
Netskope Threat Labs Unveils New Campaign Distributing LegionLoader Using Fake CAPTCHA Techniques
Unraveling the Latest Attack Campaign by Netskope Threat Labs
Netskope Threat Labs, the research arm steering the security and networking industry, has recently unveiled a menacing campaign adept at distributing the loader-type malware known as LegionLoader. This nefarious scheme maliciously exploits fake CAPTCHA systems and CloudFlare’s Turnstile to mislead users into downloading malware, particularly through the guise of legitimate documents.
Key Findings
The analysis by Netskope Threat Labs led to the discovery of a new drive-by download attack campaign. It utilized fake CAPTCHA and the alternative verification method offered by CloudFlare Turnstile, marking the distribution of LegionLoader’s payload.
In this elaborate infection chain, legitimate VMware-signed applications are misappropriated for the side-loading of malicious DLLs. These nefarious DLLs execute the LegionLoader payload, ultimately leading to the installation of harmful browser extensions.
Moreover, a custom algorithm was employed to obfuscate the shellcode for the LegionLoader, making it harder to detect and analyze.
Overview
Netskope Threat Labs has been diligently tracking multiple phishing and malware campaigns targeting users searching for PDF documents since February 2025. These attacks trick victims into clicking on malicious links, steering them towards harmful websites, and prompting them to download malware.
Through tracking these threats, the lab revealed similar malicious campaigns employing fake CAPTCHA and CloudFlare Turnstile in their methods, particularly manifesting the spread of LegionLoader to install harmful browser extensions. Notably, over 140 of Netskope’s customers, spanning various industries including technology and financial services, mainly from North America, Asia, and Southern Europe, were targeted in this campaign.
This article will encompass an overview of the entire infection chain related to this specific attack campaign, detailing:
- - Evasion techniques employed
- - How LegionLoader executes on victim machines
- - The process of loading malicious browser extensions for the theft of sensitive information.
Initial Infection Chain: PDF Download and Fake CAPTCHA
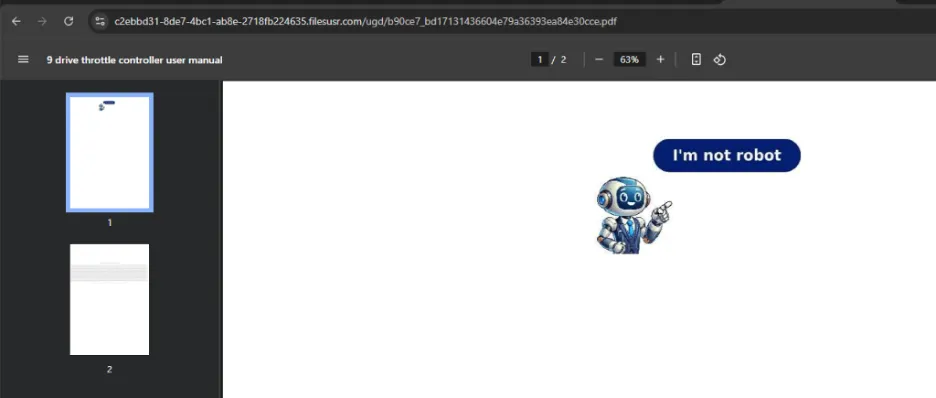
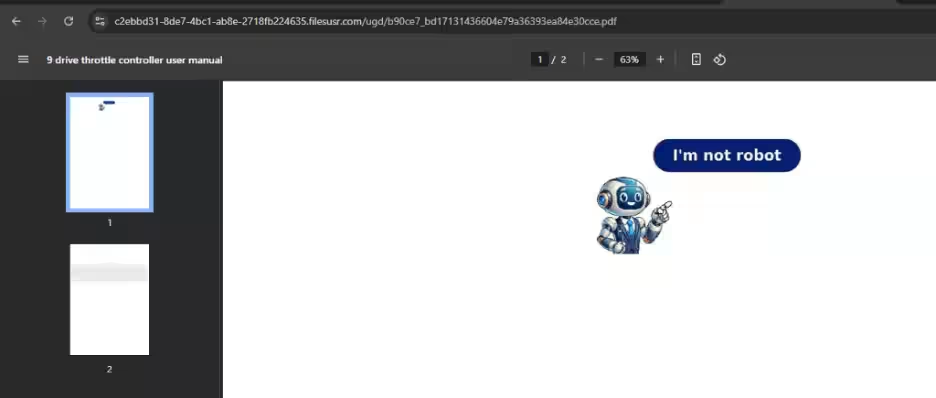
The infection process begins when victims are lured to specific documents through searches, leading them to malicious websites. The initial payload spreads through drive-by downloads. The downloaded document contains a CAPTCHA image, enticing victims to click and subsequently redirecting them to the CloudFlare Turnstile CAPTCHA. This transition leads to a browser notification page.
