
Check Point Software Discovers Massive Phishing Attack Exploiting Google Classroom
Overview of the Phishing Attack
Check Point Software Technologies, a global leader in cybersecurity solutions, recently published findings detailing a significant phishing campaign exploiting Google Classroom. This online learning platform, trusted by millions of students and educators worldwide, was misused by attackers to send fraudulent emails in a series of organized assaults. Within just a week, the attackers executed five campaigns and sent over 115,000 phishing emails targeting various sectors across 13,500 organizations, impacting regions including Europe, North America, the Middle East, and Asia.
Understanding the Attack Methodology
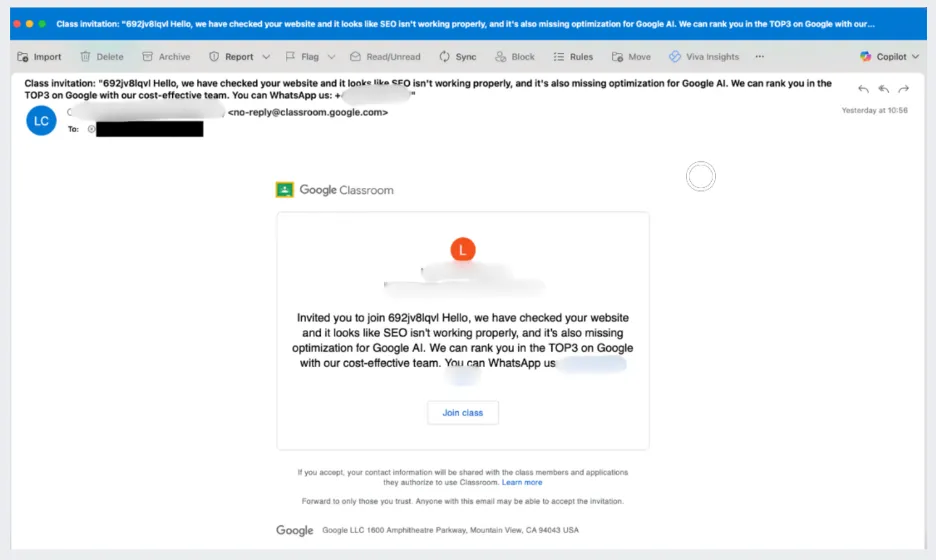
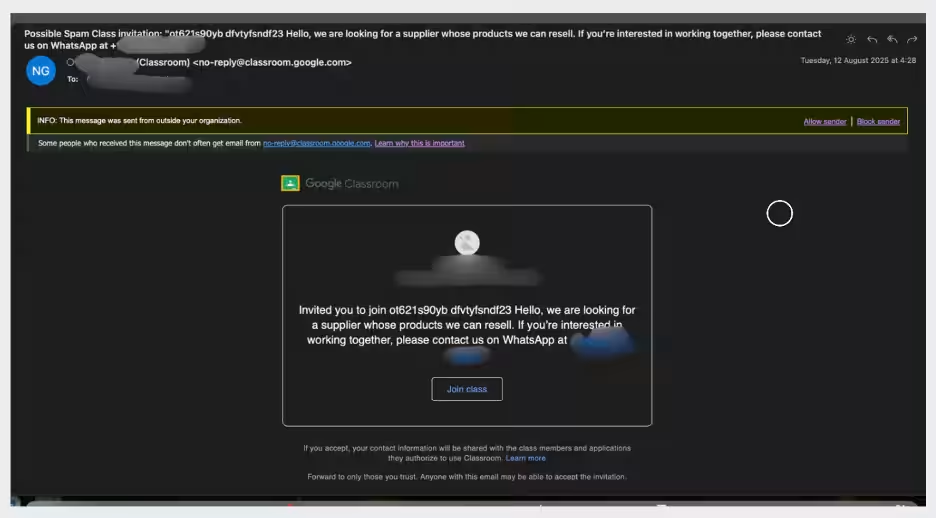
Google Classroom is primarily designed to foster connections between teachers and students through invitations to participate in online classes. The attackers took advantage of this established trust to disseminate fake invitations that included illegitimate commercial offers unrelated to educational activities, such as SEO services and product resale pitches. Each fraudulent email usually instructed recipients to reach out to scammers via WhatsApp, a tactic commonly employed in various fraud schemes.
