
Reemergence of Iranian Threat Group Spear-Phishing Attacks Confirmed by Check Point Research
Rising Threats: Iranian Cyber Group Educated Manticore
In a disturbing turn of events, Check Point Research (CPR) has confirmed a resurgence of spear-phishing attacks orchestrated by the Iranian threat group known as Educated Manticore. This development comes amid heightened alerts from various U.S. agencies, including the FBI and DHS, regarding Iran's cyber operations.
What is Educated Manticore?
The group, also recognized by names such as APT42, Charming Kitten, and Mint Sandstorm, is believed to have links to the Islamic Revolutionary Guard Corps (IRGC). Historically, they have targeted prominent individuals globally, especially in academia and journalism. Recently, their focus has shifted towards Israeli officials, deploying sophisticated techniques to steal login credentials while also maintaining a much wider array of potential targets across various sectors.
Implications of Rising Tensions
With tensions escalating between Israel and Iran, Educated Manticore has intensified its activities. Their recent tactics include impersonating Israeli institutions, diplomats, and IT personnel to launch attacks. The sophisticated nature of these operations indicates an evolution in Iran's cyber strategy, showcasing a targeted approach that leverages a mixture of genuine persona details and precise timing across several forms of communication.
Elaborate Spear-Phishing Techniques
The recent attacks exemplify how Iran's cyber operations are becoming increasingly scaled and sophisticated. The group has been documented using fictitious personas linked to real organizations and employing intricate spear-phishing methods. These methods are designed to bypass multi-factor authentication by manipulating victims into revealing sensitive information.
Notable Targets
The current focus appears to be on influential individuals, particularly:
- - Renowned computer science and cybersecurity researchers from Israel.
- - Prominent journalists specializing in geopolitics and intelligence.
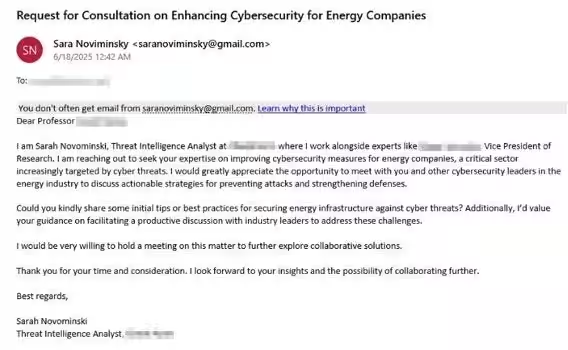
Although current activities are primarily targeting Israel, Educated Manticore has historically engaged in widespread international operations. Previous phishing endeavors include masquerading as prestigious media organizations such as The Washington Post and The Economist, aiming at journalists and researchers whose work intersects with Iranian strategic interests. Such efforts exemplify a consistent pattern of building trust through impersonation, leading to credential theft and extensive surveillance efforts.
Discovery of Fake Domains and Phishing Pages
CPR has reported uncovering dozens of custom phishing domains adapted to specific targets, which mimic popular services for information theft. Notably:
- - Eight phishing domains impersonating Google, along with additional domains for Outlook and Yahoo users, were identified.
- - These links have since been blocked, rendering them inaccessible.
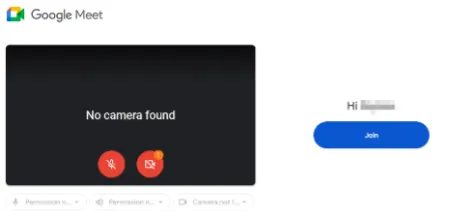
- - The group has been utilizing web-based meeting tools like Google Meet, crafted to redirect users to malicious servers via fake images that lead them to phishing attempts.
Communication Tactics
The attackers have adopted various methods to initiate contact, including:
- - Targeted phishing emails to academics and researchers.
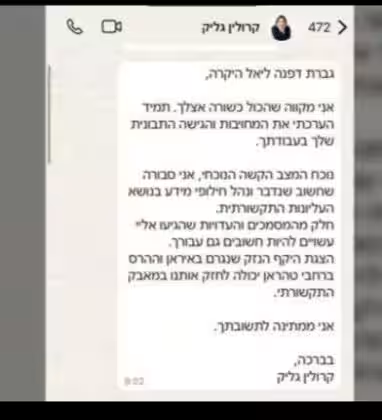
- - Direct messages on private platforms such as WhatsApp, impersonating high-profile figures, including former Israeli ambassadors.
Once initial contact is established, potential victims are directed to enter their credentials on counterfeit Google login pages, often pre-filled with their email addresses to increase the likelihood of success.
Advanced Social Engineering Attacks
Educated Manticore has displayed a remarkable ability to socially engineer victims into sharing their two-factor authentication codes, allowing them to completely hijack accounts. There have been instances where attackers lured individuals into believing they were scheduling in-person meetings in Tel Aviv, thus evidencing a chilling increase in cyber crimes spilling into physical realms.
Flexible Impersonation Strategies
The threat group exhibits impressive flexibility in their impersonation efforts, adopting identities from various levels of Israeli organizations, such as:
- - Mid-level managers at notable companies.
- - Staff at the Prime Minister's Office.
- - Experts associated with well-known technology firms.
Emails have been found to be grammatically correct and properly formatted, potentially generated using AI tools. However, subtle inconsistencies, such as slight misspellings, may provide opportunities to unveil the deceptions.
Recommendations for Safety
The evolution of these attacks presents significant threats to universities, research institutions, government, and media organizations. Maintaining vigilance is crucial, especially when faced with unsolicited meeting invitations from seemingly trustworthy sources.
Security Precautions
Specific advice for individuals in high-risk sectors includes:
- - Verify the identity of senders using trusted social media accounts or known channels.
- - Always check the URLs before inputting sensitive information on sites dealing with confidential data.
- - Enable two-factor authentication (2FA) and monitor for unsolicited requests for authentication codes.
- - Report suspicious communications immediately to your organization’s security team.
CPR continues to monitor these activities and will share new findings as they develop. Their advanced security services, including Harmony Email and Collaboration and Zero Phishing, are designed to detect and block such targeted phishing attacks.
For a detailed look at this spear-phishing attack, refer to CPR's comprehensive report.
About Check Point Research
Check Point Research provides current cyber threat intelligence to customers and the threat intelligence community. The team, comprising over 100 analysts and researchers, collaborates with security vendors, law enforcement, and various CERT organizations to bolster cybersecurity measures effectively. Check Point Software Technologies aims to protect organizations globally through AI-driven cybersecurity solutions.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.