
Unveiling Ink Dragon: A Chinese Cyber Espionage Group's Escalating Global Intrusions
The Rising Threat of Ink Dragon: Insights from Check Point Research
In a detailed report by Check Point Research (CPR), a significant escalation in the activities of Ink Dragon, a Chinese-linked cyber espionage group, has been uncovered. This group has notably extended its reach, carrying out attacks on governmental networks across regions from Asia and South America to Europe. The findings shed light on how Ink Dragon employs sophisticated methods to forge a formidable attack infrastructure by utilizing compromised servers as relay nodes to coordinate operations across multiple countries.
The Scope of Ink Dragon's Operations
The report from CPR highlights that Ink Dragon has been involved in cyber activities targeting not just local entities but expanding its focus to include government networks in Europe. This marked diversification of operations signifies a calculated strategy aimed at infiltrating critical infrastructures worldwide. A key tactic employed by the group involves the use of compromised servers, which act as intermediary nodes facilitating the flow of commands and data, making it challenging to trace the origins of the attack.
Tools of the Trade
Among the advancements in Ink Dragon's toolkit is an evolved variant of the FinalDraft backdoor, designed for persistent access to Microsoft cloud environments. This sophisticated tool allows attackers to blend typical cloud activities with malicious intent, maintaining a low profile while conducting long-term campaigns. Ink Dragon's operations reflect not only a technical prowess but also an understanding of the unique intricacies of cloud infrastructure, effectively disguising their activities amid legitimate business traffic.
Methodology of Attack
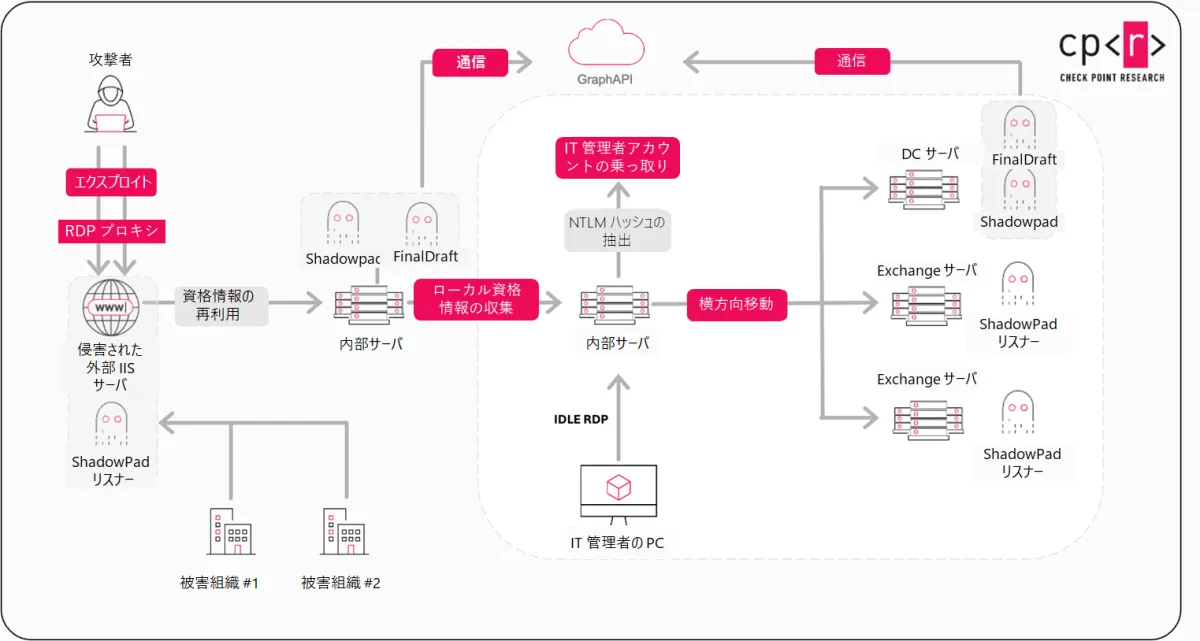
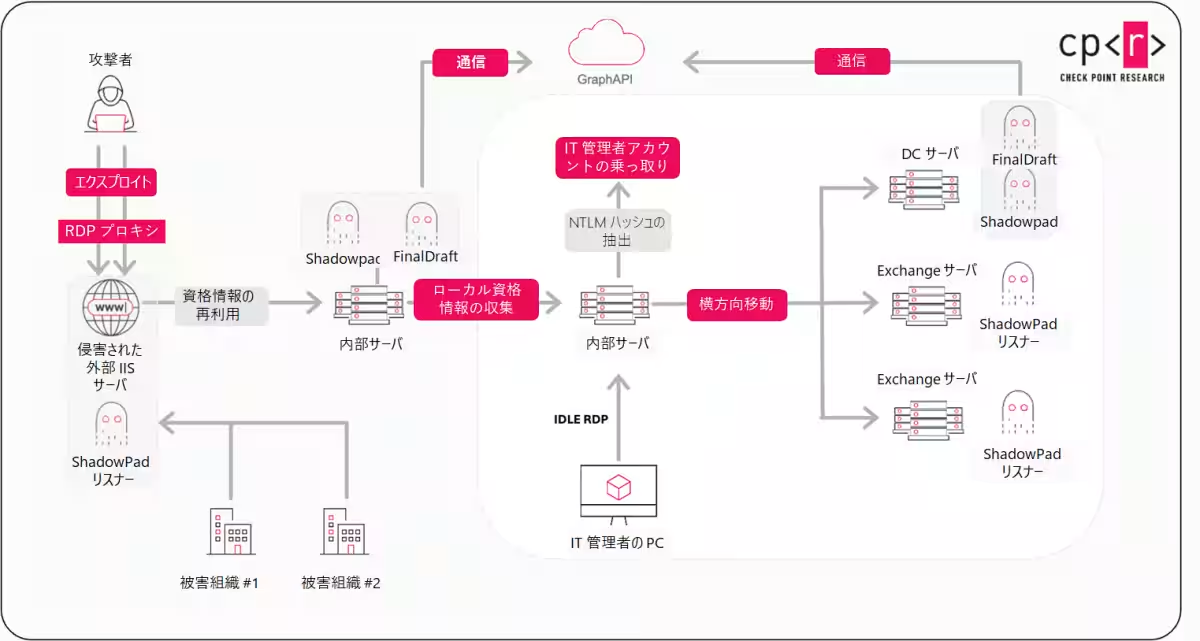
The attack vectors utilized by Ink Dragon begin with exploiting minor configuration vulnerabilities in publicly exposed environments. Many of the investigated intrusion cases stem from simple misconfigurations within Microsoft IIS web servers and SharePoint, enabling hackers to insert malicious code with minimal detection risk. Once inside a network, they meticulously gain access and control over the system’s internal operations, effectively operating under the radar of standard administrative activities.
Phased Approach to Compromise
1. Initial Access: Attackers leverage compromised servers to harvest local credentials and exploit active administrator sessions.
2. Privilege Escalation: They systematically acquire the necessary privileges to maneuver within the network while masquerading as authorized users.
3. Lateral Movement: By using shared service accounts, they access adjacent systems, further expanding their reach within the targeted environment.
This methodical approach enables Ink Dragon to gradually elevate its access without triggering alarms, as their actions often blend seamlessly with regular administrative tasks.