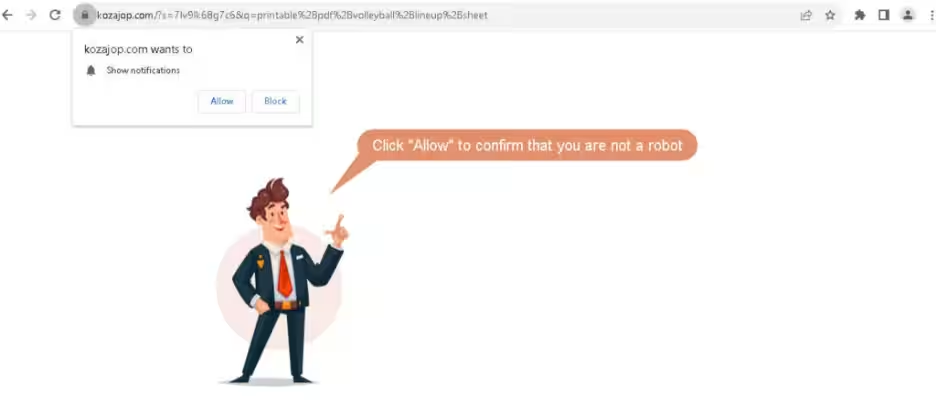
The Role of the Fake CAPTCHA
For the infection chain to progress, victims must enable notifications in their browsers. A malicious page prompts them to grant these notifications. If users either block the request or use an unsupported browser, they are redirected to download benign applications like 7-Zip or Opera. Conversely, should they consent to receiving notifications, they face a second CloudFlare Turnstile CAPTCHA, and once completed, they are redirected to a page offering instructions on how to download the document they initially sought.
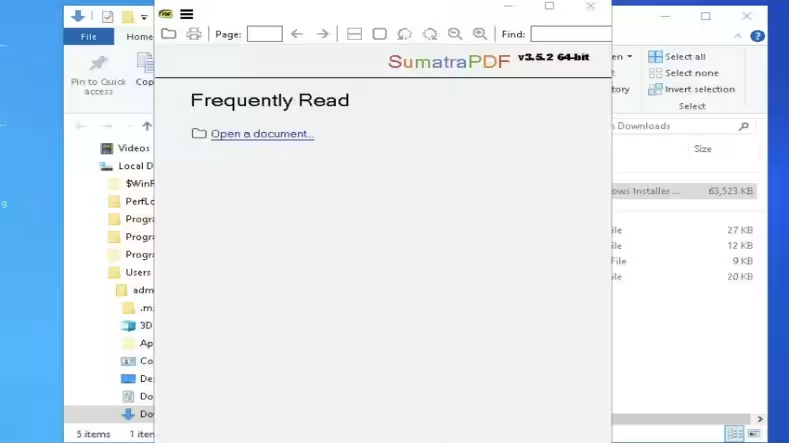
Instructions on this page urge users to press Win+R to open the Windows Run window, paste in content copied to the clipboard via Ctrl+V, and hit enter. This clipboard content consists of a command prompting a cURL execution to download an MSI file. The subsequent execution of this MSI file allows the initial payload to activate.
Infection Chain ②: Execution of the MSI File
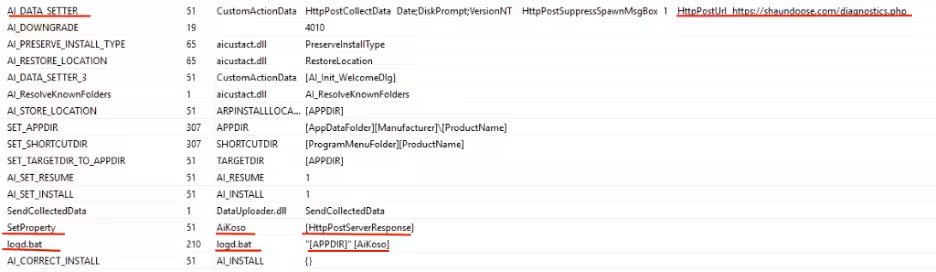
When the MSI file is executed, it registers an application named “Kilo Verfair Tools,” embedding numerous custom actions defined in the CustomActions table, streamlining the integration of custom code and data into the installation process.
To evade suspicion, the MSI runs launcher.exe, executing the SumatraPDF application—a free and open-source document reader—which reinforces the victim's belief that they are merely trying to access the PDF they have been searching for.
Actions Embedded in the MSI File
Included in the CustomActions table is a batch script named logd.bat that performs two primary tasks:
1. Extracting multiple DLLs from a 7-zip archive named “jp_ver.dat” using a server-collected password.
2. Executing the mksSandbox.exe file which is signed with a VMWare certificate.
Infection Chain ③: Side-Loading Malicious DLLs
Upon the execution of mksSandbox.exe, DLL files within that directory undergo side-loading. The prominent file, “libcrypto-1_1-x64.dll,” serves as a counterfeit OpenSSL library, triggering the load and execution of the LegionLoader payload.
