

Unlocking the Power of Keycloak: A Comprehensive Guide to Authentication and Authorization with Version 2
Introduction to the Second Edition of Keycloak
In April 2025, Ric Telecom Co., Ltd. will release the much-anticipated second edition of Introduction to Authentication and Authorization: Keycloak. This updated edition is fully compatible with Quarkus and offers insights into the newly refreshed architecture of the open-source security system, Keycloak, which has been a cornerstone for hundreds of web-based applications
What is Keycloak?
Keycloak is an open-source software (OSS) system designed to integrate authentication and authorization functionalities seamlessly into web applications. It enables developers to manage user authentication effortlessly while focusing on the core aspects of their software development.
With the advent of this second edition, readers will gain knowledge about Keycloak's latest architecture that has shifted from WildFly to Quarkus. In a world increasingly dependent on digital security, Keycloak has become crucial not only for mundane applications but also for significant events and infrastructure that bolster our daily lives.
A Must-Read for Software Engineers
This book is a treasure trove of practical information, crafted specifically for software technicians and developers interested in bolstering their understanding and application of Keycloak. Covering everything from introduction to implementation, it is considered an essential read in the field of software technology.
Book Overview
- - Title: Introduction to Authentication and Authorization: Keycloak (Second Edition)
- - Authors: Yuichi Nakamura, Hiroyuki Wada, Kohei Tamura, Yoshiyuki Tabata, Takashi Aoyagi, Wataru Okuura
- - Format: B5 Variant
- - Pages: 496
- - Price: ¥4,840 (Tax included)
- - ISBN: 978-4-86594-436-5
- - Publication: April 2025
- - Publisher: Ric Telecom Co., Ltd.
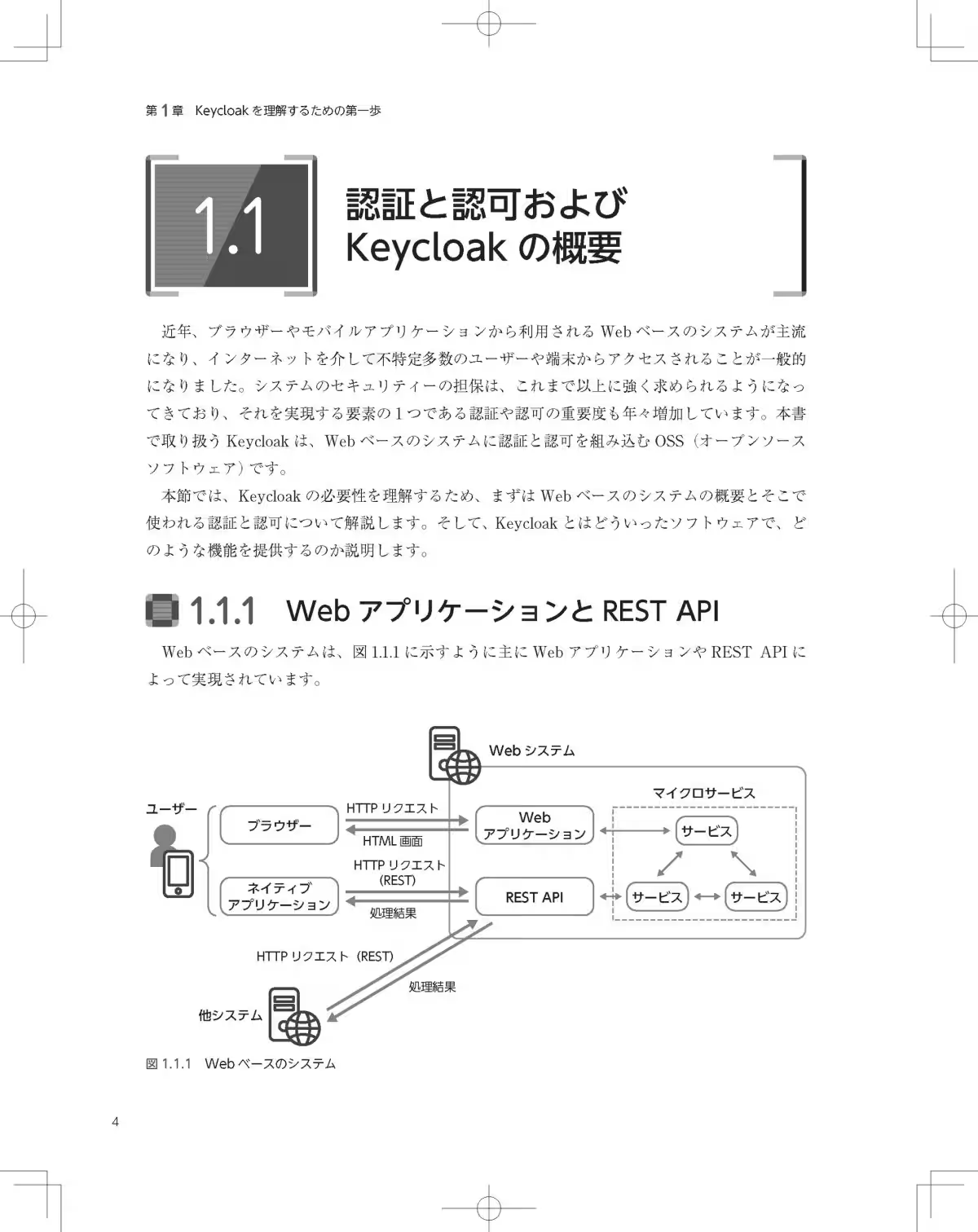
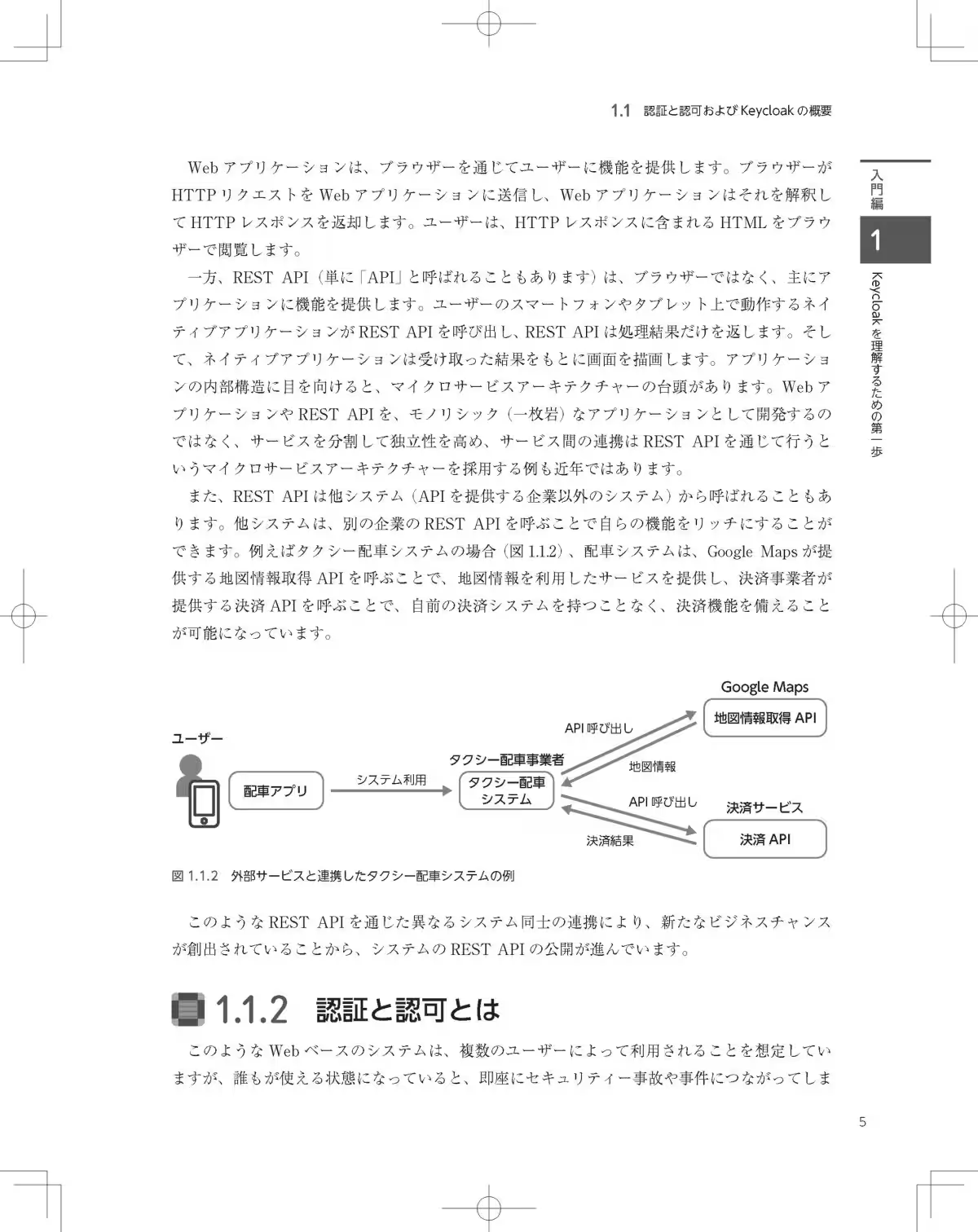
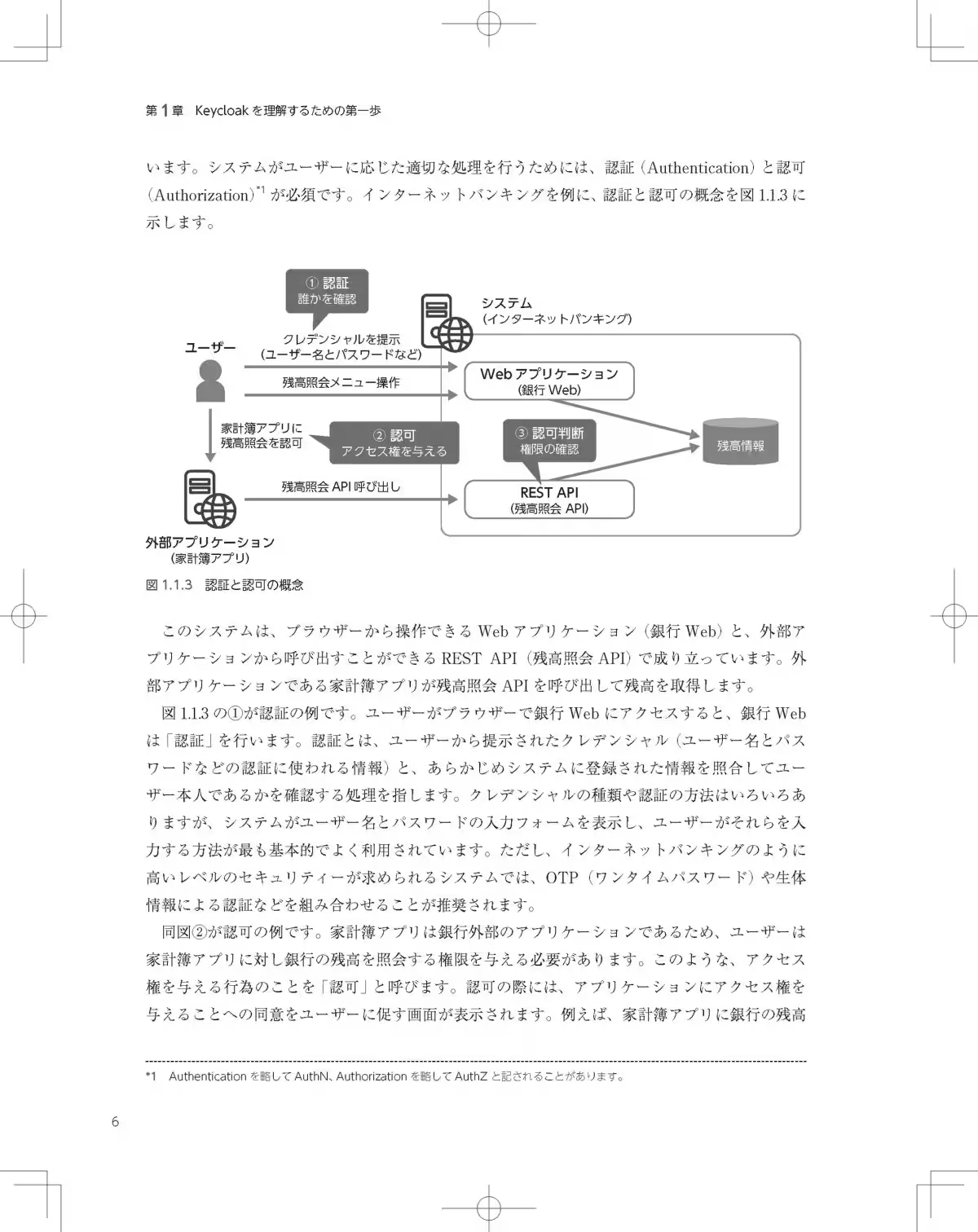
The book is structured into three main components: basic, practical, and advanced topics, ensuring that readers can progress through the material in a structured manner.
Target Audience
The book is designed for:
- - System planners and designers focusing on authentication
- - Operators involved in designing and constructing authentication infrastructures
- - Application developers considering methods for implementing authentication and authorization
- - Individuals interested in constructing authentication and authorization systems using OSS.
Detailed Content Structure
Basic Section
- - Understanding Keycloak
- - Fundamental Knowledge of OAuth and OIDC
- - Basics of Single Sign-On (SSO)
Practical Section
- - Implementing API Authorization following OAuth
- - Realizing Single Sign-On (SSO)
- - Utilizing Various Authentication Methods
Advanced Section
- - Customizing Keycloak
- - Non-functional Considerations in Keycloak
By reading through each section, one can harness their understanding of Keycloak while tackling real-world applications and scenarios, preparing them for real systems deployment.
Authors’ Backgrounds
The authors boast extensive experience in the field of authentication and authorization, having contributed to OSS projects and possessing rich backgrounds in consultancy and system development. Their expertise lends credibility to the book, making it both a resource and a guide for aspiring developers.
For those eager to delve deeper into authentication and authorization systems, Introduction to Authentication and Authorization: Keycloak (Second Edition) serves as the perfect kickoff. Readers can find further information at Ric Telecom's official book site here and purchase through Amazon here.



Topics Other)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.