
Understanding the ZipLine Phishing Campaign and Its Threats to U.S. Manufacturing
The Emergence of the ZipLine Phishing Campaign
In recent reports, Check Point Research (CPR) unveiled an advanced phishing campaign dubbed "ZipLine," significantly posing threats to the U.S. manufacturing and supply chain industries. As a leader in cybersecurity solutions, Check Point Software Technologies has recognized the ZipLine campaign as one of the most refined social engineering attacks of recent times, urging businesses to remain vigilant.
Overview of the ZipLine Campaign
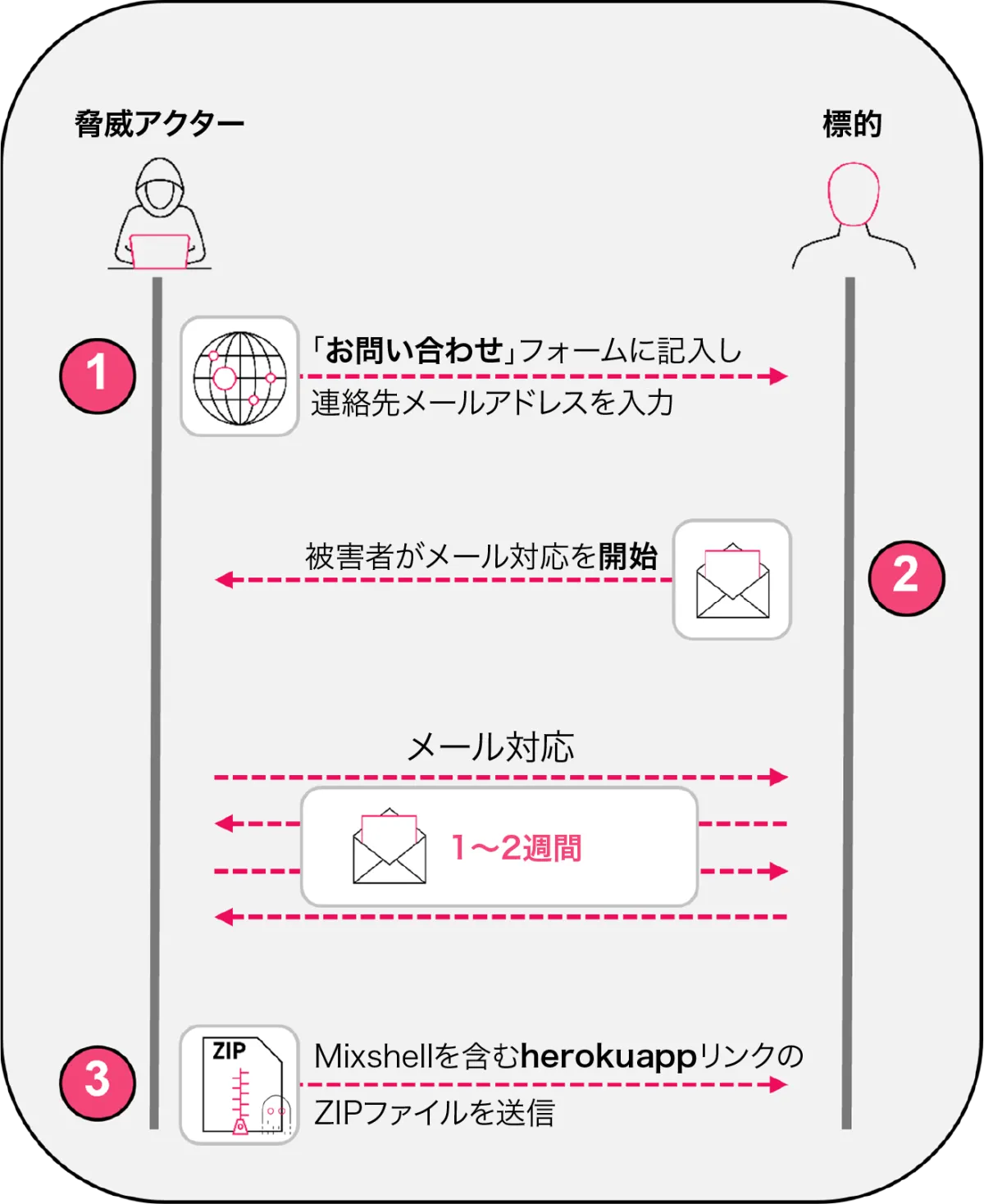
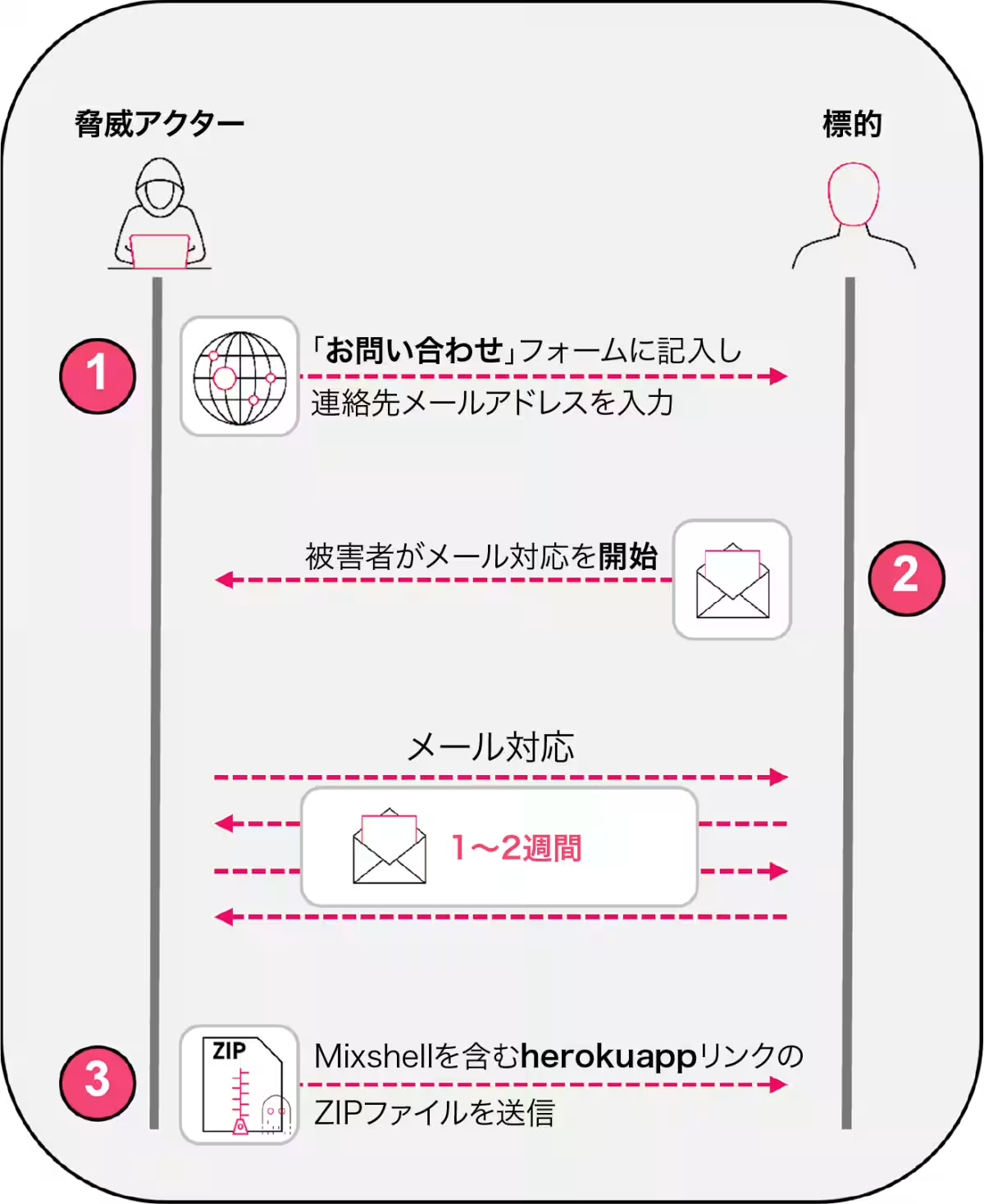
The ZipLine phishing campaign diverges from traditional phishing tactics. Attackers initiate contact through enterprise contact forms, prompting their targets to respond first, effectively flipping the usual phishing script. This reverse engineering approach has proven highly effective in tricking victims into engaging with attackers. Once the communication starts, attackers often engage in professional exchanges over several weeks, eventually sending malicious zip files after requesting non-disclosure agreements (NDAs).
