
Surge in Vacation-Related Phishing Scams Ahead of Holiday Travel Season
Phishing Scams Rise as Summer Travel Approaches
As travelers begin to plan their much-anticipated summer vacations, a significant rise in vacation-related phishing scams has come to light, as warned by Check Point Research (CPR), a pioneer in cybersecurity solutions and global leader in the field. Leading up to this crucial season for the travel and hospitality industry, CPR highlighted that over 39,000 new travel-related domains were registered in May 2025, representing a 55% increase compared to the same period last year. Alarmingly, among these newly registered domains, 1 in 21 was identified as malicious or suspicious.
The surge in fraudulent web domains is not coincidental; cybercriminals are taking advantage of the peak travel planning period to execute sophisticated phishing scams. These scams are targeting consumers searching for hotel reservations and budget travel options, as well as hosts and property owners in the vacation rental sector. Tactics include fake login pages that mimic trusted services and well-crafted phishing emails designed to steal authentication and payment information.
A Wave of Cyberattacks in Hospitality
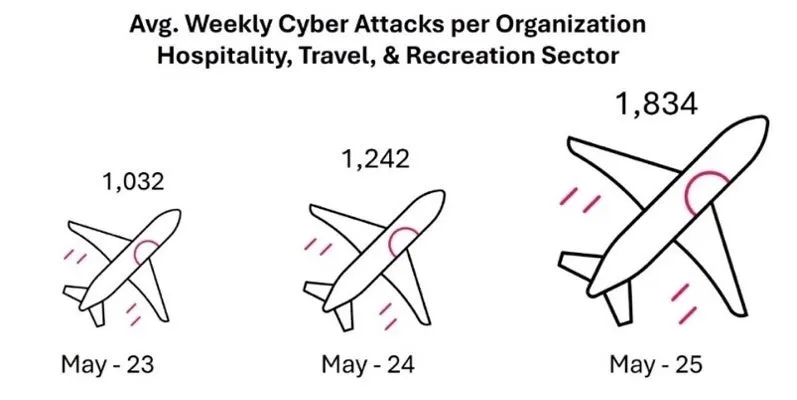
Simultaneously, the hospitality industry finds itself under unprecedented levels of cyberattacks. During the month of May alone, the average number of attacks per organization in this sector reached 1,834 per week, marking a 48% increase from May 2024 and a staggering 78% surge compared to two years ago. Such systematic attacks pose significant risks not just to individual travelers but also to major hotel chains, booking platforms, and essential businesses within the global tourism ecosystem.
Examples of Phishing Scams
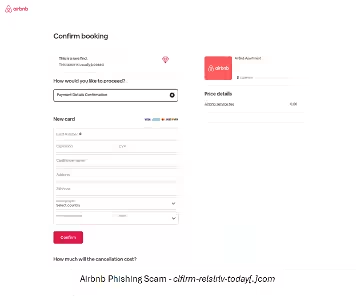
One alarming case identified by CPR involved a phishing site masquerading as Airbnb, operating under the domain clflrm-relslrlv-today.com. This scam site incorporated Airbnb's official logo and cleverly replicated a payment page to deceive users into entering sensitive information such as card numbers and security codes (CVV). Thankfully, this site has since been taken down.
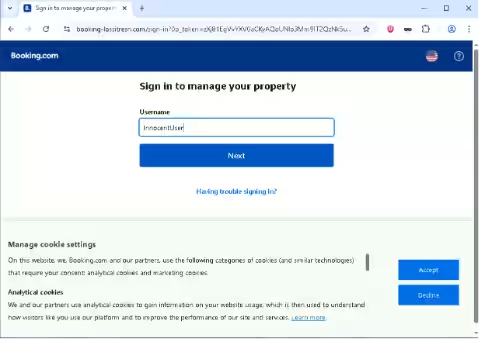
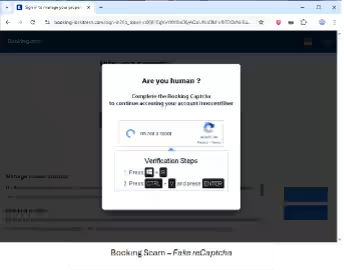
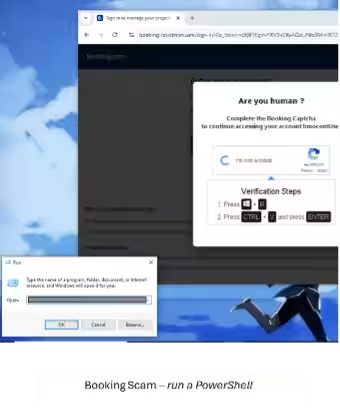
In another instance, a malicious phishing site designed to mimic Booking.com was uncovered. This site, registered in early May under the domain booking-lossitresn.com, utilized a fake reCAPTCHA, named ClickFix, and replicated the official property owner login page. As users entered their credentials, they were tricked with prompts suggesting further actions that executed malicious commands, allowing the download of a remote access trojan (RAT) onto victims' computers.