This obfuscation process incorporates unnecessary mathematical operations to mislead analysis, revealing that API Hammering methods were also deployed to avoid detection.
Infection Chain ④: The Initial PowerShell Payload
The LegionLoader server’s response encapsulates an encrypted PowerShell command executed on the infected machine. This script is programmed to download and run a subsequent payload, employing a series of obfuscation steps to obtain the necessary URL for the download.
Infection Chain ⑤: The Second PowerShell
The downloaded PowerShell script contains highly obfuscated payloads. To decode the payload, the script executes the decryption of a base64 encoded key and an initialization vector defined as variables. An AES decryption routine is established with CBC mode and PKCS7 padding to unveil the payload, which is executed using Invoke-Expression.
Infection Chain ⑥: The Addition of Malicious Browser Extensions
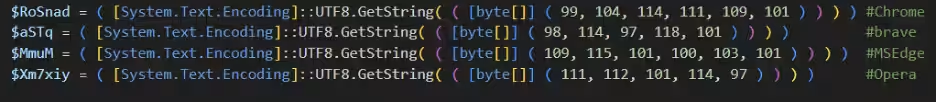
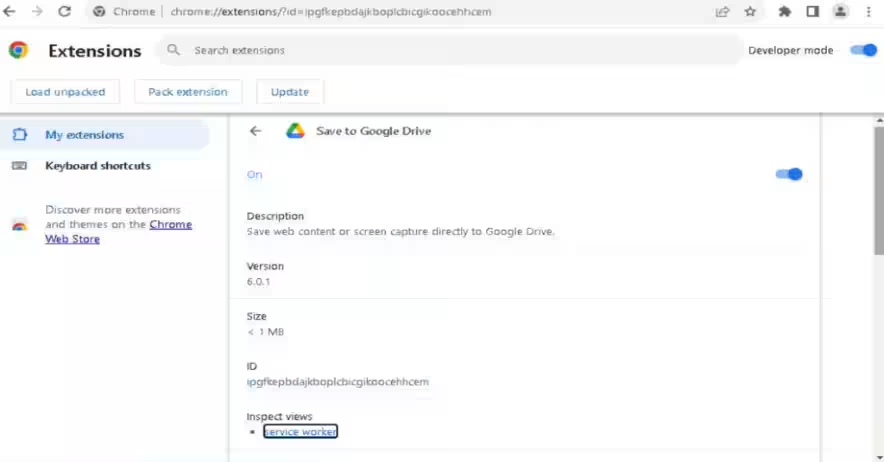
The decrypted payload extends to another PowerShell script, which adds a browser extension named “Save to Google Drive” resembling legitimate ones. This script obfuscates critical commands by prescribing them in byte arrays rather than plain text, delineating the targeted browser process name and “User Data” folder path, all encapsulated in byte arrays for transformation into strings as needed.
Once the browser process shuts down, the script generates folders and files for the browser extension. After completing all required changes, it restarts the previously terminated browser process, ensuring successful addition of the extension.
Features of the Malicious Extension
The malicious browser extension, endowed with extensive permissions stipulated in the manifest.json file, possesses capabilities for script execution, machine information gathering, and accessing a plethora of browser data, including clipboard-saved details. This extension subsequently garners sensitive information such as cookies and browsing history while monitoring user behaviors associated with Bitcoin, relaying related data back to the attackers.
Conclusion
Attackers persist in targeting users searching online for PDF documents. Through continuous monitoring, Netskope Threat Labs unveil campaigns where victims unwittingly execute LegionLoader malware by opening malicious PDF files, culminating in the unwanted installation of malicious browser extensions. This extension, targeting Chrome, Edge, Brave, Opera, collects sensitive information regarding users and their computers. Netskope Threat Labs remains vigilant, keeping tabs on such campaigns that target document-seeking users and endeavors linked to LegionLoader and its malevolent payloads.
About the Analysis Data
The analysis findings disseminated in this release were derived from a subset of anonymous usage data collected with prior consent from Netskope customers via the Netskope Security Cloud platform.
IOC (Indicators of Compromise)
All IOC identified in relation to this attack campaign can be reviewed in the Netskope GitHub repository.
This press release is based on a blog published at 4 PM US time on April 4, 2025.
About Netskope
Netskope leads the industry with cutting-edge security and networking technologies. No matter where people, devices, or data are located, we provide optimized access and real-time, context-based security, catering to both security teams and network teams' needs. Thousands of customers, including over 30 Fortune 100 companies, trust and leverage the Netskope One platform, proprietary zero-trust engine, and formidable NewEdge network. These solutions enable visualization of usage across all cloud, SaaS, web, and private applications, thus reducing security risks and enhancing network performance. For more information, visit netskope.com/jp.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.