The Payload and Its Functionality
Within the malicious payload, named MixShell, resides a memory-resident malware employing DNS tunneling and HTTP fallback to maintain connections and execute attacker commands. The second wave of attacks exploits fake internal AI transformation assessments, masquerading as legitimate requests for internal evaluations to further lure potential victims.
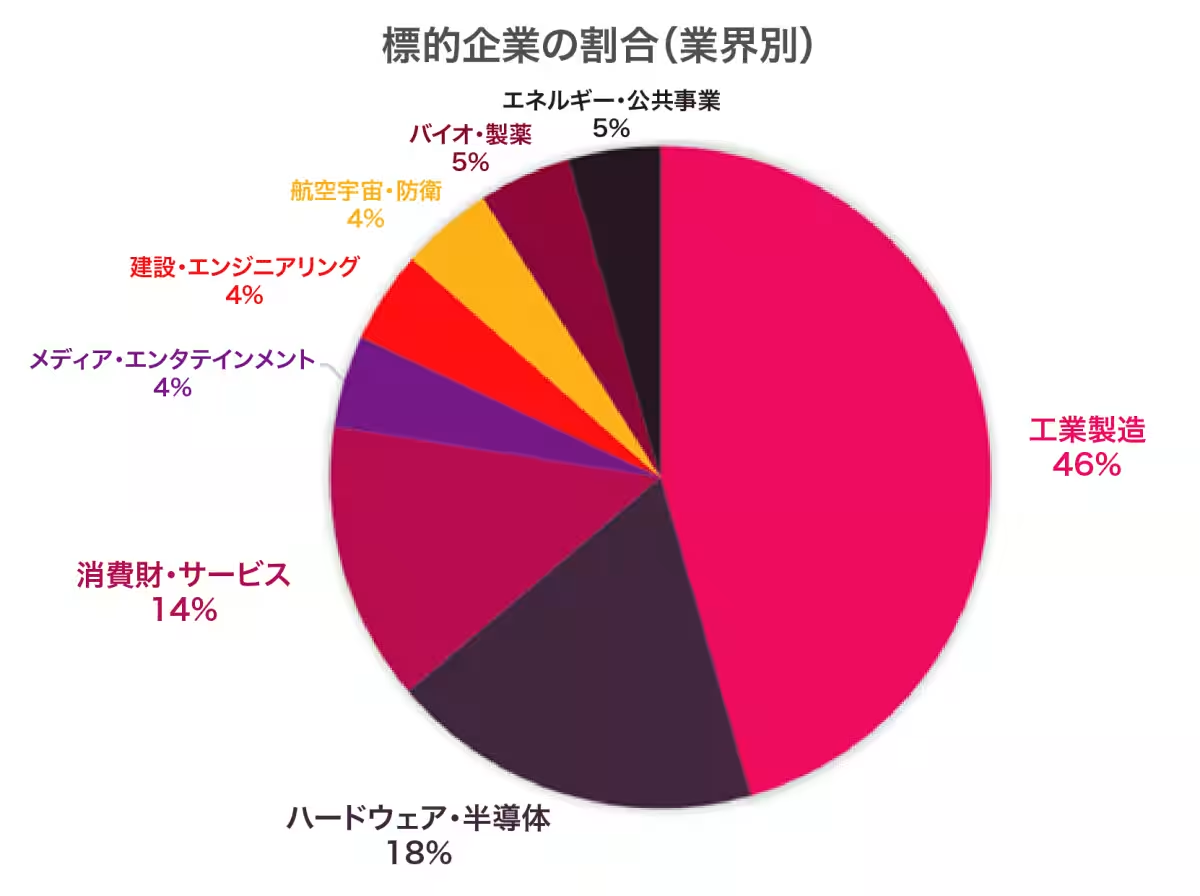
Targeted Sectors and Potential Consequences
Primarily, the U.S. manufacturing and key supply chain companies are at risk. The potential repercussions of these attacks are grave: theft of intellectual property, ransomware extortion, financial fraud through account takeovers and Business Email Compromise (BEC) attacks, and significant disruptions within crucial supply chains.