Targeted Phishing Campaigns
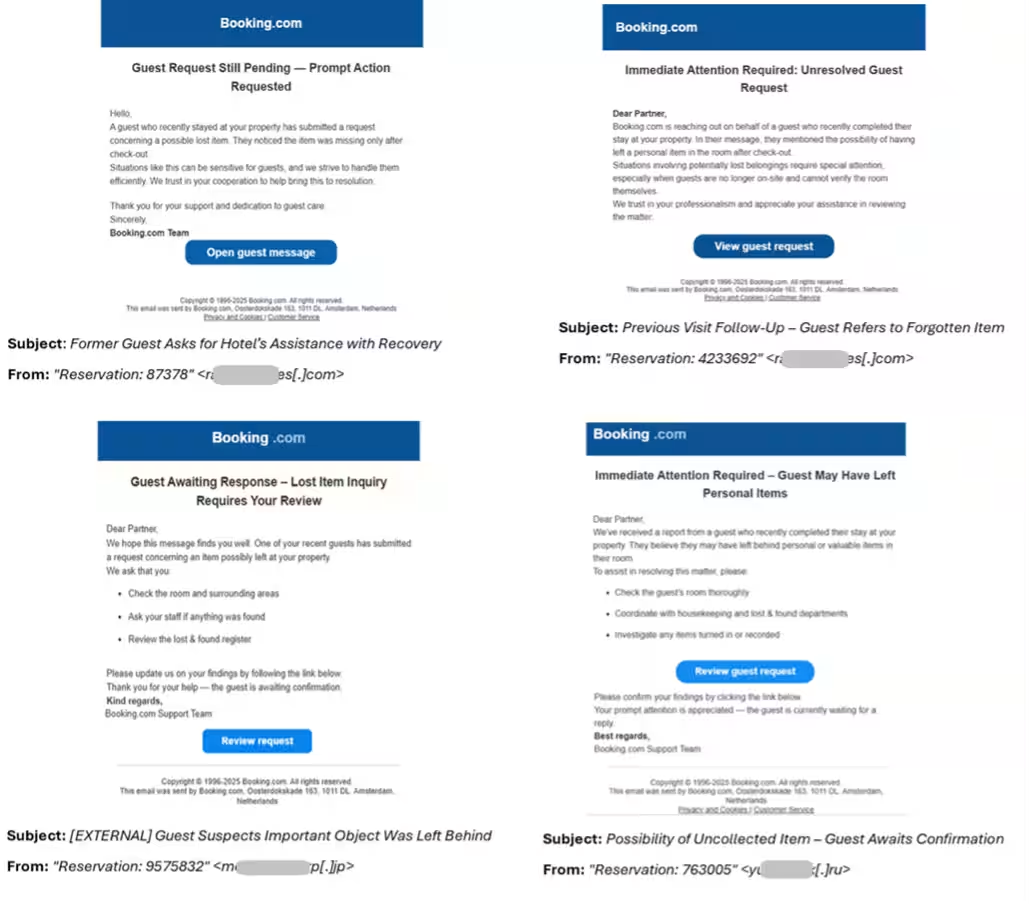
CPR also reported a new wave of phishing attacks aimed at property owners on Booking.com. Multiple identical emails were sent with subject lines suggesting inquiries from guests about lost items. These emails were designed to appear as if they came from a genuine corporate user with a hacked or spoofed email address. All emails prompted recipients to check on requests concerning lost items, guiding them to a phishing link leading to a harmful website that mimicked the Booking.com login page. This site was registered on May 26 and has since been taken down. The similarities across these phishing messages reflect an advanced use of generative AI tools by attackers, enhancing efficiency and improving social engineering tactics to evade detection by email security systems.
The increase in phishing domains and targeted attacks underscores the relentless nature of cybercriminals. Particularly during times when users are more predictable in their online behaviors, these perpetrators ramp up their attacks. For consumers eager to book their long-awaited trips, maintaining heightened vigilance is more important than ever.
Recommended Cybersecurity Measures for Travelers
To protect against these scams during the travel season, Check Point Research recommends the following cybersecurity measures:
1. Book Directly through Official Sites: Always input web addresses manually or use trusted apps, and avoid clicking on links in emails or messages.
2. Double-Check URLs: Look out for slight misspellings or unusual domains (.today, .info, etc.) characteristic of fraudulent sites.
3. Enable Multi-Factor Authentication (MFA): This adds an extra layer of security in case login information is compromised.
4. Be Cautious on Public Wi-Fi: Use a VPN when accessing sensitive information like bank accounts or booking sites.
5. Install Endpoint Security: Ensure comprehensive protection on mobile and desktop devices to detect phishing attacks and block malicious downloads in real time.
Whether you're planning your next getaway or managing sensitive customer data, proactive security measures are essential. As phishing scams grow more sophisticated and wait for their opportune moment, understanding the current threat landscape and knowing how to respond can make the difference between a safe holiday and a disastrous one.
As you embark on your summer adventures, ensure your vacation plans are secure and avoid letting a security incident spoil your well-deserved break.
This article is based on a blog post released on June 11, 2025 (U.S. Time).
About Check Point Research
Check Point Research provides the latest cyber threat intelligence to customers and the threat information community. By collecting and analyzing global cyber attack data stored in Check Point's ThreatCloud AI, they work to deter hackers while collaborating on the development of protective features integrated into their products. The team comprises over 100 analysts and researchers who partner with security vendors, law enforcement, and various CERT organizations to tackle cybersecurity challenges.
About Check Point Software Technologies
Check Point Software Technologies (https://www.checkpoint.com/) is the leading provider of digital trust, protecting more than 100,000 organizations worldwide with AI-driven cybersecurity solutions. Their Infinity Platform and open garden ecosystem achieve best-in-class security effectiveness in a prevention-first approach while reducing risk. The hybrid mesh network architecture centered on SASE integrates the management of on-premises, cloud, and workspace environments, offering flexibility, simplicity, and scalability to enterprises and service providers.
For further inquiries related to this release, please contact Check Point PR at [email protected].
Topics Consumer Technology)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.