
Check Point Research Warns About Large-Scale Phishing Attack Targeting Customers
Urgent Warning: Major Phishing Campaign Discovered
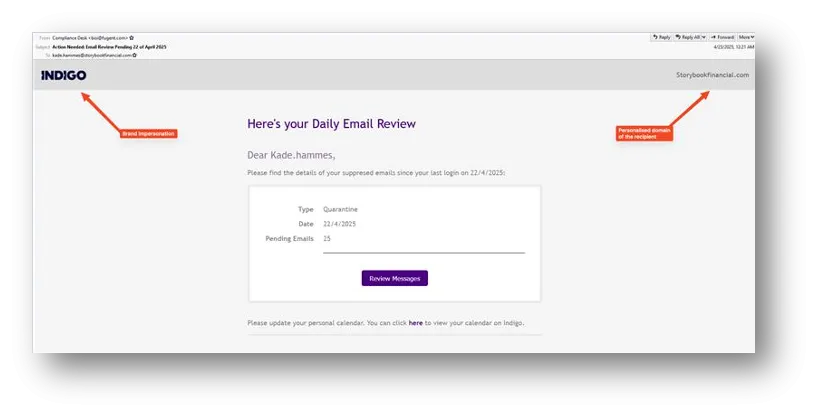
Check Point Research, the threat intelligence branch of Check Point Software Technologies, recently uncovered a large phishing campaign that has targeted more than 6,000 customers worldwide. Over 32,000 fraudulent emails were sent out, masquerading as quarantine notifications, with the primary goal of tricking users into revealing their login information through a fake login page.
Overview of the Attack
The phishing emails originated from compromised accounts associated with three different domains. Each email was carefully crafted to convey a sense of urgency and legitimacy. Here are some examples of the subject lines used:
- - "Email Sent to Quarantine – Review Needed"
- - "Email Delivery Delayed – Retry Scheduled"
- - "Action Needed: Email Review Pending"
The recipients were prompted to click on links embedded in the email content to view their supposed pending messages. This action led them to a fraudulent login page specifically designed to steal their credentials. By leveraging the familiar format of quarantine notifications and stressing urgency, the attackers effectively coerced users into immediate action.
Geographic Targeting
The phishing campaign primarily focused on customers in North America, with approximately 90% of the victims located in Canada and the United States. The remaining 10% of affected customers were from Europe and Australia, indicating a targeted approach aimed at regions where trust in email communications is typically high.
Recommendations and Precautions
This phishing campaign serves as a stark reminder of the need for vigilance, especially when it comes to urgent email notifications. Users should always verify the sender's address and refrain from clicking on links from unknown or suspicious sources. Here are some recommended security measures:
- - Employee Training: Conduct regular training sessions for employees to help them recognize phishing tactics and suspicious emails.
- - Implement Multi-Factor Authentication (MFA): Adding an extra layer of security through MFA can prevent unauthorized access, even if login credentials are compromised.
- - Utilize Email Filtering: Invest in advanced email filtering solutions that can detect and block phishing attempts before they reach user inboxes.
- - Regularly Update Security Protocols: Keeping security measures up to date is crucial to staying ahead of new threats.
For further information, please reach out to Check Point representatives or explore the demo of their email security products available online.
About Check Point Research
Check Point Research provides vital cyber threat intelligence to Check Point customers and the broader threat intelligence community. Their analysts and researchers collect and analyze global data on cyberattacks stored in Check Point’s ThreatCloud AI, deterring hackers while enhancing the product protection features. With over 100 analysts and researchers, the team collaborates with security vendors, law enforcement agencies, and various CERT organizations to strengthen cybersecurity measures across sectors.
About Check Point Software Technologies
As a leading provider of AI-driven, cloud-based cybersecurity solutions, Check Point Software Technologies protects over 100,000 organizations globally. Through its Infinity Platform, Check Point enhances cybersecurity effectiveness and accuracy, enabling proactive defense and quicker response to threats. The comprehensive structure of the Infinity Platform includes features for employee protection (Check Point Harmony), cloud protection (Check Point CloudGuard), network protection (Check Point Quantum), and collaborative security operations (Check Point Infinity Core Services). The wholly owned subsidiary of Check Point, Check Point Software Technologies KK, was established in Tokyo on October 1, 1997.
For more insights, check out their blogs on Check Point Blog and Check Point Research Blog. You can also find them on social media platforms like YouTube, LinkedIn, Twitter, and Facebook.
Topics Consumer Technology)










【About Using Articles】
You can freely use the title and article content by linking to the page where the article is posted.
※ Images cannot be used.
【About Links】
Links are free to use.