
Check Point Research Uncovers Targeted Cyber Espionage Exploiting Microsoft Zero-Day Vulnerability
Check Point Research Exposes Targeted Cyber Espionage
In a significant finding, Check Point Research (CPR), the threat intelligence division of Check Point Software Technologies (NASDAQ: CHKP), recently revealed an alarming attempt to carry out a cyber attack against a prominent Turkish defense institution. This operation exploited a previously unknown vulnerability within Windows, labeled CVE-2025-33053.
The discovery comes in the wake of CPR's responsible disclosure, prompting Microsoft to release a patch as part of the regular Patch Tuesday updates on June 10, 2025. This zero-day vulnerability was utilized by a known threat group, 'Stealth Falcon', which primarily targets organizations in the Middle East and Africa.
Attack Methodology
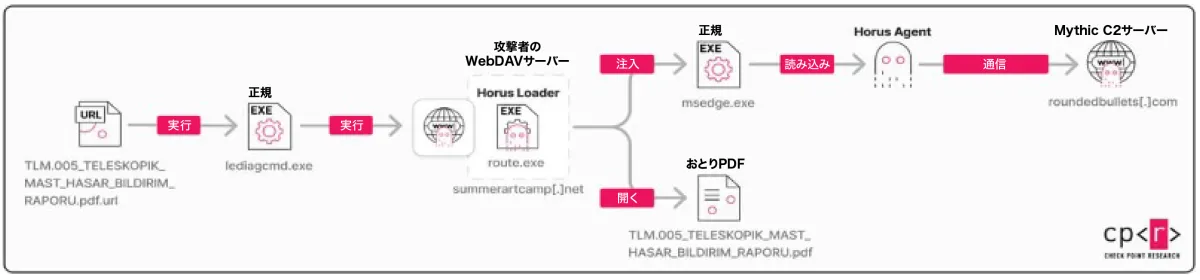
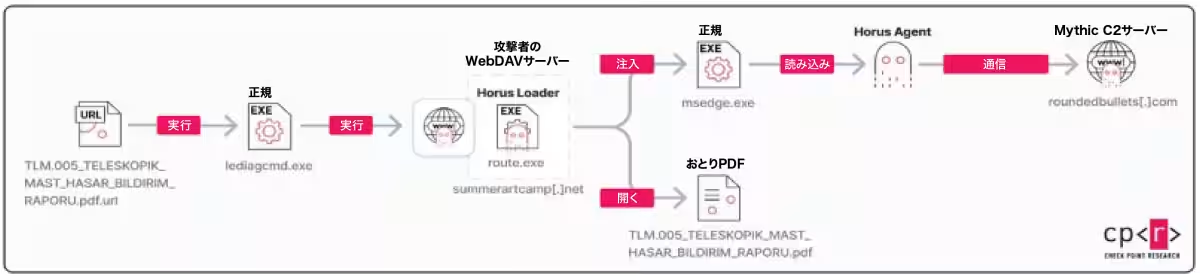
The attack vector began when a disguised .url file was used to covertly trigger malware hosted on a WebDAV server controlled by the attackers. This process involved the exploitation of legitimate Windows tools. The operation employed a sophisticated custom loader and implant designed to avoid detection, interfere with analysis, and selectively operate only on high-value targets.
In March 2025, CPR identified a cyber attack method targeting the Turkish defense organization, utilizing a previously unreported remote code execution flaw in Windows. The attackers managed to execute files from their remote server while stealthily deploying malicious code through legitimate Windows tools. After responsible disclosure to Microsoft, CVE-2025-33053 was assigned to this vulnerability, leading to the issuance of a patch in June.
According to CPR's analysis of the attack's techniques and the infrastructure behind the campaign, it was attributed to 'Stealth Falcon', an established Advanced Persistent Threat (APT) group known for its targeted espionage efforts.
The 'Horus Agent'
The press release elaborated on how Stealth Falcon utilized a custom-built implant named 'Horus Agent', which is part of an extensive toolkit designed for espionage. This malware was specifically engineered to exploit CVE-2025-33053.
A longstanding cyber espionage group, Stealth Falcon has been active since at least 2012, targeting politically and strategically significant organizations across the Middle East and Africa. The group's tactics have evolved but remain focused on government and defense sectors. They are recognized for their use of zero-day exploits, custom malware, and sophisticated delivery mechanisms.
This specific attack commenced with a standard .url file masquerading as a PDF document related to military equipment damage. It is highly probable that this file was distributed through phishing emails, a method previously employed by Stealth Falcon.
Multi-Layer Loader: Horus Loader
Once the malicious shortcut file was executed, the next phase of the attack initiated with Horus Loader. Named after the Egyptian falcon god, Horus Loader was designed for agility and evasion. It can:
- - Remove traces left during the initial infection phase.
- - Evade basic detection mechanisms.
- - Drop and open decoy documents to divert suspicion.
- - Covertly deploy the final spyware payload.
Deployment of Horus Agent
As the victim viewed the decoy documents, the malware operated silently in the background. The deployment of Horus Agent marked one of the most technologically advanced stages of the operation. This custom-built backdoor malware was fashioned for use with Mythic, an open-source command & control (C2) framework popular in red team exercises.
Unlike conventional malware, Horus was developed from the ground up using C++, prioritizing stealth and flexibility. It shares only basic characteristics with existing Mythic agents, ensuring it is neither easily detected nor attributed based on code similarities.
Once installed, Horus Agent connects to C2 servers and begins polling for instructions. While some commands are built-in, Stealth Falcon has developed custom commands focused on stealth and flexibility, allowing for quiet information gathering and minimal detection during payload execution.
Conclusion: Strategic Implications of Zero-Day Attacks
Stealth Falcon continues to adapt, launching potent campaigns that leverage the CVE-2025-33053 zero-day exploit, legitimate tools, multi-layer loaders, and custom-built implants. The crafty abuse of WebDAV and Windows operations illustrates that even minor configuration errors or overlooked features can be weaponized.
Mitigation and Defense
This attack underscores the importance of proactive threat detection, operational visibility, and real-time protection. Organizations in defense, government, and critical infrastructure sectors must recognize that targeted threats remain a continuous concern. Considering the nature of this vulnerability and its relevance to the operation of core Windows APIs, it is likely to affect a wide range of Windows versions.
To determine if your organization's environment has been compromised, it is advisable to inspect logs and monitoring systems for suspicious activity, particularly regarding URL or LNK files in email attachments and unusual WebDAV connections initiated by default Windows processes.
Following the discovery of the vulnerability, Check Point quickly developed and deployed protective measures to safeguard its customers. Their Intrusion Prevention System (IPS), Threat Emulation, and Harmony Endpoint solutions are actively detecting and blocking attempts exploiting this vulnerability. CPR continues to monitor global telemetry to track new activities and provide timely updates as the threat landscape evolves.
For more in-depth insights on Stealth Falcon’s campaigns, refer to CPR’s comprehensive report.
About Check Point Research
Check Point Research is committed to providing the latest cyber threat intelligence to Check Point customers and the threat intelligence community. The team of over 100 analysts and researchers collaborates with security vendors, law enforcement, and CERT organizations to enhance cybersecurity measures.
Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.