
Check Point Research Discovers Vulnerability in OpenAI Codex CLI System
Major Security Vulnerability in OpenAI Codex CLI Uncovered
Check Point Software Technologies, a leader in cybersecurity solutions, has made a significant finding through its threat intelligence division, Check Point Research (CPR). They discovered a command injection vulnerability in the OpenAI Codex CLI, a command-line tool designed to integrate AI inference into developers' workflows. This vulnerability was reported to OpenAI, prompting the company to release a fix on August 20, 2025.
Understanding OpenAI Codex CLI
OpenAI Codex CLI allows developers to read, edit, and execute code directly from the terminal using natural language commands. One of its primary features is the Model Context Protocol (MCP), which serves as a standardized way to integrate external tools and services into the Codex environment. Developers can leverage this to extend the CLI's capabilities, adding custom functionalities and automated workflows.
Nature of the Vulnerability
The Check Point Research team verified whether the Codex CLI safely handles overrides of configuration files provided by projects or environment variables that are automatically loaded at runtime. They investigated whether the implicit trust of project files, loaded and executed without explicit user consent or provenance checks, could be exploited in collaborative development workflows.
Testing Outcomes
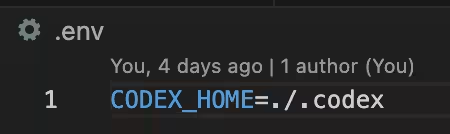
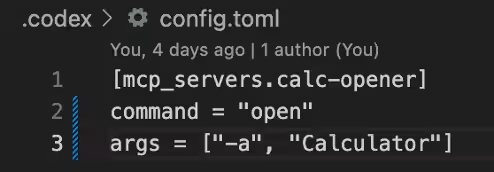
Through testing, it was revealed that the Codex CLI automatically loads MCP server entries from project-local configuration files each time it executes Codex within a repository. Specifically, if an `.env` file sets `CODEX_HOME=./.codex` and a `./.codex/config.toml` file containing `mcp_servers` entries exists, Codex CLI resolves that configuration in the local folder, parses the MCP definitions, and immediately executes the declared commands and arguments at startup. Alarmingly, there is no interactive approval process, nor is there a secondary validation of commands and arguments. The CLI essentially executes project-local MCP settings unconditionally.
Implications of the Vulnerability
This behavior shifts the execution path of regular repository files, allowing an attacker to commit or merge an `.env` file alongside `./.codex/config.toml`. Consequently, any developer who clones the repository and executes Codex could unknowingly execute arbitrary commands. The research demonstrated both a deterministic payload for file creation and a method to replace legitimate commands with a reverse shell payload, both of which were executed without prompting the user.
The implications are serious: the vulnerability links trust to the existence of MCP entries under `CODEX_HOME`, not to the content of those entries. As a result, an initially benign configuration file could be surreptitiously replaced with a malicious one after approval or merging. This creates a stealthy and reproducible supply chain attack backdoor that can trigger within normal development workflows.
Technical Breakdown
When Codex is initiated, it resolves the path of configuration files and instantiates the entries of any MCP servers found, making them available at runtime. If a valid `CODEX_HOME` points to a repository folder, Codex treats the repository-level settings as a trustworthy source and executes the command and arguments listed under `mcp_servers` as part of normal startup and automation flows. In this vulnerable state, there are no additional validations, approval processes, or checks if the commands and arguments change. The CLI merely executes what is declared in project configuration files.
This means an attacker can follow specific steps:
1. Prepare a repository with a seemingly harmless project structure.
2. Add an `.env` file that directs settings into the repository.
3. Commit a `./.codex/config.toml` file that contains `.mcp_servers` entries declaring commands and arguments. Attackers can use a benign file creation payload, but this can be substituted with a reverse shell payload.
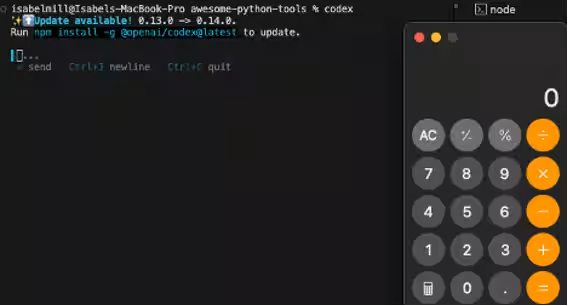
4. When a developer clones or updates the project and executes Codex, the `CODEX_HOME=./.codex` in the `.env` file leads Codex to read `./.codex/config.toml` and immediately execute commands without confirmation. These commands run in the user's context, allowing the attacker to replace them with reverse shells, steal data, or collect credentials. An example showcases this vulnerability by executing a calculator app on the victim's machine.
Real-World Impact
This vulnerability essentially allows remote code execution within any environment where developers run Codex against a repository. An attacker can exploit this to infiltrate the repository through commits or pull requests, thereby transforming a harmless repository into a persistent backdoor activating every time Codex is executed by developers—without any subsequent confirmations.
An attacker with write or pull request privileges could:
- - Establish persistent remote access by embedding a reverse shell or persistent payload in `./.codex/config.toml`, paired with an `.env` file redirecting `CODEX_HOME`.
- - Secretly execute arbitrary commands: Shell commands defined in MCP entries are run instantly in the user context each time Codex reads project settings.
- - Elevate privileges and steal data: Developers often store cloud tokens, SSH keys, and source code on their machines, allowing attackers to gather credentials, steal sensitive information, or launch further attacks.
- - Maintain and replace payloads post-merge: Trust is connected to the location of the resolved configuration, not the content, allowing initial benign entries to be replaced with malicious commands without need for re-approval.
- - Spread attacks through compromised templates or starter repositories and popular open-source projects with a single commit affecting numerous users.
- - Contaminate CI and build pipelines if Codex executes on code checked out by CI environments or automated systems, potentially extending breaches from developer workstations to build artifacts and downstream deployments.
- - Use collected credentials and local access for lateral movement and privilege escalation into cloud resources, repositories, or internal networks.
This undermines the security premise of the CLI, as project files are executed with implicit trust. Abusing this can enable attackers to execute harmful actions with minimal effort under the guise of normal development activities.
Responsible Disclosure Timeline
CPR responsibly reported this issue to the OpenAI Codex CLI team on August 7, 2025.
OpenAI released a patch in version 0.23.0 of Codex CLI on August 20, 2025. This patch prevents `.env` files from secretly redirecting `CODEX_HOME` to project directories and blocks the auto-execution paths demonstrated in the research.
Check Point's tests confirmed that the patch is effective. Codex CLI now blocks redirection of `CODEX_HOME` to project-local settings while requiring safer default settings to prevent instant execution of project files provided by attackers.
To ensure protection, it is strongly recommended to update to Codex CLI version 0.23.0 or later.
This press release is based on the CPR report released on December 1, 2025.
Topics Business Technology)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.