
Check Point Research Reports on Active Malware Threats in March 2025
Overview of Cyber Threats in March 2025
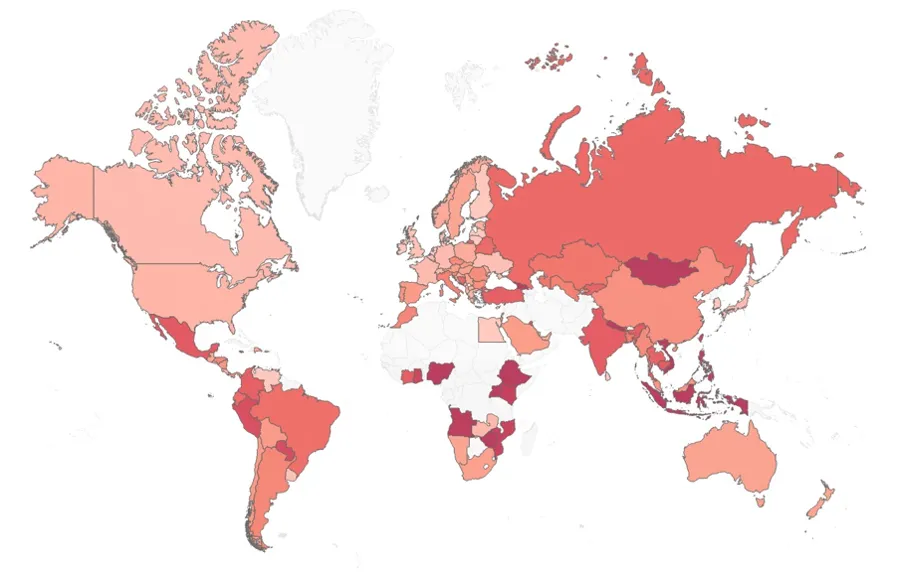
Check Point Research (CPR), the threat intelligence division of Check Point Software Technologies, has released its Global Threat Index for March 2025, revealing that the notorious downloader malware, FakeUpdates, continues to pose a significant risk worldwide. Additionally, ransomware attacks involving RansomHub are gaining momentum, emphasizing growing concerns in the domain of ransomware.
The education and research sectors remain the most targeted by cybercriminals, with both malware and ransomware being primary threats. New infiltration campaigns have been identified, linking FakeUpdates to further ransomware attacks orchestrated by RansomHub. In March, various attack methodologies were prevalent, exploiting infected websites, disreputable Keitaro TDS, and misleading browser update notifications to deceive users.
Analysis of Malware Distribution
FakeUpdates is still the most pervasive malware, with infection tactics including drive-by downloads from compromised sites and tricking users into installing fake browser updates. The attackers have continued to refine their techniques, utilizing obfuscated JavaScript loaders for data theft and command execution, revealing the sophistication of cybercriminals who are leveraging legitimate services like Dropbox and TryCloudflare to evade detection.
A large-scale phishing campaign involving the Lumma Stealer has also been uncovered, impacting over 1,150 companies and more than 7,000 users in North America and Southern Europe. Attackers deployed around 5,000 malicious PDFs on Webflow's CDN, using fake CAPTCHA images to launch PowerShell and deploy malware. This trend of abusing legitimate services is indicative of a new approach by cybercriminals looking to minimize detection.
In Japan, the top active malware families saw notable shifts in rankings from the previous month:
- - Remcos (3.47%) - Observed since 2016, this Remote Access Trojan (RAT) is typically distributed via phishing campaigns and malicious documents, capable of bypassing various Windows security protocols.
- - Androxgh0st (2.23%) - A Python-based malware that scans publicly exposed .env files for credentials associated with services like AWS and Office 365. It targets applications built on the Laravel PHP framework and utilizes botnets to identify Laravel sites for data extraction.
- - FakeUpdates (1.74%) - Initially discovered in 2018, this downloader malware spreads through drive-by downloads and manipulates users into fake updates. It is believed to be related to the Russian hacking group Evil Corp.
Global Malware Landscape
Globally, FakeUpdates maintained its position as the foremost malware in March, impacting around 8% of organizations, followed by Remcos and AgenTesla, both at approximately 3%.
Active Ransomware Groups
According to the data released by ransomware groups operating double-extortion schemes, RansomHub is the most active in March, accounting for 12% of revealed attacks. It is a rebranded version of the ransomware previously known as Knight, emerging on underground forums with ambitious campaigns targeting various systems, including Windows, macOS, and Linux.
Additional active ransomware groups include:
- - Qilin - Known for targeting high-value organizations, including those in the healthcare sector.
- - Akira - First reported in early 2023, focusing on Windows and Linux systems.
Mobile Malware Trends
In the mobile domain, Anubis emerged as the most prevalent malware, with notable successors being Necro and AhMyth. Anubis is an advanced banking Trojan with capabilities to intercept SMS-based OTPs and perform keylogging among others. Its distribution often occurs through infected applications available on the Google Play Store.
Industries Under Attack
In March 2025, education and research sectors continued to be the most attacked industries globally, followed by telecommunications and government/military sectors.
In summary, the cyber threat landscape remains complex and precarious, with Check Point's research shedding light on evolving strategies by cybercriminals. By utilizing real-time data from millions of sources globally, Check Point's ThreatCloud enables organizations to implement robust security protocols against these daunting threats. Organizations can leverage Check Point’s solutions to ensure security against the ever-evolving cyber threats identified in this report.
Topics Consumer Technology)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.