These impersonations succeed because security systems on the receiving end tend to trust communications that appear as if they originate from legitimate Google services. By hijacking Google Classroom's infrastructure, attackers could bypass traditional security layers and attempt to infiltrate inboxes of over 13,500 organizations before defensive measures were triggered.
Detailed Attack Insights
- - Scale of the Attack: The campaign ran from August 6 to August 12, 2025, sending 115,000 phishing emails.
- - Targets: 13,500 organizations across multiple sectors worldwide.
- - Means: Emails disguised as legitimate Google Classroom invitations with unrelated commercial offers.
- - Call to Action: Recipients were urged to avoid email communication and contact via a WhatsApp phone number.
- - Delivery Method: The attack was executed across five instances, each time exploiting Google Classroom's authenticity to bypass security filters.
Blockage Mechanisms Employed by Check Point
Despite the sophisticated exploitation of reliable infrastructure by the attackers, a majority of these phishing attempts were blocked thanks to Check Point's Harmony Email & Collaboration SmartPhish technology, which automatically detects and mitigates such threats. Additionally, remaining messages that circumvented the initial security measures were prevented from reaching end-users through further security layers.
Importance of Multi-layered Defense
This incident underscores the significance of employing a multi-layered defense strategy. The weaponization of legitimate cloud services by attackers is on the rise, and traditional email gateways alone are insufficient to combat evolving phishing tactics.
Recommended Actions for Organizations
1. User Education: Train employees to exercise caution when receiving invitations, even from familiar platforms, to ensure comprehensive vigilance against potential threats.
2. Advanced Threat Protection: Implement AI-driven threat detection capabilities that analyze not just the sender's reputation but also context and intent.
3. Cloud Application Monitoring: Extend phishing defenses beyond email to cover collaboration apps, messaging platforms, and SaaS services.
4. Social Engineering Countermeasures: Educate staff on the increasing trend of attackers directing victims to unofficial communication channels like WhatsApp.
Conclusion
Attackers will continue seeking innovative methods to exploit legitimate services like Google Classroom to gain trust and circumvent defenses while reaching broader targets. The rapid dissemination of over 115,000 emails within a week highlights how easily digital platforms can be weaponized for fraudulent activities.
Check Point's Harmony Email & Collaboration, rated as a leader and outperformer in the phishing protection sector by the 2025 GigaOm Radar Report, provides essential advanced multi-layered defense to protect organizations, regardless of how cleverly attacks are concealed. This release is based on a blog published on August 25, 2025, US Time.
About Check Point
Check Point Software Technologies (https://www.checkpoint.com/) is a leading provider of digital trust solutions, safeguarding over 100,000 organizations worldwide through AI-driven cybersecurity solutions. With its Infinity Platform and open-garden ecosystem, Check Point achieves top-tier security effectiveness while reducing risk through a prevention-first approach. The platform integrates management across on-premise, cloud, and workspace environments, offering flexibility, simplicity, and scalability to enterprises and service providers. Check Point’s wholly-owned subsidiary in Japan was established on October 1, 1997, and is based in Minato-ku, Tokyo.
Stay Updated:
Legal Disclaimer Regarding Forward-Looking Statements
This press release contains forward-looking statements about future events or our anticipated performance. Factors that could cause actual results to differ from these forward-looking statements include our ability to continue enhancing our platform and solutions, customer acceptance and adoption of both existing and new solutions, the evolving IT security market, competitive pressures, and market, political, economic, or management conditions.
Media Inquiries
For inquiries, please contact:
Check Point Public Relations Office (within NEXT PR LLC)
Tel: 03-4405-9537
Fax: 03-6739-3934
Email: [email protected]
Topics Business Technology)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.