Control and Persistence
Once Ink Dragon achieves domain-level privileges, the group sets about deploying tools intended to maintain long-term access to sensitive systems. This includes installing persistent backdoors, implanting malware on systems that store credentials or confidential data, and creating independent channels for remote access that do not rely on the initial entry point.
Strategic Utilization of Compromised Infrastructure
A distinctive tactic employed by Ink Dragon involves leveraging compromised organizations as infrastructure supporting various attacks. By deploying custom modules on IIS servers, these machines transition into inconspicuous relays, facilitating communication between different compromised environments while obscuring the true source of outbound traffic.
This operational model presents a concerning possibility where a server compromised in one country could relay attack traffic destined for another, thereby complicating defensive measures against such intrusions.
Evolving Threat Tools
The FinalDraft backdoor has been a cornerstone of Ink Dragon's operations due to its adaptability. With the latest updates, this tool has incorporated features that enhance its stealth — for example:
- - Timing Controls: Allowing malware to check in during conventional working hours, mimicking legitimate activities.
- - Data Transfer Capabilities: Enabling background transfer of large data files without detection.
- - Advanced Profiling: Facilitating detailed mapping of the compromised systems.
These enhancements reflect a stark commitment by Ink Dragon to ensure quiet, sustained operations that evade detection.
Overlap with Other Threat Groups
The research by CPR has also revealed concurrent activities by another threat actor known as RudePanda. Despite the apparent lack of collaboration between the two, their attacks target the same government networks, capitalizing on similar vulnerabilities from publicly exposed servers. This overlapping presence emphasizes the risk a single unpatched vulnerability can pose, attracting multiple advanced threat actors who can simultaneously exploit the same environment.
Conclusion and Recommendations
The activities of Ink Dragon, as documented by Check Point Research, highlight a worrying evolution in cyber tactics—transforming compromised servers into an expansive communication network. This strategy not only fortifies Ink Dragon’s resilience but allows it to blend with everyday web activities, complicating the detection of threats. Eli Smadja, CPR’s group manager notes, “Ink Dragon is not just a threat that breaches networks; it covertly reshapes compromised environments into parts of a global C2 network.” Due to the extensive nature of such threats, a singular focus on endpoint remediation is insufficient. A holistic approach that identifies and dismantles the entire relay chain is essential to combat this evolving threat landscape.
Topics General Business)









【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.