The Mechanisms of Deception
The campaign's success is attributed to a long-term focus on building professional rapport through persistent interactions. Attackers often pose as legitimate LLCs, creating fake websites to establish credibility before delivering threats hidden in weaponized ZIP files. These files contain both harmless documents and harmful LNK files, from which PowerShell scripts are extracted and executed entirely within memory, deploying MixShell to carry out its functions.
AI as a Cover Story
Recent observations from CPR highlighted the second wave of marketing the ZipLine emails under the pretext of AI transformation assessments. These phishing attempts often appear as internal surveys concerning AI efficiency and cost reductions within organizations. Although malware isn't directly identified in these AI-themed emails, they reveal the infrastructure setup that can be used for subsequent attacks by leveraging incremental ZIP delivery models and in-memory execution.
Why ZipLine Demands Attention
The ZipLine phishing campaign's focus on critical industries raises alarms about potential disastrous outcomes for affected organizations. Here are some notable risks:
- - Intellectual Property Theft and Ransomware: The threat of production line stoppages and data breaches is significant.
- - Financial Fraud: Risks associated with credential theft, bank accounts compromise, and large financial losses grow with BEC attacks.
- - Supply Chain Disruptions: Instabilities created could ripple through numerous industries, impacting essential product and component production.
Defense Recommendations
Organizations are encouraged to enhance their defenses through several strategies:
- - Monitoring Inbound Channels: Elevate scrutiny over contact forms, collaboration tools, and seemingly innocent avenues that could serve as infiltration points.
- - Increasing User Awareness: Provide training for employees, especially in procurement and supply chain management, about social engineering tactics and malicious file types used by scammers.
- - Strengthened Due Diligence for New Vendors: Implement verification processes through independent sources for new vendors.
- - Attachment and Link Inspections: Ensure comprehensive security scans of archive file contents.
- - Countermeasures for Account Takeovers and BEC Attacks: Apply Multi-Factor Authentication (MFA) and monitor for suspicious login behavior.
Check Point's Protective Technologies
Check Point's Harmony Email & Collaboration solution offers advanced protection against phishing and social engineering attacks like ZipLine. Key features include:
- - AI-Powered Phishing Prevention: Analyzes context and communication patterns instead of relying solely on message filters.
- - Threat Emulation: Blocks malicious attachments such as weaponized ZIP files.
- - Real-Time URL Protection: Prevents access to phishing links.
- - Behavioral Analysis: Detects account compromises and BEC attempts.
- - Data Loss Prevention (DLP): Safeguards sensitive proprietary information and supply chain data.
Conclusion
ZipLine's innovation in phishing tactics displays how attackers leverage web forms, prolonged email interactions, and AI-themed emails to create severe risks for U.S. manufacturing and supply chain sectors. Organizations must fortify their defenses with comprehensive strategies and use tools like Harmony Email & Collaboration to stay ahead of these sophisticated attacks. For detailed insights on the ZipLine phishing campaign, explore CPR's technical analysis report.
Topics Business Technology)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.