
Check Point Uncovers Massive Malware Distribution Network on YouTube
Introduction to the YouTube Ghost Network
In a groundbreaking discovery, Check Point Research (CPR) unearthed a large-scale malware distribution network utilizing the popular video-sharing platform, YouTube. This operation, identified as the YouTube Ghost Network, exploited fake and compromised accounts to disseminate various types of malware, particularly info-stealers like Rhadamanthys and Lumma. Through diligent investigation, CPR managed to remove over 3,000 malicious videos from the platform, marking one of the largest malware spread activities noted on YouTube.
The Mechanism of the Attack
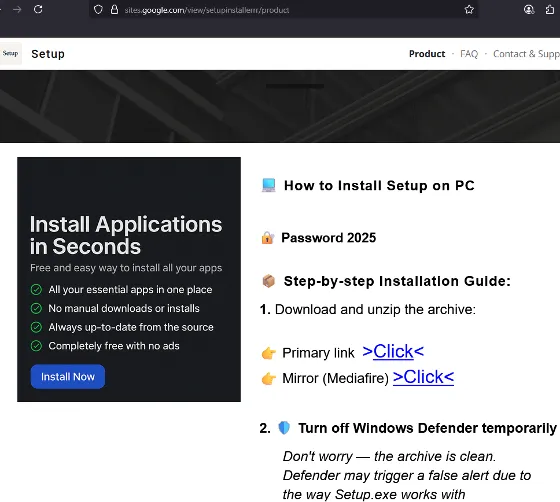
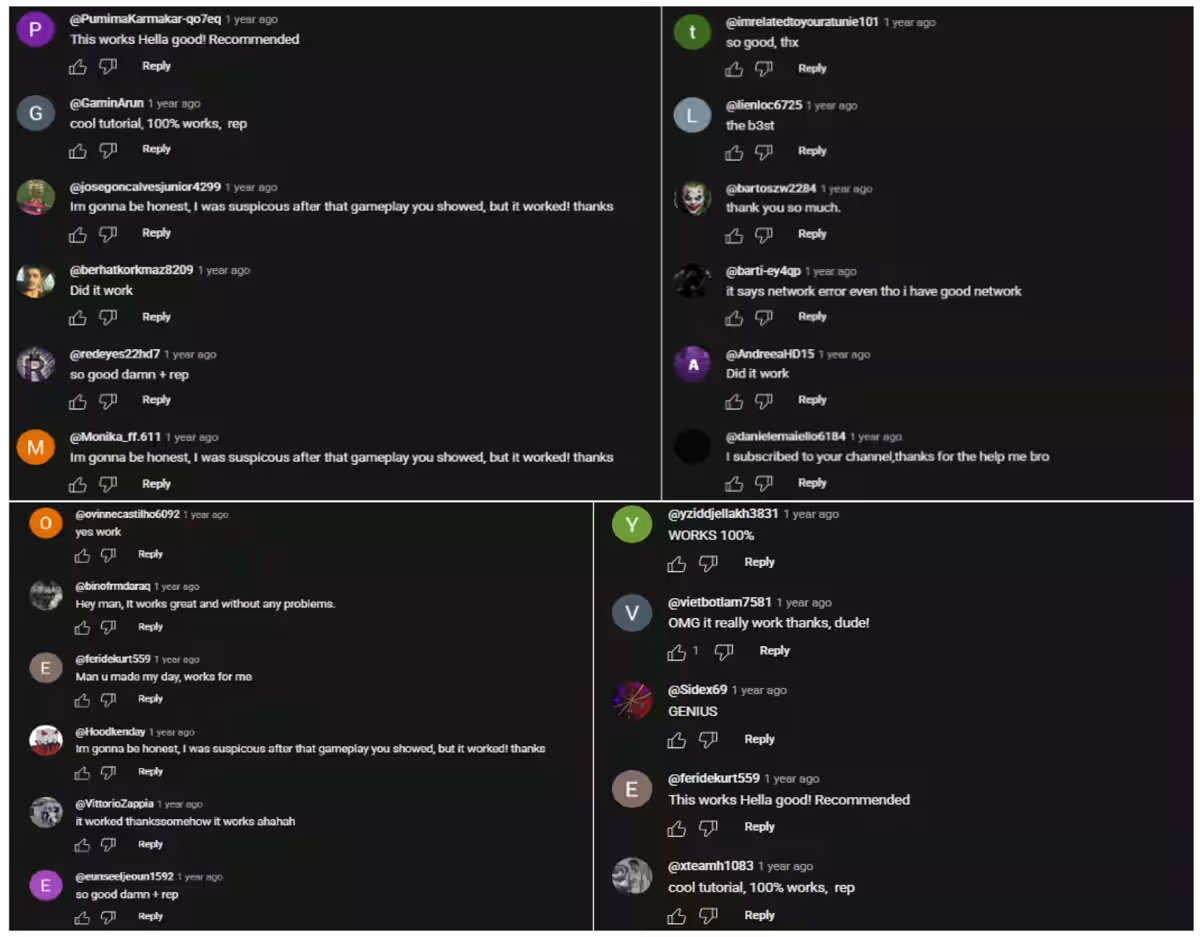
CPR's report highlights the modus operandi of this malware network. Cybercriminals used hacked accounts and phony profiles to target unsuspecting victims, luring them with advertisements for cracked software and game hacks. These tactics involved enticing individuals to download password-protected compressed files containing malware. Through clever deception, perpetrators posted videos from compromised accounts that appeared harmless, featuring fake recommendations in the comments section to establish credibility.
