
Global Surge in Cyberattacks Exploiting SharePoint Zero-Day Vulnerability Highlights Urgent Security Needs
Rising Cyber Threats: The SharePoint Zero-Day Vulnerability
Check Point Research (CPR) has recently unveiled troubling findings regarding a significant spike in cyberattacks linked to a severe zero-day vulnerability found within Microsoft SharePoint. Identified as CVE-2025-53770, this vulnerability poses a serious risk and has been actively exploited worldwide, primarily targeting on-premises Microsoft SharePoint systems.
Overview of the Threat
Named 'ToolShell', this aggressive cyber campaign grants unauthorized access to on-premises SharePoint Servers, dramatically increasing risks for organizations. The first signs of exploitation were detected on July 7, 2025. Since then, CPR has monitored numerous attacks, particularly against government agencies and industries such as telecommunications and software in North America and Western Europe.
This alarming trend showcases the vulnerability of many server infrastructures that have not been promptly patched. The attackers have also taken advantage of known vulnerabilities in Ivanti Endpoint, amplifying the threat further.
Key Findings
The recent attacks extensively utilized the critical remote code execution (RCE) vulnerability associated with SharePoint, allowing threat actors to execute arbitrary code with full access rights, even without authentication. Microsoft has issued official guidance regarding this vulnerability, while the Cybersecurity and Infrastructure Security Agency (CISA) reinforced the need for immediate remedial actions, especially following the release of recent patches around July 20.
Here are some important observations from the CPR report:
- - The surge in exploit attempts started on July 7, 2025, with significant attacks targeting major government bodies in Western Europe observed on July 18 and 19.
- - Specific IP addresses involved in these attacks include:
- 107.191.58.76
- 96.9.125.147
- - One of the malicious IPs was also associated with the Ivanti EPMM vulnerability chain (CVE-2025-4427 and CVE-2025-4428).
The attack vectors employed in these incidents featured custom web shells that facilitated payload parsing and deserialization attacks, illustrating the complex nature of the threat aimed at critical sectors such as government, software, and telecommunications.
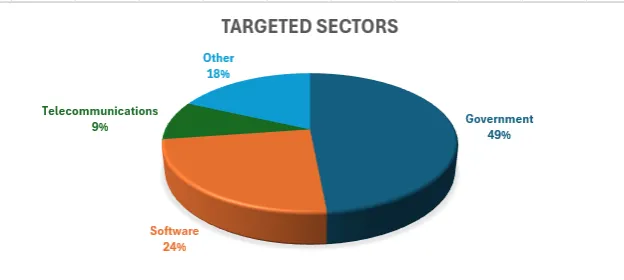
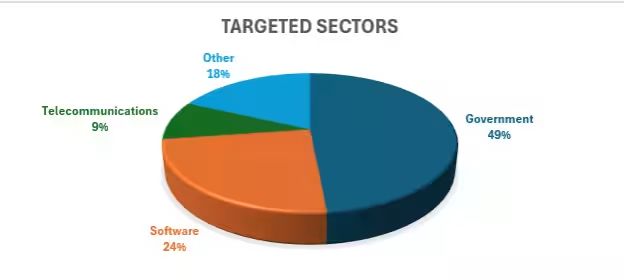
Targeted Sectors
In terms of affected sectors, the breakdown is as follows:
- - Government Agencies: 49%
- - Software Industry: 24%
- - Telecommunications: 9%
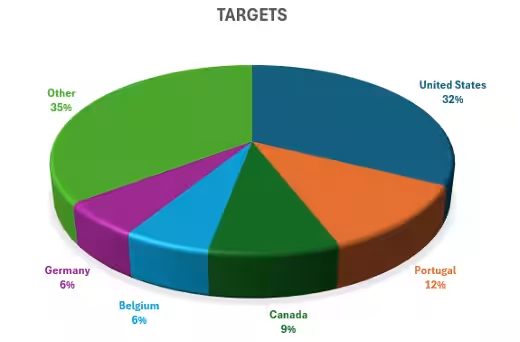
Predominantly, organizations managing on-premises SharePoint systems in North America and Western Europe have been significantly impacted by these attacks.
Security Implications
This alarming outbreak emphasizes the critical need for robust monitoring and defense mechanisms over legacy and on-premises infrastructures. Threat actors are rapidly exploiting unpatched vulnerabilities, such as CVE-2025-53770, and chaining them with previously known vulnerabilities to gain initial access and escalate privileges effectively.
These series of exploits highlight the growing trend of targeting organizations that manage sensitive data and critical systems through specialized attacks leveraging SharePoint zero-day vulnerabilities.
Recommended Protective Measures
To mitigate the risks posed by the SharePoint vulnerability and related threats, organizations should consider implementing the following protective measures:
1. Ensure that the Anti-Malware Scanning Interface (AMSI) is activated.
2. Regularly rotate the ASP.NET machine keys for SharePoint Server.
3. Implement Check Point's Harmony Endpoint to block post-exploitationactivities on servers.
4. Where possible, utilize Private Access tools to restrict internet access to SharePoint Servers.
5. Update Check Point's Quantum Gateway IPS package 635254838, ensuring protection is set to 'prevent' and conducting traffic inspection for the SharePoint Server.
6. Report any signs of suspicious activity to Check Point Incident Response for further assistance.
In conclusion, organizations must take immediate steps to address these vulnerabilities and safeguard against the increasingly sophisticated methods employed by cybercriminals.
About Check Point Research
Check Point Research excels in offering current cyber threat intelligence to clients and the threat intelligence community. The team analyzes data on global cyberattacks sourced from Check Point's ThreatCloud AI, aiding in the development of effective protection solutions.
With a strong workforce of over 100 analysts and researchers, CPR collaborates with security vendors, law enforcement, and CERT organizations to enhance cybersecurity measures globally.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.