
Check Point Research Unveils Malware Trends for April 2025
Overview of Malware Trends in April 2025
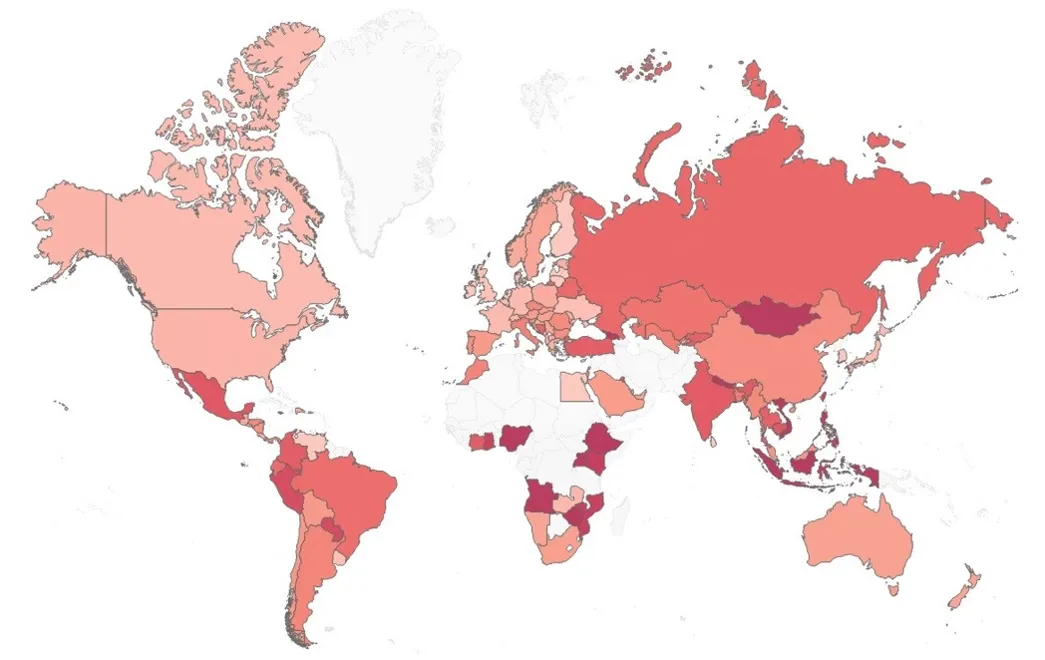
Check Point Research has released its latest Global Threat Index for April 2025, revealing critical insights into the malware landscape. For the fifth consecutive month, FakeUpdates emerged as the dominant malware, causing disruptions for 8% of organizations globally. Following closely are Remcos and AgentTesla, both posing significant threats. Researchers have also uncovered intricate multi-stage attacks distributing AgentTesla, Remcos, and Xloader, showcasing an alarming trend in cybercrime where commodity malware intersects with advanced delivery techniques.
The Rising Threat of FakeUpdates
FakeUpdates, also known as SocGholish, has become a frequent tool for cybercriminals since its discovery in 2018. This downloader-type malware spreads through infected websites, tricking users into installing fraudulent browser updates. It's suspected to be linked to the notorious hacking group Evil Corp. The sophistication of its operational tactics reveals a trend towards complexity in cyber attacks, further emphasized by the recent campaigns deploying encoded scripts and legitimate processes to evade detection.
Trends in Multi-Stage Attacks
The recent surge in multi-stage attacks begins with phishing emails disguised as order confirmations, enticing victims to open a 7-Zip archive. These archives contain .JSE files that initiate Base64-encoded PowerShell scripts, executed through .NET or AutoIt-based files. The final stages see the malware injected into legitimate Windows processes, significantly increasing stealth and evasion potential. Check Point's Director of Threat Intelligence, Lotem Finkelstein, underscores the evolving nature of cyber threats, urging organizations to adopt a proactive, AI-driven approach to threat mitigation.
Malware Family Rankings in April
In the domestic sphere, the most active malware families, as ranked in April, include:
- - Remcos (4.44%): This remote access Trojan (RAT) targets victims through phishing campaigns. It circumvents Windows security mechanisms like User Account Control (UAC), making it a robust tool for attackers.
- - Androxgh0st (2.50%): This Python-based malware scans for exposed credentials concerning AWS, Twilio, and other services via public .env files, it exploits the Laravel PHP framework for further malicious activity.
- - FakeUpdates (2.22%): This downloader malware continues to pose risks through deceptive installations of fake browser updates, showcasing its persistent threat.
Global Malware Landscape
Globally, FakeUpdates continues to lead, impacting 6% of organizations. Remcos and AgentTesla maintain their positions, with each affecting 3% of the global infrastructure. The adaptability of these malware, particularly FakeUpdates and Remcos, can’t be overstated, illustrating a shifting narrative in the cyber threat landscape from simple commodity malware to sophisticated, multi-faceted attacks.
Ransomware Activity in April
The ransomware sector remains volatile with Akira being the most prominent group, involved in 11% of reported attacks. Following closely are SatanLock and Qilin, each accounting for 10%. Akira targets both Windows and Linux systems, employing advanced encryption methods akin to the infamous Conti v2. Meanwhile, SatanLock and Qilin exemplify the rapid evolution of emerging ransomware actors, underlining the need for vigilance and adaptive defense measures.
Mobile Malware Digest
April’s mobile malware threats are led by Anubis, a multi-functional banking Trojan evolving to intercept SMS-based one-time passwords and conduct various malicious activities. AhMyth and Hydra follow closely, both aiming to exploit user credentials through legitimate-looking applications and interactions in mobile banking contexts.
Sector-Wise Impact
The education and research sector remains the most targeted globally, followed by government and military sectors and telecommunications, illustrating a consistent pattern of attack prioritization.
Recommendations for Organizations
To combat these sophisticated malware campaigns, organizations must prioritize proactive measures. This encompasses robust phishing awareness training for employees, stringent patch management practices, and leveraging advanced threat mitigation solutions such as Check Point's Threat Emulation to halt unknown threats before they infiltrate networks. A combination of these strategies can create a multi-layered defense that is essential in today’s rapidly evolving threat landscape.
Conclusion
In April 2025, the notable rise of multi-stage attacks employing commodity malware showcases a pressing need for adaptive security strategies. FakeUpdates leads the charge in global infections, while developments in mobile threats like Anubis signal a continued demand for vigilance. The educational sector remains a focal point for attacks, highlighting the necessity for tailored threat intelligence and defense approaches across various industries. Check Point’s AI-driven insights continue to guide effective responses to these emerging threats, demonstrating the critical importance of a proactive cybersecurity posture in safeguarding information assets.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.