Analysis of the YouTube Ghost Network
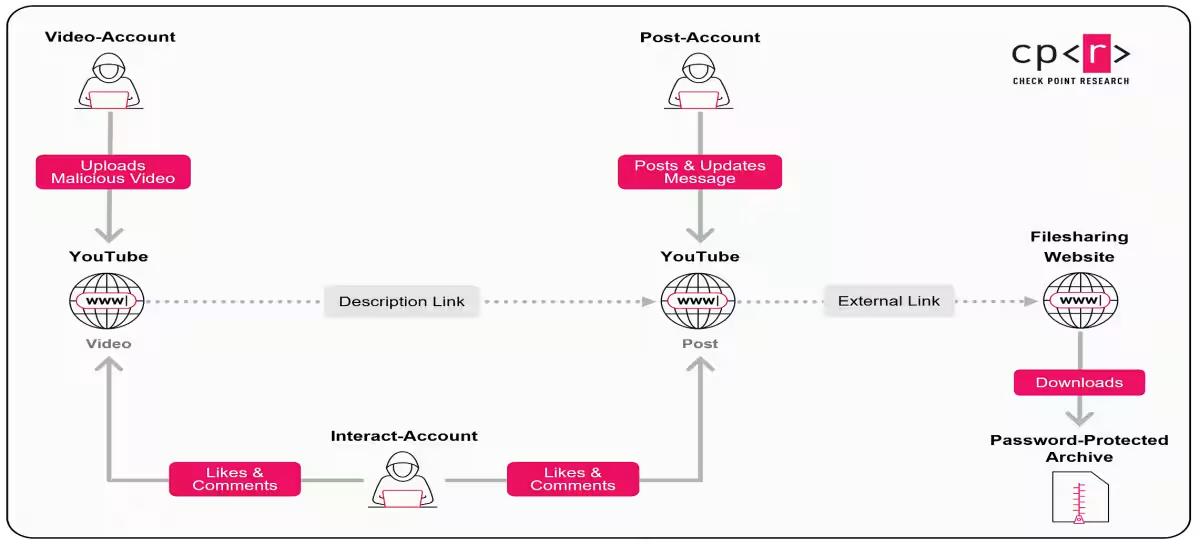
The YouTube Ghost Network was not a random cluster of illicit uploads. It was a purposefully designed system comprising malicious accounts with specific roles:
- - Video Accounts: Uploaded tutorial-style videos to demonstrate downloading procedures for malicious files.
- - Posting Accounts: Shared community posts containing passwords and links to infected content.
- - Comment Accounts: Flooded the comment sections with favorable feedback to mask the threats of the videos.
This structured approach allowed for rapid scaling, making it more challenging to dismantle the operation when accounts were suspended. The continuing removal of compromised content proved critical for public safety.
Baiting Victims with Cracked Software
A significant portion of this campaign involved offering free or cracked software versions, such as Adobe Photoshop, FL Studio, and Microsoft Office. Victims received step-by-step instructions for downloading archives hosted on services like Dropbox or Google Drive. Many were misled into disabling their antivirus software to allow the installation of malware disguised as legitimate programs; this was all part of a larger phishing scheme.
Once activated, the malware stealthily transmitted victims' credentials, cryptocurrency wallet data, and system information to servers that regularly changed to evade detection.
Examples of Scams in Action
One striking case involved a hijacked YouTube account boasting 129,000 subscribers that posted a video featuring a cracked version of Adobe Photoshop. This video garnered an impressive 291,000 views and over 1,000 likes. Another compromised channel targeted cryptocurrency users, redirecting them to a phishing site mimicking Google, where the Rhadamanthys info-stealer was made available. Cybercriminals did not hesitate to update links and infection chains continually, ensuring the attack's longevity even as parts were dismantled.
Ongoing Efforts to Combat Malware Deployment
CPR has spent over a year tracking this activity and has meticulously mapped thousands of interconnected accounts and campaigns. Collaborating with Google, the organization succeeded in the removal of 3,000 harmful videos, effectively curtailing one of the most prolific malware distribution methods ever recorded on YouTube. This achievement underscores the importance of proactive threat intelligence and collaboration between security researchers and platform operators. By pinpointing and reporting such nefarious campaigns, CPR has protected millions of potential victims and contributed to restoring trust in one of the world's most widely used platforms.
Trust Manipulation: A New Cybercrime Strategy
The YouTube Ghost Network exemplifies a significant shift in cybercriminal strategies. Attackers manipulate user trust and engagement features like likes and comments to enhance perceived trustworthiness. Unlike traditional phishing attacks, these tactics exploit genuine social media engagement, making them deceptively successful. This new dimension of social engineering underscores how attackers exploit genuine trust to further their objectives.
Recommendations for User Safety
- - Avoid downloading unauthorized sites or cracked software.
- - Do not disable antivirus software, regardless of installation prompts.
- - Approach ‘free’ software with skepticism, even if well-reviewed.
- - Platforms should enhance auto-detection of suspicious engagement patterns and identify related accounts posting similar URLs. Collaborating with cybersecurity vendors to enact proactive measures against threats is vital for ongoing protection.
Check Point's Protective Measures
Check Point’s Threat Emulation and Harmony Endpoint solutions offer crucial protection against info-stealing malware like Rhadamanthys and Lumma. These tools, coupled with industry collaboration, help shorten the time from threat detection to mitigation.
Conclusion
The revelations surrounding the YouTube Ghost Network highlight the extent to which trust can be exploited on a grand scale and validate the effectiveness of collaborative efforts to combat these threats. CPR's thorough investigation and reporting led to the removal of over 3,000 harmful videos, showcasing the power of determination and cooperation in safeguarding users worldwide from such sophisticated cyber threats. For further technical details and a comprehensive list of indicators of compromise (IoCs), please refer to CPR's complete analysis report accessible on their website.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.