and its initiatives, you can visit their official blog.
- ---
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.